Windows权限提升篇&溢出漏洞&土豆家族&通杀全系&补丁对比&EXP筛选
Web到Win-系统提权-人工操作
如果提权中无法执行命令的话,可以尝试上传cmd.exe到可读写目录再调用
优点:解决实时更新不集成的EXP
缺点:操作繁琐,需要各种复现调试
解决工具或插件无法实时更新,又或者集成较少面对复杂情况下人工操作更适合
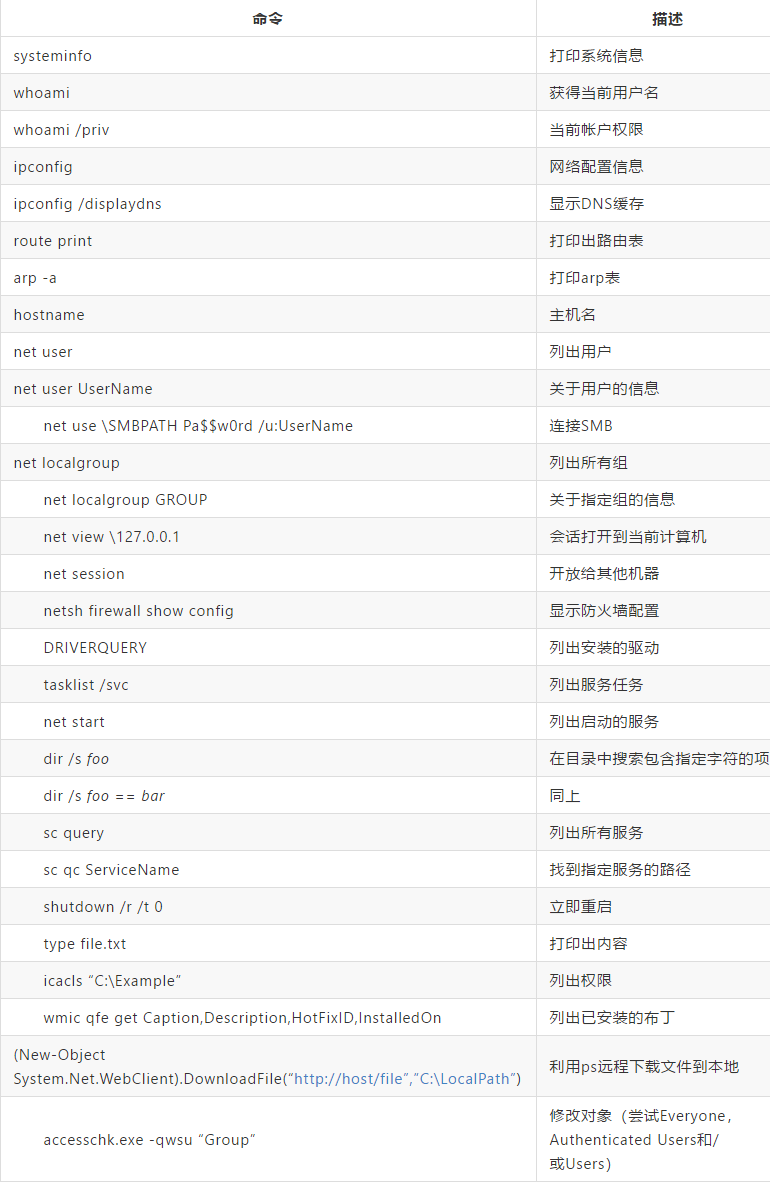
1、信息收集
参考常见命令(见上图)
2、补丁筛选
https://i.hacking8.com/tiquan
https://github.com/bitsadmin/wesng
python wes.py systeminfo.txt --color
python wes.py systeminfo.txt --color -i "Elevation of Privilege" ---只需要提权漏洞
3、EXP获取执行
KernelHub 针对常用溢出编号指定找EXP
Poc-in-Github 针对年份及编号指定找EXP
exploitdb 针对类型及关键说明指定找EXP
https://github.com/Ascotbe/Kernelhub
https://github.com/nomi-sec/PoC-in-GitHub
https://gitlab.com/exploit-database/exploitdb
#Web到Win-系统提权-土豆家族
https://mp.weixin.qq.com/s/OW4ybuqtErh_ovkTWLSr8w
土豆(potato)提权通常用在我们获取WEB/数据库权限的时候,
可以将低权限的服务用户提升为“NT AUTHORITY\SYSTEM”特权。
1、Test in:Windows 10/11(1809/21H2)
2、Test in:Windows Server 2019 Datacenter(1809)
3、Test in:Windows Server 2022 Datacenter(21H2)
SweetPotato OK
RoguePotato
BadPotato OK
EfsPotato OK
GodPotato OK
PetitPotato OK
MultiPotato
CandyPotato
RasmanPotato OK
CoercedPotato
JuicyPotatoNG
PrintNotifyPotato OK
GodPotato
https://github.com/BeichenDream/GodPotato
SweetPotato
https://github.com/CCob/SweetPotato
RoguePotato
https://github.com/antonioCoco/RoguePotato
BadPotato
https://github.com/BeichenDream/BadPotato
EfsPotato
https://github.com/zcgonvh/EfsPotato
MultiPotato
https://github.com/S3cur3Th1sSh1t/MultiPotato
CandyPotato
https://github.com/klezVirus/CandyPotato
RasmanPotato
https://github.com/crisprss/RasmanPotato
PetitPotato
https://github.com/wh0amitz/PetitPotato
JuicyPotatoNG
https://github.com/antonioCoco/JuicyPotatoNG
PrintNotifyPotato
https://github.com/BeichenDream/PrintNotifyPotato
CoercedPotato
https://github.com/Prepouce/CoercedPotato